Certificationmonitor is a free high quality blog that offers all exam dumps from pass4itsure experts. The latest effective 131 CompTIA
security+ sy0-401 exam dumps Practice test and free sharing of sy0-401 pdf, we keep an eye on the latest content to ensure that
all questions and answers are up to date. Free content allows you to progress and enhance your abilities, and if you want to easily
pass the exam to get a sy0-401 exam certificate, please select the full https://www.pass4itsure.com/sy0-401.html PDF + VCE
[PDF] Free CompTIA Security+ SY0-401 dumps download from Google Drive:
https://drive.google.com/open?id=1fNUvuARTsqEpjU2G_fxVaZCoDDWhG1sd
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
CompTIA Security+ Certification:https://certification.comptia.org/certifications/security
Pass4itsure offers the latest CompTIA Security+ SY0-401 practice test free of charge (141Q&As)
QUESTION 1
Ann is the data owner of financial records for a company. She has requested that she have the ability to assign read and write privileges to her folders. The network administrator is tasked with setting up the initial access control system and
handing Ann’s administrative capabilities. Which of the following systems should be deployed?
A. Role-based
B. Mandatory
C. Discretionary
D. Rule-based
Correct Answer: C
QUESTION 2
A password history value of three means which of the following?
A. Three different passwords are used before one can be reused.
B. A password cannot be reused once changed for three years.
C. After three hours a password must be re-entered to continue.
D. The server stores passwords in the database for three days.
Correct Answer: A
QUESTION 3
A security administrator has installed a new KDC for the corporate environment. Which of the following authentication protocols is the security administrator planning to implement across the organization?
A. LDAP
B. RADIUS
C. Kerberos
D. XTACACS
Correct Answer: C
QUESTION 4
A system administrator is using a packet sniffer to troubleshoot remote authentication. The administrator detects a device trying to communicate to TCP port 49. Which of the following authentication methods is MOST likely being attempted?
A. RADIUS
B. TACACS+
C. Kerberos
D. LDAP
Correct Answer: B
QUESTION 5
Which of the following authentication services requires the use of a ticket-granting ticket (TGT) server in order to complete the authentication process?
A. TACACS+
B. Secure LDAP
C. RADIUS
D. Kerberos
Correct Answer: D
QUESTION 6
An organization has introduced token-based authentication to system administrators due to risk of password compromise. The tokens have a set of numbers that automatically change every 30 seconds. Which of the following type of
authentication mechanism is this?
A. TOTP
B. Smart card
C. CHAP
D. HOTP
Correct Answer: A
QUESTION 7
The security department has implemented a new laptop encryption product in the environment. The product requires one user name and password at the time of boot up and also another password after the operating system has finished
loading. This setup is using which of the following authentication types?
A. Two-factor authentication
B. Single sign-on
C. Multifactor authentication
D. Single factor authentication
Correct Answer: D
QUESTION 8
A company hired Joe, an accountant. The IT administrator will need to create a new account for
Joe. The company uses groups for ease of management and administration of user accounts.
Joe will need network access to all directories, folders and files within the accounting department.
Which of the following configurations will meet the requirements?
A. Create a user account and assign the user account to the accounting group.
B. Create an account with role-based access control for accounting.
C. Create a user account with password reset and notify Joe of the account creation.
D. Create two accounts: a user account and an account with full network administration rights.
Correct Answer: B
QUESTION 9
Which of the following access controls enforces permissions based on data labeling at specific levels?
A. Mandatory access control
B. Separation of duties access control
C. Discretionary access control
D. Role based access control
Correct Answer: A
QUESTION 10
A system administrator needs to ensure that certain departments have more restrictive controls to their shared folders than other departments. Which of the following security controls would be implemented to restrict those departments?
A. User assigned privileges
B. Password disablement
C. Multiple account creation
D. Group based privileges
Correct Answer: D
QUESTION 11
Ann was reviewing her company’s event logs and observed several instances of GUEST accessing the company print server, file server, and archive database. As she continued to investigate, Ann noticed that it seemed to happen at random
intervals throughout the day, but mostly after the weekly automated patching and often logging in at the same time. Which of the following would BEST mitigate this issue?
A. Enabling time of day restrictions
B. Disabling unnecessary services
C. Disabling unnecessary accounts
D. Rogue machine detection
Correct Answer: C
QUESTION 12
An administrator implements SELinux on a production web server. After implementing this, the web server no longer serves up files from users’ home directories. To rectify this, the administrator creates a new policy as the root user. This is
an example of which of the following? (Select TWO).A. Enforcing SELinux in the OS kernel is role-based access control
B. Enforcing SELinux in the OS kernel is rule-based access control
C. The policy added by the root user is mandatory access control
D. Enforcing SELinux in the OS kernel is mandatory access control
E. The policy added by the root user is role-based access control
F. The policy added by the root user is rule-based access control
Correct Answer: DF
QUESTION 13
Jane, a security administrator, has been tasked with explaining authentication services to the company’s management team. The company runs an active directory infrastructure. Which of the following solutions BEST relates to the host
authentication protocol within the company’s environment?
A. Kerberos
B. Least privilege
C. TACACS+
D. LDAP
Correct Answer: A
QUESTION 14
Which of the following is an example of multifactor authentication?
A. Credit card and PIN
B. Username and password
C. Password and PIN
D. Fingerprint and retina scan
Correct Answer: A
QUESTION 15
Which of the following should be used to authenticate and log connections from wireless users connecting with EAP-TLS?
A. Kerberos
B. LDAP
C. SAML
D. RADIUS
Correct Answer: D
QUESTION 16
Which of the following authentication services uses a ticket granting system to provide access?
A. RADIUS
B. LDAP
C. TACACS+
D. Kerberos
Correct Answer: D
QUESTION 17
Which of the following was based on a previous X.500 specification and allows either unencrypted authentication or encrypted authentication through the use of TLS?
A. Kerberos
B. TACACS+
C. RADIUS
D. LDAP
Correct Answer: D
QUESTION 18
Which of the following types of security services are used to support authentication for remote users and devices?
A. Biometrics
B. HSM
C. RADIUS
D. TACACS
Correct Answer: C
QUESTION 19
A hacker has discovered a simple way to disrupt business for the day in a small company which relies on staff working remotely. In a matter of minutes the hacker was able to deny remotely working staff access to company systems with a
script. Which of the following security controls is the hacker exploiting?
A. DoS
B. Account lockout
C. Password recovery
D. Password complexity
Correct Answer: B
QUESTION 20
A technician is reviewing the logical access control method an organization uses. One of the senior managers requests that the technician prevent staff members from logging on during nonworking days. Which of the following should the
technician implement to meet managements request?
A. Enforce Kerberos
B. Deploy smart cards
C. Time of day restrictions
D. Access control lists
Correct Answer: C
QUESTION 21
Which of the following is the BEST reason for placing a password lock on a mobile device?
A. Prevents an unauthorized user from accessing owner’s data
B. Enables remote wipe capabilities
C. Stops an unauthorized user from using the device again
D. Prevents an unauthorized user from making phone calls
Correct Answer: A
QUESTION 22
Which of the following is mainly used for remote access into the network?
A. XTACACS
B. TACACS+
C. Kerberos
D. RADIUS
Correct Answer: D
QUESTION 23
Which of the following protocols uses TCP instead of UDP and is incompatible with all previous versions?
A. TACACS
B. XTACACS
C. RADIUS
D. TACACS+
Correct Answer: D
QUESTION 24
The system administrator is tasked with changing the administrator password across all 2000 computers in the organization. Which of the following should the system administrator implement to accomplish this task?A. A security group
B. A group policy
C. Key escrow
D. Certificate revocation
Correct Answer: B
QUESTION 25
The IT department has setup a website with a series of questions to allow end users to reset their own accounts. Which of the following account management practices does this help?
A. Account Disablements
B. Password Expiration
C. Password Complexity
D. Password Recovery
Correct Answer: D
QUESTION 26
Use of group accounts should be minimized to ensure which of the following?
A. Password security
B. Regular auditing
C. Baseline management
D. Individual accountability
Correct Answer: D
QUESTION 27
One of the most basic ways to protect the confidentiality of data on a laptop in the event the device is physically stolen is to implement which of the following?
A. File level encryption with alphanumeric passwords
B. Biometric authentication and cloud storage
C. Whole disk encryption with two-factor authentication
D. BIOS passwords and two-factor authentication
Correct Answer: C
QUESTION 28
A security analyst implemented group-based privileges within the company active directory. Which of the following account management techniques should be undertaken regularly to ensure least privilege principles?
A. Leverage role-based access controls.
B. Perform user group clean-up.
C. Verify smart card access controls.
D. Verify SHA-256 for password hashes.
Correct Answer: B
QUESTION 29
An internal auditing team would like to strengthen the password policy to support special characters. Which of the following types of password controls would achieve this goal?
A. Add reverse encryption
B. Password complexity
C. Increase password length
D. Allow single sign on
Correct Answer: B
QUESTION 30
Which of the following is best practice to put at the end of an ACL?
A. Implicit deny
B. Time of day restrictions
C. Implicit allow
D. SNMP string
Correct Answer: A
QUESTION 31
Ann, a security administrator, wishes to replace their RADIUS authentication with a more secure protocol, which can utilize EAP. Which of the following would BEST fit her objective?
A. CHAP
B. SAML
C. Kerberos
D. Diameter
Correct Answer: D
QUESTION 32
Jane, a security administrator, needs to implement a secure wireless authentication method that uses a remote RADIUS server for authentication.
Which of the following is an authentication method Jane should use?
A. WPA2-PSK
B. WEP-PSK
C. CCMP
D. LEAP
Correct Answer: D
QUESTION 33
A network administrator is configuring access control for the sales department which has high employee turnover. Which of the following is BEST suited when assigning user rights to individuals in the sales department?
A. Time of day restrictions
B. Group based privileges
C. User assigned privileges
D. Domain admin restrictions
Correct Answer: B
QUESTION 34
A security technician is working with the network firewall team to implement access controls at the company’s demarc as part of the initiation of configuration management processes. One of the network technicians asks the security
technician to explain the access control type found in a firewall. With which of the following should the security technician respond?
A. Rule based access control
B. Role based access control
C. Discretionary access control
D. Mandatory access control
Correct Answer: A
QUESTION 35
A security administrator has been tasked to ensure access to all network equipment is controlled by a central server such as TACACS+. This type of implementation supports which of the following risk mitigation strategies?
A. User rights and permissions review
B. Change management
C. Data loss prevention
D. Implement procedures to prevent data theft
Correct Answer: A
QUESTION 36
Which of the following is an XML based open standard used in the exchange of authentication and authorization information between different parties?
A. LDAP
B. SAMLC. TACACS+
D. Kerberos
Correct Answer: B
QUESTION 37
The security manager wants to unify the storage of credential, phone numbers, office numbers, and address information into one system. Which of the following is a system that will support the requirement on its own?
A. LDAP
B. SAML
C. TACACS
D. RADIUS
Correct Answer: A
QUESTION 38
LDAP and Kerberos are commonly used for which of the following?
A. To perform queries on a directory service
B. To store usernames and passwords for Federated Identity
C. To sign SSL wildcard certificates for subdomains
D. To utilize single sign-on capabilities
Correct Answer: D
QUESTION 39
A user reports being unable to access a file on a network share. The security administrator determines that the file is marked as confidential and that the user does not have the appropriate access level for that file. Which of the following is
being implemented?
A. Mandatory access control
B. Discretionary access control
C. Rule based access control
D. Role based access control
Correct Answer: A
QUESTION 40
Users report that they are unable to access network printing services. The security technician checks the router access list and sees that web, email, and secure shell are allowed. Which of the following is blocking network printing?
A. Port security
B. Flood guards
C. Loop protection
D. Implicit deny
Correct Answer: D
QUESTION 41
Ann has recently transferred from the payroll department to engineering. While browsing file shares, Ann notices she can access the payroll status and pay rates of her new coworkers. Which of the following could prevent this scenario from
occurring?
A. Credential management
B. Continuous monitoring
C. Separation of duties
D. User access reviews
Correct Answer: D
QUESTION 42
A security administrator is tackling issues related to authenticating users at a remote site. There have been a large number of security incidents that resulted from either tailgating or impersonation of authorized users with valid credentials. The
security administrator has been told to implement multifactor authentication in order to control facility access. To secure access to the remote facility, which of the following could be implemented without increasing the amount of space
required at the entrance?
A. MOTD challenge and PIN pad
B. Retina scanner and fingerprint reader
C. Voice recognition and one-time PIN token
D. One-time PIN token and proximity reader
Correct Answer: C
QUESTION 43
A security administrator wants to check user password complexity. Which of the following is the
BEST tool to use?
A. Password history
B. Password logging
C. Password cracker
D. Password hashing
Correct Answer: C
QUESTION 44
Which of the following controls mitigates the risk of Matt, an attacker, gaining access to a company network by using a former employee’s credential?
A. Account expiration
B. Password complexity
C. Account lockout
D. Dual factor authentication
Correct Answer: A
QUESTION 45
An organizations’ security policy requires that users change passwords every 30 days. After a security audit, it was determined that users were recycling previously used passwords. Which of the following password enforcement policies
would have mitigated this issue?
A. Password history
B. Password complexity
C. Password length
D. Password expiration
Correct Answer: A
QUESTION 46
The systems administrator notices that many employees are using passwords that can be easily guessed or are susceptible to brute force attacks. Which of the following would BEST mitigate this risk?
A. Enforce password rules requiring complexity.
B. Shorten the maximum life of account passwords.
C. Increase the minimum password length.
D. Enforce account lockout policies.
Correct Answer: A
QUESTION 47
When Ann an employee returns to work and logs into her workstation she notices that, several desktop configuration settings have changed. Upon a review of the CCTV logs, it is determined that someone logged into Ann’s workstation.
Which of the following could have prevented this from happening?
A. Password complexity policy
B. User access reviews
C. Shared account prohibition policy
D. User assigned permissions policy
Correct Answer: A
QUESTION 48
Which of the following allows a network administrator to implement an access control policy based on individual user characteristics and NOT on job function?A. Attributes based
B. Implicit deny
C. Role based
D. Rule based
Correct Answer: A
QUESTION 49
Which of the following presents the STRONGEST access control?
A. MAC
B. TACACS
C. DAC
D. RBAC
Correct Answer: A
QUESTION 50
Ann is a member of the Sales group. She needs to collaborate with Joe, a member of the IT group, to edit a file. Currently, the file has the following permissions:
Ann:read/write
Sales Group:read
IT Group:no access
If a discretionary access control list is in place for the files owned by Ann, which of the following would be the BEST way to share the file with Joe?
A. Add Joe to the Sales group.
B. Have the system administrator give Joe full access to the file.
C. Give Joe the appropriate access to the file directly.
D. Remove Joe from the IT group and add him to the Sales group.
Correct Answer: C
QUESTION 51
A security administrator implements access controls based on the security classification of the data and need-to-know information. Which of the following BEST describes this level of access control?
A. Implicit deny
B. Role-based Access Control
C. Mandatory Access Controls
D. Least privilege
Correct Answer: C
QUESTION 52
A group policy requires users in an organization to use strong passwords that must be changed every 15 days. Joe and Ann were hired 16 days ago. When Joe logs into the network, he is prompted to change his password; when Ann logs
into the network, she is not prompted to change her password. Which of the following BEST explains why Ann is not required to change her password?
A. Ann’s user account has administrator privileges.
B. Joe’s user account was not added to the group policy.
C. Ann’s user account was not added to the group policy.
D. Joe’s user account was inadvertently disabled and must be re-created.
Correct Answer: C
QUESTION 53
Which of the following authentication services should be replaced with a more secure alternative?
A. RADIUS
B. TACACS
C. TACACS+
D. XTACACS
Correct Answer: B
QUESTION 54
Which of the following security concepts can prevent a user from logging on from home during the weekends?
A. Time of day restrictions
B. Multifactor authentication
C. Implicit deny
D. Common access card
Correct Answer: A
QUESTION 55
Several employee accounts appear to have been cracked by an attacker. Which of the following should the security administrator implement to mitigate password cracking attacks? (Select TWO).
A. Increase password complexity
B. Deploy an IDS to capture suspicious logins
C. Implement password history
D. Implement monitoring of logins
E. Implement password expiration
F. Increase password length
Correct Answer: AF
QUESTION 56
A security technician has been asked to recommend an authentication mechanism that will allow users to authenticate using a password that will only be valid for a predefined time interval. Which of the following should the security technician
recommend?
A. CHAP
B. TOTP
C. HOTP
D. PAP
Correct Answer: B
QUESTION 57
Privilege creep among long-term employees can be mitigated by which of the following procedures?
A. User permission reviews
B. Mandatory vacations
C. Separation of duties
D. Job function rotation
Correct Answer: A
QUESTION 58
Human Resources suspect an employee is accessing the employee salary database. The administrator is asked to find out who it is. In order to complete this task, which of the following is a security control that should be in place?
A. Shared accounts should be prohibited.
B. Account lockout should be enabled
C. Privileges should be assigned to groups rather than individuals
D. Time of day restrictions should be in use
Correct Answer: A
QUESTION 59
Which of the following is a BEST practice when dealing with user accounts that will only need to be active for a limited time period?
A. When creating the account, set the account to not remember password history.
B. When creating the account, set an expiration date on the account.
C. When creating the account, set a password expiration date on the account.D. When creating the account, set the account to have time of day restrictions.
Correct Answer: B
QUESTION 60
A company requires that a user’s credentials include providing something they know and something they are in order to gain access to the network. Which of the following types of authentication is being described?
A. Biometrics
B. Kerberos
C. Token
D. Two-factor
Correct Answer: D
QUESTION 61
An administrator discovers that many users have used their same passwords for years even though the network requires that the passwords be changed every six weeks. Which of the following, when used together, would BEST prevent
users from reusing their existing password? (Select TWO).
A. Length of password
B. Password history
C. Minimum password age
D. Password expiration
E. Password complexity
F. Non-dictionary words
Correct Answer: BC
QUESTION 62
RADIUS provides which of the following?
A. Authentication, Authorization, Availability
B. Authentication, Authorization, Auditing
C. Authentication, Accounting, Auditing
D. Authentication, Authorization, Accounting
Correct Answer: D
QUESTION 63
In order for network monitoring to work properly, you need a PC and a network card running in what mode?
A. Launch
B. Exposed
C. Promiscuous
D. Sweep
Correct Answer: C
QUESTION 64
Users require access to a certain server depending on their job function. Which of the following would be the MOST appropriate strategy for securing the server?
A. Common access card
B. Role based access control
C. Discretionary access control
D. Mandatory access control
Correct Answer: B
QUESTION 65
A recent audit of a company’s identity management system shows that 30% of active accounts belong to people no longer with the firm. Which of the following should be performed to help avoid this scenario? (Select TWO).
A. Automatically disable accounts that have not been utilized for at least 10 days.
B. Utilize automated provisioning and de-provisioning processes where possible.
C. Request that employees provide a list of systems that they have access to prior to leaving the firm.
D. Perform regular user account review / revalidation process.
E. Implement a process where new account creations require management approval.
Correct Answer: BD
QUESTION 66
A company with a US-based sales force has requested that the VPN system be configured to authenticate the sales team based on their username, password and a client side certificate.
Additionally, the security administrator has restricted the VPN to only allow authentication from the US territory. How many authentication factors are in use by the VPN system?
A. 1
B. 2
C. 3
D. 4
Correct Answer: C
QUESTION 67
A network administrator has a separate user account with rights to the domain administrator group. However, they cannot remember the password to this account and are not able to login to the server when needed. Which of the following is
MOST accurate in describing the type of issue the administrator is experiencing?
A. Single sign-on
B. Authorization
C. Access control
D. Authentication
Correct Answer: D
QUESTION 68
A user attempting to log on to a workstation for the first time is prompted for the following information before being granted access: username, password, and a four-digit security pin that was mailed to him during account registration. This is
an example of which of the following?
A. Dual-factor authentication
B. Multifactor authentication
C. Single factor authentication
D. Biometric authentication
Correct Answer: C
QUESTION 69
After a recent internal audit, the security administrator was tasked to ensure that all credentials must be changed within 90 days, cannot be repeated, and cannot contain any dictionary words or patterns. All credentials will remain enabled
regardless of the number of attempts made. Which of the following types of user account options were enforced? (Select TWO).
A. Recovery
B. User assigned privileges
C. Lockout
D. Disablement
E. Group based privileges
F. Password expiration
G. Password complexity
Correct Answer: FG
QUESTION 70
Which of the following is the difference between identification and authentication of a user?
A. Identification tells who the user is and authentication tells whether the user is allowed to logon to a system.
B. Identification tells who the user is and authentication proves it.
C. Identification proves who the user is and authentication is used to keep the users data secure.
D. Identification proves who the user is and authentication tells the user what they are allowed to do.
Correct Answer: B
QUESTION 71
Sara, a security manager, has decided to force expiration of all company passwords by the close of business day. Which of the following BEST supports this reasoning?
A. A recent security breach in which passwords were cracked.
B. Implementation of configuration management processes.
C. Enforcement of password complexity requirements.
D. Implementation of account lockout procedures.
Correct Answer: A
QUESTION 72
Which of the following security benefits would be gained by disabling a terminated user account rather than deleting it?
A. Retention of user keys
B. Increased logging on access attempts
C. Retention of user directories and files
D. Access to quarantined files
Correct Answer: A
QUESTION 73
Ann, a security administrator at a call center, has been experiencing problems with users intentionally installing unapproved and occasionally malicious software on their computers. Due to the nature of their jobs, Ann cannot change their
permissions. Which of the following would BEST alleviate her concerns?
A. Deploy a HIDS suite on the users’ computers to prevent application installation.
B. Maintain the baseline posture at the highest OS patch level.
C. Enable the pop-up blockers on the users’ browsers to prevent malware.
D. Create an approved application list and block anything not on it.
Correct Answer: D
QUESTION 74
A security administrator has deployed all laptops with Self Encrypting Drives (SED) and enforces key encryption. Which of the following represents the greatest threat to maintaining data confidentiality with these devices?
A. Full data access can be obtained by connecting the drive to a SATA or USB adapter bypassing the SED hardware.
B. A malicious employee can gain the SED encryption keys through software extraction allowing access to other laptops.
C. If the laptop does not use a Secure Boot BIOS, the SED hardware is not enabled allowing full data access.
D. Laptops that are placed in a sleep mode allow full data access when powered back on.
Correct Answer: D
QUESTION 75
A company plans to expand by hiring new engineers who work in highly specialized areas. Each engineer will have very different job requirements and use unique tools and applications in their job. Which of the following is MOST appropriate
to use?
A. Role-based privileges
B. Credential management
C. User assigned privileges
D. User access
Correct Answer: A
QUESTION 76
Account lockout is a mitigation strategy used by Jane, the administrator, to combat which of the following attacks? (Select TWO).
A. Spoofing
B. Man-in-the-middle
C. Dictionary
D. Brute force
E. Privilege escalation
Correct Answer: CD
QUESTION 77
Which of the following is an authentication and accounting service that uses TCP for connecting to routers and switches?
A. DIAMETER
B. RADIUS
C. TACACS+
D. Kerberos
Correct Answer: C
QUESTION 78
A recent audit has discovered that at the time of password expiration clients are able to recycle the previous credentials for authentication. Which of the following controls should be used together to prevent this from occurring? (Select TWO).
A. Password age
B. Password hashing
C. Password complexity
D. Password history
E. Password length
Correct Answer: AD
QUESTION 79
An auditing team has found that passwords do not meet best business practices. Which of the following will MOST increase the security of the passwords? (Select TWO).
A. Password Complexity
B. Password Expiration
C. Password Age
D. Password Length
E. Password History
Correct Answer: AD
QUESTION 80
Which of the following protocols provides for mutual authentication of the client and server?
A. Two-factor authentication
B. Radius
C. Secure LDAP
D. Biometrics
Correct Answer: C
QUESTION 81
Ann, the security administrator, wishes to implement multifactor security. Which of the following should be implemented in order to compliment password usage and smart cards?
A. Hard tokens
B. Fingerprint readers
C. Swipe badge readers
D. Passphrases
Correct Answer: B
QUESTION 82
Which of the following services are used to support authentication services for several local devices from a central location without the use of tokens?
A. TACACS+
B. Smartcards
C. Biometrics
D. Kerberos
Correct Answer: A
QUESTION 83
After Ann, a user, logs into her banking websites she has access to her financial institution mortgage, credit card, and brokerage websites as well. Which of the following is being described?
A. Trusted OS
B. Mandatory access control
C. Separation of duties
D. Single sign-on
Correct Answer: D
QUESTION 84
Which of the following is an authentication method that can be secured by using SSL?
A. RADIUS
B. LDAP
C. TACACS+
D. Kerberos
Correct Answer: B
QUESTION 85
A small company has a website that provides online customer support. The company requires an account recovery process so that customers who forget their passwords can regain access.
Which of the following is the BEST approach to implement this process?
A. Replace passwords with hardware tokens which provide two-factor authentication to the online customer support site.
B. Require the customer to physically come into the company’s main office so that the customer can be authenticated prior to their password being reset.
C. Web-based form that identifies customer by another mechanism and then emails the customer their forgotten password.
D. Web-based form that identifies customer by another mechanism, sets a temporary password and forces a password change upon first login.
Correct Answer: D
QUESTION 86
Which of the following common access control models is commonly used on systems to ensure a “need to know” based on classification levels?
A. Role Based Access Controls
B. Mandatory Access Controls
C. Discretionary Access Controls
D. Access Control List
Correct Answer: B
QUESTION 87
A customer has provided an email address and password to a website as part of the login process. Which of the following BEST describes the email address?
A. Identification
B. Authorization
C. Access control
D. Authentication
Correct Answer: A
QUESTION 88
Speaking a passphrase into a voice print analyzer is an example of which of the following security concepts?
A. Two factor authentication
B. Identification and authorization
C. Single sign-on
D. Single factor authentication
Correct Answer: A
QUESTION 89
A Chief Information Security Officer (CISO) wants to implement two-factor authentication within the company. Which of the following would fulfill the CISO’s requirements?
A. Username and password
B. Retina scan and fingerprint scan
C. USB token and PIN
D. Proximity badge and token
Correct Answer: C
QUESTION 90
A security administrator is concerned about the strength of user’s passwords. The company does not want to implement a password complexity policy. Which of the following can the security Administrator implement to mitigate the risk of an
online password attack against users with weak passwords?
A. Increase the password length requirements
B. Increase the password history
C. Shorten the password expiration period
D. Decrease the account lockout time
Correct Answer: C
QUESTION 91
Which of the following protocols is MOST likely to be leveraged by users who need additional information about another user?
A. LDAP
B. RADIUS
C. Kerberos
D. TACACS+
Correct Answer: A
QUESTION 92
A security administrator is reviewing the below output from a password auditing tool:
P@ss.
@pW1.
S3cU4
Which of the following additional policies should be implemented based on the tool’s output?
A. Password age
B. Password history
C. Password length
D. Password complexity
Correct Answer: C
QUESTION 93
In order for Sara, a client, to logon to her desktop computer, she must provide her username, password, and a four digit PIN. Which of the following authentication methods is Sara using?
A. Three factor
B. Single factor
C. Two factor
D. Four factor
Correct Answer: B
QUESTION 94
A new intern was assigned to the system engineering department, which consists of the system architect and system software developer’s teams. These two teams have separate privileges. The intern requires privileges to view the system
architectural drawings and comment on some software development projects. Which of the following methods should the system administrator implement?A. Group based privileges
B. Generic account prohibition
C. User access review
D. Credential management
Correct Answer: A
QUESTION 95
Joe Has read and write access to his own home directory. Joe and Ann are collaborating on a project, and Joe would like to give Ann write access to one particular file in this home directory. Which of the following types of access control
would this reflect?
A. Role-based access control
B. Rule-based access control
C. Mandatory access control
D. Discretionary access control
Correct Answer: D
QUESTION 96
A security administrator must implement a system that will support and enforce the following file system access control model:
FILE NAMESECURITY LABEL
Employees.docConfidential
Salary.xlsConfidential
OfficePhones.xlsUnclassified
PersonalPhones.xlsRestricted
Which of the following should the security administrator implement?
A. White and black listing
B. SCADA system
C. Trusted OS
D. Version control
Correct Answer: C
QUESTION 97
In Kerberos, the Ticket Granting Ticket (TGT) is used for which of the following?
A. Identification
B. Authorization
C. Authentication
D. Multifactor authentication
Correct Answer: C
QUESTION 98
Employee badges are encoded with a private encryption key and specific personal information.
The encoding is then used to provide access to the network. Which of the following describes this access control type?
A. Smartcard
B. Token
C. Discretionary access control
D. Mandatory access control
Correct Answer: A
QUESTION 99
Which of the following relies on the use of shared secrets to protect communication?
A. RADIUS
B. Kerberos
C. PKI
D. LDAP
Correct Answer: A
QUESTION 100
A system administrator is configuring UNIX accounts to authenticate against an external server. The configuration file asks for the following information DC=ServerName and DC=COM. Which of the following authentication services is being
used?
A. RADIUS
B. SAML
C. TACACS+
D. LDAP
Correct Answer: D
QUESTION 101
Which of the following is a measure of biometrics performance which rates the ability of a system to correctly authenticate an authorized user?
A. Failure to capture
B. Type II
C. Mean time to register
D. Template capacity
Correct Answer: B
QUESTION 102
During an audit, the security administrator discovers that there are several users that are no longer employed with the company but still have active user accounts. Which of the following should be performed?
A. Account recovery
B. Account disablement
C. Account lockouts
D. Account expiration
Correct Answer: B
QUESTION 103
ABC company has a lot of contractors working for them. The provisioning team does not always get notified that a contractor has left the company. Which of the following policies would prevent contractors from having access to systems in
the event a contractor has left?
A. Annual account review
B. Account expiration policy
C. Account lockout policy
D. Account disablement
Correct Answer: B
QUESTION 104
A company wants to ensure that all credentials for various systems are saved within a central database so that users only have to login once for access to all systems. Which of the following would accomplish this?
A. Multi-factor authentication
B. Smart card access
C. Same Sign-On
D. Single Sign-On
Correct Answer: D
QUESTION 105
Which of the following techniques enables a highly secured organization to assess security weaknesses in real time?
A. Access control lists
B. Continuous monitoring
C. Video surveillance
D. Baseline reporting
Correct Answer: B
QUESTION 106
A network administrator, Joe, arrives at his new job to find that none of the users have changed their network passwords since they were initially hired. Joe wants to have everyone change their passwords immediately. Which of the following
policies should be enforced to initiate a password change?
A. Password expiration
B. Password reuse
C. Password recovery
D. Password disablement
Correct Answer: A
QUESTION 107
Joe, a network administrator, is able to manage the backup software console by using his network login credentials. Which of the following authentication services is the MOST likely using?
A. SAML
B. LDAP
C. iSCSI
D. Two-factor authentication
Correct Answer: B
QUESTION 108
Pete, a security auditor, has detected clear text passwords between the RADIUS server and the authenticator. Which of the following is configured in the RADIUS server and what technologies should the authentication protocol be changed
to?
A. PAP, MSCHAPv2
B. CHAP, PAP
C. MSCHAPv2, NTLMv2
D. NTLM, NTLMv2
Correct Answer: A
QUESTION 109
A technician wants to implement a dual factor authentication system that will enable the organization to authorize access to sensitive systems on a need-to-know basis. Which of the following should be implemented during the authorization
stage?
A. Biometrics
B. Mandatory access control
C. Single sign-on
D. Role-based access control
Correct Answer: A
QUESTION 110
Which of the following practices reduces the management burden of access management?
A. Password complexity policies
B. User account audit
C. Log analysis and review
D. Group based privileges
Correct Answer: D
QUESTION 111
An organization’s security policy states that users must authenticate using something you do. Which of the following would meet the objectives of the security policy?
A. Fingerprint analysis
B. Signature analysis
C. Swipe a badge
D. Password
Correct Answer: B
QUESTION 112
The company’s sales team plans to work late to provide the Chief Executive Officer (CEO) with a special report of sales before the quarter ends. After working for several hours, the team finds they cannot save or print the reports.
Which of the following controls is preventing them from completing their work?
A. Discretionary access control
B. Role-based access control
C. Time of Day access control
D. Mandatory access control
Correct Answer: C
QUESTION 113
A network administrator uses an RFID card to enter the datacenter, a key to open the server rack, and a username and password to logon to a server. These are examples of which of the following?
A. Multifactor authentication
B. Single factor authentication
C. Separation of duties
D. Identification
Correct Answer: B
QUESTION 114
A system administrator has noticed that users change their password many times to cycle back to the original password when their passwords expire. Which of the following would BEST prevent this behavior?
A. Assign users passwords based upon job role.
B. Enforce a minimum password age policy.
C. Prevent users from choosing their own passwords.
D. Increase the password expiration time frame.
Correct Answer: B
QUESTION 115
Which of the following BEST describes using a smart card and typing in a PIN to gain access to a system?
A. Biometrics
B. PKI
C. Single factor authentication
D. Multifactor authentication
Correct Answer: D
QUESTION 116
During the information gathering stage of a deploying role-based access control model, which of the following information is MOST likely required?
A. Conditional rules under which certain systems may be accessed
B. Matrix of job titles with required access privileges
C. Clearance levels of all company personnel
D. Normal hours of business operation
Correct Answer: B
QUESTION 117
Which of the following passwords is the LEAST complex?
A. MyTrain!45
B. Mytr@in!!
C. MyTr@in12
D. MyTr@in#8
Correct Answer: B
QUESTION 118
Which of the following should be done before resetting a user’s password due to expiration?
A. Verify the user’s domain membership.
B. Verify the user’s identity.
C. Advise the user of new policies.
D. Verify the proper group membership.
Correct Answer: B
QUESTION 119
Which of the following is an authentication service that uses UDP as a transport medium?
A. TACACS+
B. LDAP
C. Kerberos
D. RADIUS
Correct Answer: D
QUESTION 120
Ann works at a small company and she is concerned that there is no oversight in the finance department; specifically, that Joe writes, signs and distributes paycheques, as well as other expenditures. Which of the following controls can she
implement to address this concern?
A. Mandatory vacations
B. Time of day restrictions
C. Least privilege
D. Separation of duties
Correct Answer: D
QUESTION 121
A recent review of accounts on various systems has found that after employees’ passwords are required to change they are recycling the same password as before. Which of the following policies should be enforced to prevent this from
happening? (Select TWO).
A. Reverse encryption
B. Minimum password age
C. Password complexity
D. Account lockouts
E. Password history
F. Password expiration
Correct Answer: BE
QUESTION 122
Which of the following types of authentication solutions use tickets to provide access to various resources from a central location?
A. Biometrics
B. PKI
C. ACLs
D. Kerberos
Correct Answer: D
QUESTION 123
Use of a smart card to authenticate remote servers remains MOST susceptible to which of the following attacks?
A. Malicious code on the local system
B. Shoulder surfing
C. Brute force certificate cracking
D. Distributed dictionary attacks
Correct Answer: A
QUESTION 124
The security administrator notices a user logging into a corporate Unix server remotely as root. Which of the following actions should the administrator take?
A. Create a firewall rule to block SSH
B. Delete the root account
C. Disable remote root logins
D. Ensure the root account has a strong password
Correct Answer: C
QUESTION 125
Which of the following types of authentication packages user credentials in a ticket?
A. Kerberos
B. LDAP
C. TACACS+
D. RADIUS
Correct Answer: A
QUESTION 126
An organization is implementing a password management application which requires that all local administrator passwords be stored and automatically managed. Auditors will be responsible for monitoring activities in the application by
reviewing the logs. Which of the following security controls is the BEST option to prevent auditors from accessing or modifying passwords in the application?
A. Time of day restrictions
B. Create user accounts for the auditors and assign read-only access
C. Mandatory access control
D. Role-based access with read-only
Correct Answer: D
QUESTION 127
A new network administrator is setting up a new file server for the company. Which of the following would be the BEST way to manage folder security?
A. Assign users manually and perform regular user access reviews
B. Allow read only access to all folders and require users to request permission
C. Assign data owners to each folder and allow them to add individual users to each folder
D. Create security groups for each folder and assign appropriate users to each group
Correct Answer: D
QUESTION 128
A user ID and password together provide which of the following?
A. Authorization
B. Auditing
C. Authentication
D. Identification
Correct Answer: C
QUESTION 129
A file on a Linux server has default permissions of rw-rw-r–. The system administrator has verified that Ann, a user, is not a member of the group owner of the file. Which of the following should be modified to assure that Ann has read access
to the file?
A. User ownership information for the file in question
B. Directory permissions on the parent directory of the file in question
C. Group memberships for the group owner of the file in question
D. The file system access control list (FACL) for the file in question
Correct Answer: C
QUESTION 130
An insurance company requires an account recovery process so that information created by an employee can be accessed after that employee is no longer with the firm. Which of the following is the BEST approach to implement this
process?
A. Employee is required to share their password with authorized staff prior to leaving the firm
B. Passwords are stored in a reversible form so that they can be recovered when needed
C. Authorized employees have the ability to reset passwords so that the data is accessible
D. All employee data is exported and imported by the employee prior to them leaving the firm
Correct Answer: C
QUESTION 131
A network inventory discovery application requires non-privileged access to all hosts on a network for inventory of installed applications. A service account is created by the network inventory discovery application for accessing all hosts.
Which of the following is the MOST efficient method for granting the account non-privileged access to the hosts?
A. Implement Group Policy to add the account to the users group on the hosts
B. Add the account to the Domain Administrator group
C. Add the account to the Users group on the hosts
D. Implement Group Policy to add the account to the Power Users group on the hosts.
Correct Answer: A
QUESTION 132
A supervisor in the human resources department has been given additional job duties in the accounting department. Part of their new duties will be to check the daily balance sheet calculations on spreadsheets that are restricted to the
accounting group. In which of the following ways should the account be handled?
A. The supervisor should be allowed to have access to the spreadsheet files, and their membership in the human resources group should be terminated.
B. The supervisor should be removed from the human resources group and added to the accounting group.
C. The supervisor should be added to the accounting group while maintaining their membership in the human resources group.
D. The supervisor should only maintain membership in the human resources group.
Correct Answer: C
QUESTION 133
An information bank has been established to store contacts, phone numbers and other records.
An application running on UNIX would like to connect to this index server using port 88. Which of the following authentication services would this use this port by default?
A. Kerberos
B. TACACS+
C. Radius
D. LDAP
Correct Answer: A
QUESTION 134
A user has forgotten their account password. Which of the following is the BEST recovery strategy?
A. Upgrade the authentication system to use biometrics instead.
B. Temporarily disable password complexity requirements.
C. Set a temporary password that expires upon first use.
D. Retrieve the user password from the credentials database.
Correct Answer: C
QUESTION 135
Ann has taken over as the new head of the IT department. One of her first assignments was to implement AAA in preparation for the company’s new telecommuting policy. When she takes inventory of the organizations existing network
infrastructure, she makes note that it is a mix of several different vendors. Ann knows she needs a method of secure centralized access to the company’s network resources. Which of the following is the BEST service for Ann to implement?
A. RADIUS
B. LDAP
C. SAML
D. TACACS+
Correct Answer: A
QUESTION 136
The fundamental information security principals include confidentiality, availability and which of the following?
A. The ability to secure data against unauthorized disclosure to external sources
B. The capacity of a system to resist unauthorized changes to stored information
C. The confidence with which a system can attest to the identity of a user
D. The characteristic of a system to provide uninterrupted service to authorized users
Correct Answer: B
QUESTION 137
The IT department has setup a share point site to be used on the intranet. Security has established the groups and permissions on the site. No one may modify the permissions and all requests for access are centrally managed by the
security team. This is an example of which of the following control types?
A. Rule based access control
B. Mandatory access control
C. User assigned privilege
D. Discretionary access control
Correct Answer: D
QUESTION 138
A company has 5 users. Users 1, 2 and 3 need access to payroll and users 3, 4 and 5 need access to sales. Which of the following should be implemented to give the appropriate access while enforcing least privilege?
A. Assign individual permissions to users 1 and 2 for payroll. Assign individual permissions to users 4 and 5 for sales. Make user 3 an administrator.
B. Make all users administrators and then restrict users 1 and 2 from sales. Then restrict users 4 and 5 from payroll.
C. Create two additional generic accounts, one for payroll and one for sales that users utilize.
D. Create a sales group with users 3, 4 and 5. Create a payroll group with users 1, 2 and 3.
Correct Answer: D
QUESTION 139
Which of the following is an important implementation consideration when deploying a wireless network that uses a shared password?
A. Authentication server
B. Server certificate
C. Key length
D. EAP method
Correct Answer: C
QUESTION 140
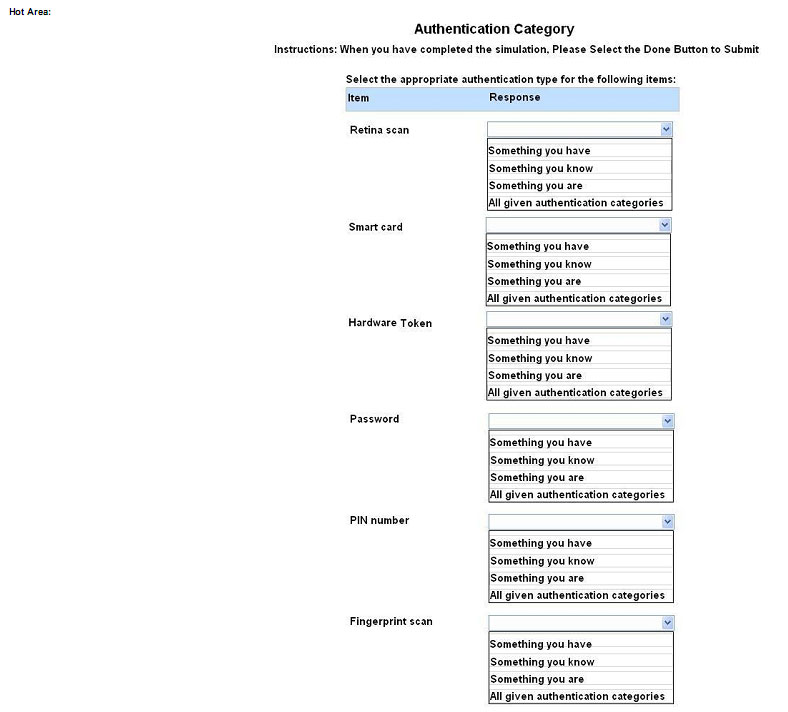
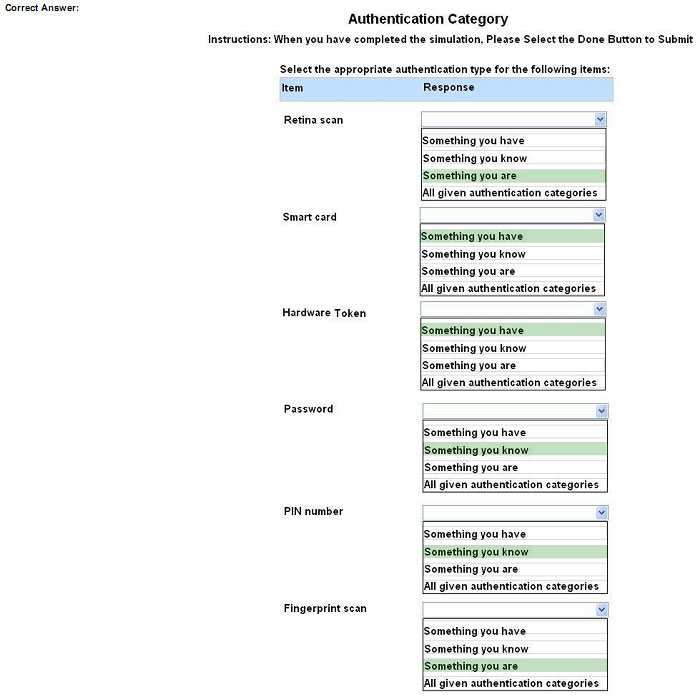
For each of the given items, select the appropriate authentication category from the dropdown choices.
Instructions: When you have completed the simulation, please select the Done button to submit.

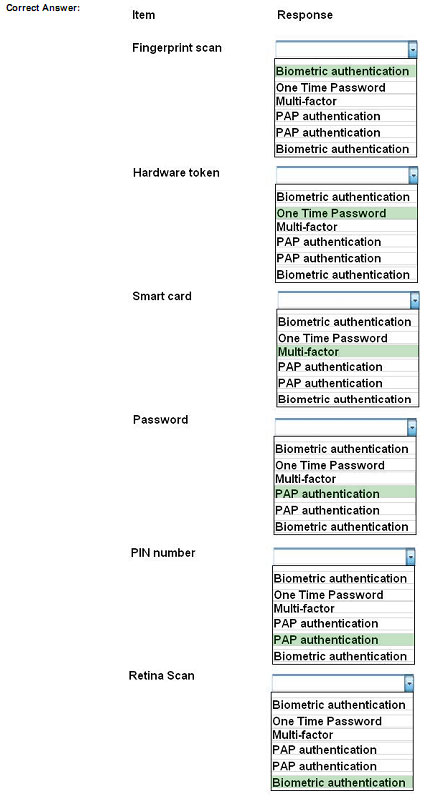
QUESTION 141
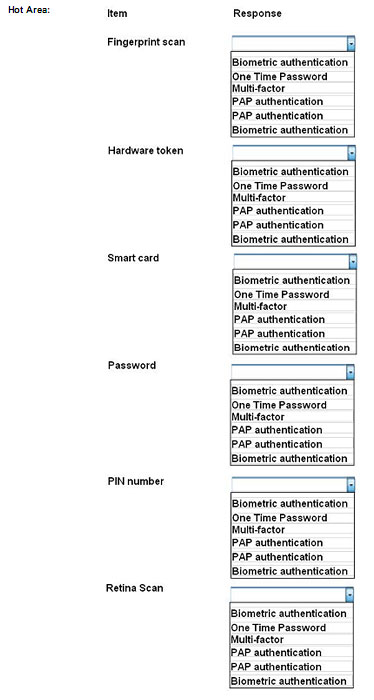
For each of the given items, select the appropriate authentication category from the drop down choices.
Select the appropriate authentication type for the following items:

About the exam:
CompTIA Security+ is the first security certification IT professionals should earn. It establishes the core knowledge
required of any cybersecurity role and provides a springboard to intermediate-level cybersecurity jobs. Security+
incorporates best practices in hands-on trouble-shooting to ensure security professionals have practical security
problem-solving skills. Cybersecurity professionals with Security+ know how to address security incidents –
not just identify them.
The new CompTIA Security+ SY0-501 exam is available as of October 4, 2017. More information on both versions of the exam is
available in the Exam Details below.
Conclusion:
We shared 141 free CompTIA security+ sy0-401 exam dumps and sy0-401 PDF to help you get started with the first step
of certification, and to easily pass the exam requires a complete selection of https://www.pass4itsure.com/sy0-401.html PDF + VCE
(100% guaranteed actual validity, 100% latest, 100% guaranteed invalid refund)
[PDF] Free CompTIA Security+ SY0-401 dumps download from Google Drive:
https://drive.google.com/open?id=1fNUvuARTsqEpjU2G_fxVaZCoDDWhG1sd
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
Pass4itsure Promo Code 15% Off
related: https://www.certificationmonitor.com/the-best-cisco-300-360-dumps-practice-test/