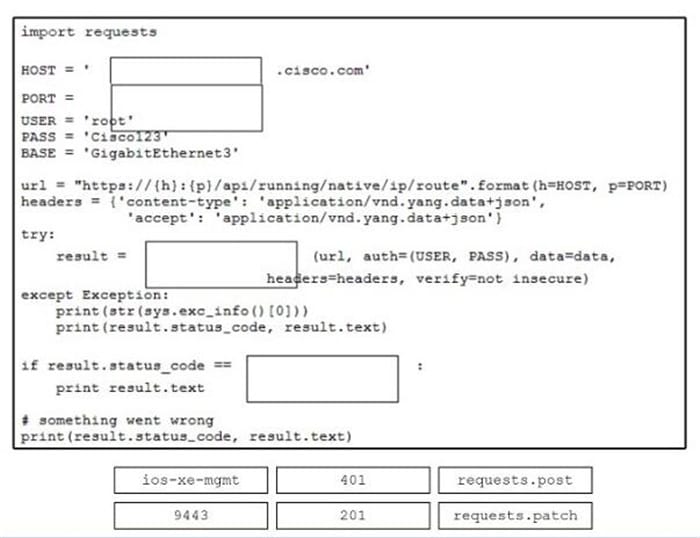
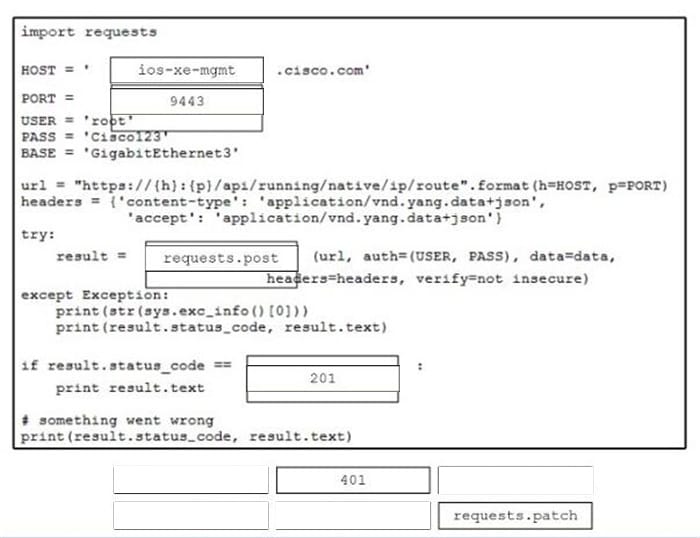
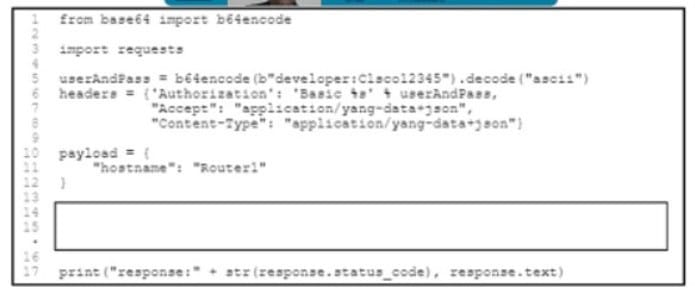
Say NO to 350-501 SPCOR exam failure! The recently updated 350-501 dumps help you easily prepare for the exam.
Here’s how to do it: You can easily prepare for the exam with the help of the 350-501 dumps (Update), download the 350-501 dumps https://www.pass4itsure.com/350-501.html (PDF, VCE) practice questions and answer questions now, or you can try Pass4itSure’s new Premium Program (All 4000+ Exam PDF& VCE dumps, One Package, from $199.79!)。
Of course, you can also get free 350-501 exam practice questions on this blog. Not only that but there is also a lot of new knowledge that will help you pass the exam.
Let’s start with the free 350-501 SPCOR exam question sharing (2024)
Come from: Pass4itSure
Question: 350-501 SPCOR exam questions Q1-Q13 were updated last time, and this time we will continue to update 15 channels
Certifications: CCNP Service Provider, CCIE Service Provider
Question 1:
Refer to the exhibit.
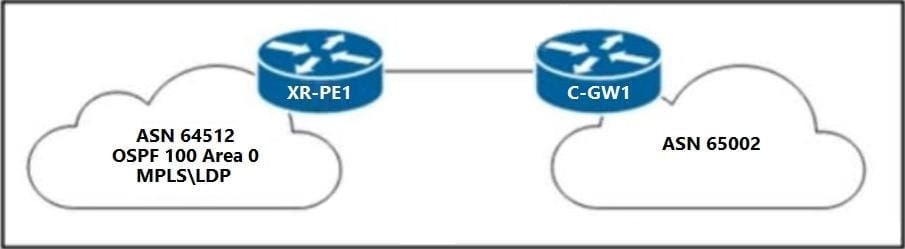
A network engineer must configure XR-PE1 for uninterruptible failover from the active RP to the standby RP. Neither peer device C-GW1 nor the core network of ASN 64512 supports graceful restart extensions. Which configuration must the engineer apply to XR-PE1 to complete the task?
A. nsr process-failures switchover router ospf 100 nsf cisco
B. router bgp 64512 nsrrouter ospf 100 nsrmpls ldp nsr
C. nsr process-failures switchover
router bgp 64512 nsr
router ospf 100 nsr
mpls ldp nsr
D. nsr process-failures switchover router ospf 100 nsf left
Correct Answer: C
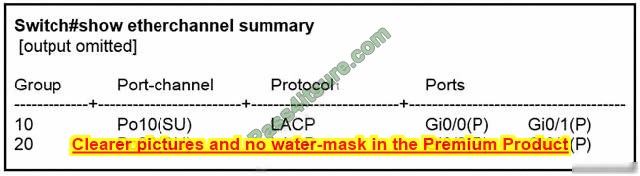
Question 2:
Refer to the exhibit.

An engineer is preparing to implement a link aggregation configuration. Which statement about this configuration is true?
A. The switch port negotiates an EtherChannel if it receives LACP packets from a connected peer running passive mode.
B. The switch port actively sends packets to negotiate an EtherChannel using PAgP.
C. The switch port passively negotiates an EtherChannel if it receives PAgP packets from a connected peer.
D. The switch port accepts LACP and PAgP packets from a connected peer and negotiates an EtherChannel using the common EtherChannel mode.
Correct Answer: B
Reference: https://www.cisco.com/en/US/docs/switches/metro/me3600x_3800x/trash/swethchl.html
Question 3:
Refer to the exhibit.
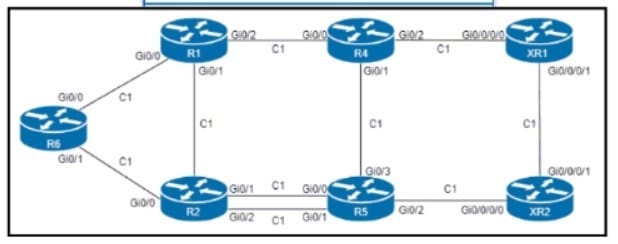
An engineer configured R6 as the headend LSR of an RSVP-TE LSP to router XR2, with the dynamic path signaled as R6-R2-R5-XR2. and set the OSPF cost of all links to 1. MPLS auto tunnel backup Is enabled on all routers to protect the LSP.
Which two NNHOP backup tunnels should the engineer use to complete the implementation? (Choose two.)
A. The R6 backup tunnel path R6-R1-R4-R5.
B. The R2 backup tunnel path R2-R5 across the alternate link.
C. The R2 backup tunnel path R2-R1-R4-XR1-XR2.
D. The R6 backup tunnel path R6-R2-R5
E. The R6 backup tunnel path R6-R1-R2.
Correct Answer: AC
Question 4:
A network engineer is configuring RIP as the routing protocol between multiple PEs and CEs. The engineer must avoid advertising the same routes back to their sources. Which action should be performed on the routers to accomplish this task?
A. Define the site of origin on each interface.
B. Configure a different route distinguisher for each prefix.
C. Define VRFs on each device to separate the traffic.
D. Enable bidirectional forwarding detection on each device.
Correct Answer: C
Explanation
A. Define the site of origin (SoO) on each interface.
Site of Origin (SoO) is an attribute used in BGP, not RIP, to prevent routing loops in BGP/MPLS IP VPNs. It’s used to mark routes that have been received from a particular site to prevent those routes from being advertised back into the site, avoiding routing loops.
Relevance: While SoO is relevant in the context of preventing routing loops, its application is more aligned with BGP/MPLS scenarios and not directly applicable to RIP routing between PEs and CEs in the manner the question suggests.
B. Configure a different route distinguisher for each prefix.
Route Distinguishers (RDs) are used in MPLS VPN technology to distinguish routes in different virtual routing and forwarding (VRF) instances. RDs make it possible for the same IP address space to be used in different VRFs without conflict.
Relevance: RDs are specific to MPLS VPN configurations and are not used in the context of RIP routing. They’re crucial for distinguishing between identical routes in different VPNs but do not directly impact the prevention of route advertisements back to their source in a traditional RIP environment.
C. Define VRFs on each device to separate the traffic.
Virtual Routing and Forwarding (VRF) is a technology that allows multiple instances of a routing table to coexist within the same router simultaneously. By using VRFs, network engineers can isolate and segregate traffic for different customers or different segments of their network.
Relevance: Defining VRFs would enable the segregation of traffic from different CEs, ensuring that routes learned from one CE are kept separate and are not advertised back to that CE or another CE within the same VPN. This approach can effectively prevent the advertisement of routes back to their sources in an environment where PEs and CEs are involved.
D. Enable bidirectional forwarding detection (BFD) on each device.
Bidirectional Forwarding Detection (BFD) is a protocol designed to quickly detect failures in the path between two forwarding engines, including interfaces, routers, and intermediate links.
Relevance: While BFD is valuable for detecting link failures rapidly, it does not directly contribute to the prevention of advertising the same routes back to their sources.
Correct Action to Accomplish the Task
Given the objective of avoiding advertising the same routes back to their sources in a network utilizing RIP between PEs and CEs, the most appropriate action would be:
C. Define VRFs on each device to separate the traffic.
This option directly addresses the goal by ensuring that routes are not advertised back to their source, leveraging the isolation provided by VRFs to maintain separate routing information for each CE in a multi-tenant environment or within distinct segments of a network. This separation is crucial in preventing routing loops and ensuring efficient routing decisions in a network setup involving RIP among multiple PEs and CEs.
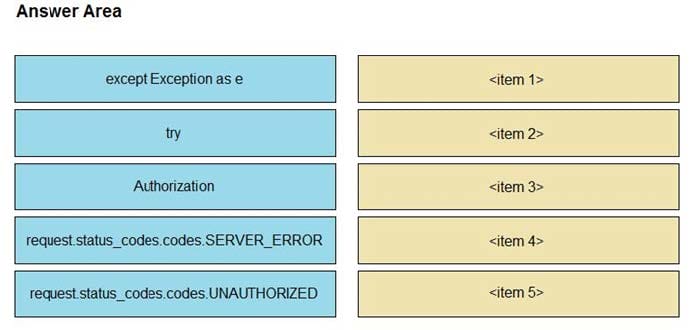
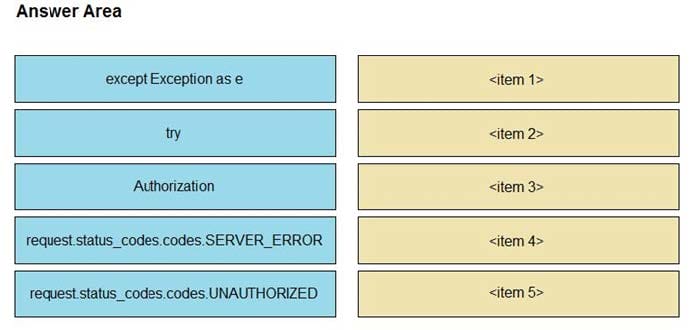
Question 5:
DRAG DROP
Drag and drop the NAT64 descriptions from the left onto the correct NAT64 types on the right.
Select and Place:
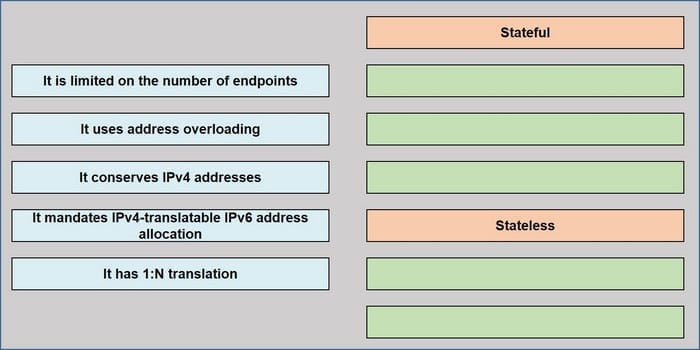
Correct Answer:
Stateful (It has 1: N translation, It uses address overloading, It conservers IPv4 addresses)
Stateless (It is limited on the number of endpoints, It mandates IPv4-translatable IPv6 address allocation)
Question 6:
What is a feature of model-driven telemetry?
A. It occasionally streams to multiple servers in the network.
B. It is less secure because it uses community strings.
C. It uses the pull model to send requested data to a client when polled.
D. It uses the push model to stream data to desired destinations.
Correct Answer: D
Explanation
Model-driven telemetry (MDT) is a modern approach to network monitoring and management that significantly enhances the capabilities and efficiency of network operations. Here’s a breakdown of the options provided, leading to why D is the correct answer:
A. It occasionally streams to multiple servers in the network. This statement is somewhat misleading. Model-driven telemetry can continuously stream data to multiple servers or endpoints, not just occasionally. The key feature of MDT is its flexibility in streaming data as configured, but the term “occasionally” doesn’t accurately describe its capabilities.
B. It is less secure because it uses community strings. This statement is incorrect. Model-driven telemetry typically utilizes more secure, modern protocols like gRPC (gRPC Remote Procedure Calls) or HTTP/2 for data transmission, which rely on authentication methods far more secure than SNMP community strings. MDT’s design focuses on enhanced security and efficient data transport.
C. It uses the pull model to send requested data to a client when polled. This option describes the traditional SNMP (Simple Network Management Protocol) method of network monitoring, where a management station polls devices to retrieve data. MDT, on the other hand, fundamentally shifts away from this model.
D. It uses the push model to stream data to desired destinations. This is the defining feature of model-driven telemetry. Unlike traditional network monitoring solutions that rely on polling (pulling data from devices at intervals), MDT allows network devices to push data to monitoring and analytics tools in real time or at specified intervals. This push model enables more efficient network utilization, reduces latency in data gathering, and allows for near real-time monitoring and analysis of the network state.
Why D is Correct
Model-driven telemetry’s push model is a significant shift from traditional polling-based monitoring systems. By pushing data from the network devices to the monitoring systems, MDT enables a more scalable, real-time, and efficient way of gathering and analyzing telemetry data. This approach not only reduces the overhead on network devices but also provides a more granular view of the network’s health and performance, facilitating quicker and more informed decision-making.
Question 7:
Which module refers to the network automation using Ansible?
A. the iosxr_system module to collect facts from remote devices
B. the iosxr_user module to manage banners for users in the local database
C. the losxr_logging module to run debugging for seventy levels 2 to 5
D. the iosxr_command module to issue run commands on remote devices
Correct Answer: D
Explanation
Ansible is a popular automation tool used for configuration management, application deployment, task automation, and IT orchestration. It can automate network devices just like servers. Ansible uses modules to interact with various devices, systems, and services. Each module is designed to handle specific tasks on different platforms or devices. Regarding network automation, especially with Cisco IOS XR devices, several modules are designed for different functions:
A. the iosxr_system module to collect facts from remote devices: While there are modules to collect facts from remote devices in Ansible (like the ios_facts module for Cisco IOS devices), the iosxr_system module is not specifically described as a fact-collecting module in the provided options, nor is it accurately named for such a purpose in the context of Ansible’s naming conventions.
B. the iosxr_user module to manage banners for users in the local database: The iosxr_user module is indeed used in Ansible to manage user accounts on Cisco IOS XR devices. However, it’s primarily for user configuration rather than managing banners, which are typically handled by a different module or parameter set focused on system or login messages.
C. the losxr_logging module to run debugging for seventy levels 2 to 5: This option seems to contain a typographical error (losxr_logging instead of a correct module naming convention) and inaccurately describes a module’s purpose. In Ansible, logging modules are used to configure logging settings, not to run debugging sessions. Additionally, the description does not match a standard module’s functionality or naming convention.
D. the iosxr_command module to issue run commands on remote devices: This is the correct answer. The iosxr_command module in Ansible is used to send commands to Cisco IOS XR devices. This module allows network administrators to issue operational commands on remote devices for various purposes, such as gathering information, checking status, or applying configurations that do not directly translate into standard Ansible modules. This functionality is a key component of network automation, enabling the execution of commands across multiple devices in a consistent and automated manner.
Conclusion
In the context of network automation using Ansible, especially with Cisco IOS XR devices, D. the iosxr_command module is the correct module that refers to the capability to issue and run commands on remote devices. This functionality is essential for automating tasks that involve executing operational or configuration commands directly on network devices.
Question 8:
A network engineer is deploying VPLS configuration between multiple PE routers so that customer\’s remote offices have end-to-end LAN connectivity. Which additional configuration should the engineer perform on the PE routers to enable the virtual switch instance?
A. I2 vfl cisco test manual vpn id 100 neighbor 192.168.2.2 encapsulation mpls neighbor 192.168.3.3 encapsulation mpls
B. interface GigEthernet 1/1 switchport mode trunk switchport trunk encap dot1q switchport trunk allow vlan 2-10
C. interface Vlan 5 xconnect vfl ciscotest
D. interface Vlan 100 xconnect vfi ciscotest ip address 192.168.1.1 255.255.255
Correct Answer: A
Provisioning a Virtual Private LAN Services (VPLS) link involves provisioning the associated attachment circuit and a virtual forwarding instance (VFI) on a provider edge (PE) device. https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/mp_l2_vpns/configuration/xe-3s/mp-l2-vpns-xe-3s-book/mp-vpls.html
Question 9:
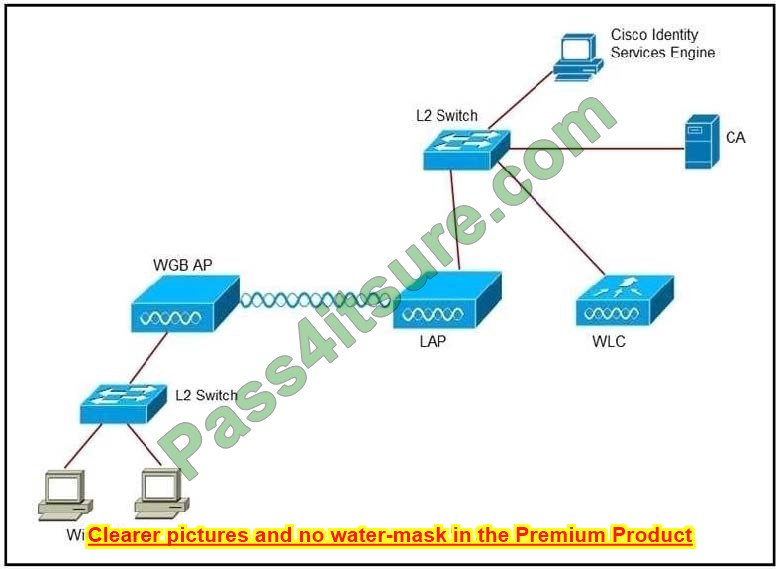
In an EVPN operation, how does the PE determine and advertise Ethernet segment reachability?
A. The PE discovers and shares routing information for the B-MAC addresses associated with local Ethernet segments.
B. The PE discovers remote ESIs and determines their redundancy mode.
C. The PE discovers the remote PEs in the EVI and builds a flood list linked with the EVI.
D. The PE discovers other PEs in the same Ethernet segment and elects a DF.
Correct Answer: D
Explanation
In an Ethernet VPN (EVPN) operation, the Provider Edge (PE) routers play a critical role in determining and advertising Ethernet segment (ES) reachability information. This is crucial for ensuring that Ethernet frames can be delivered across the network to the correct destinations, especially in multi-homed scenarios where redundancy and load balancing are important. Let’s analyze the provided options:
A. The PE discovers and shares routing information for the B-MAC addresses associated with local Ethernet segments.
While it’s true that PEs in an EVPN environment share routing information, including MAC addresses (B-MAC for bridge MAC in the case of EVPN), this option doesn’t directly address how Ethernet segment reachability is established or advertised, especially in the context of Ethernet segments and not just individual MAC addresses.
B. The PE discovers remote ESIs and determines their redundancy mode.
An Ethernet Segment Identifier (ESI) is a unique identifier that enables the network to distinguish between different Ethernet segments. While discovering ESIs is an important part of EVPN operation, and knowing their redundancy mode is important for determining how traffic should be handled, this option focuses more on the characteristics of the ES rather than the process of determining and advertising ES reachability itself.
C. The PE discovers the remote PEs in the EVI and builds a flood list linked with the EVI.
Ethernet VPN Instance (EVI) is a concept in EVPN that represents a unique VPN. While building a flood list is part of ensuring efficient traffic delivery within an EVI, this doesn’t specifically describe the process of discovering and advertising Ethernet segment reachability, which is more directly associated with how Ethernet segments are connected and reachable across the network.
D. The PE discovers other PEs in the same Ethernet segment and elects a Designated Forwarder (DF).
This option most accurately describes a critical function in EVPN operations related to Ethernet segment reachability. In multi-homed EVPN scenarios, where an Ethernet segment is connected to multiple PEs for redundancy, it’s essential to elect a Designated Forwarder (DF) among those PEs for each Ethernet segment. The DF is responsible for forwarding broadcast, unknown unicast, and multicast (BUM) traffic to and from the Ethernet segment. This process ensures that there’s no duplication of BUM traffic in the network and that the Ethernet segment’s reachability is efficiently managed. The election of a DF and the advertisement of this status to other PEs ensure that the network knows which PE to use for forwarding traffic to and from the multi-homed Ethernet segment, effectively advertising its reachability.
Conclusion:
The correct answer is D. The PE discovers other PEs in the same Ethernet segment and elects a DF. This process is fundamental to the operation of EVPN, especially in scenarios involving multi-homed Ethernet segments, as it ensures efficient and correct advertisement of Ethernet segment reachability across the network.
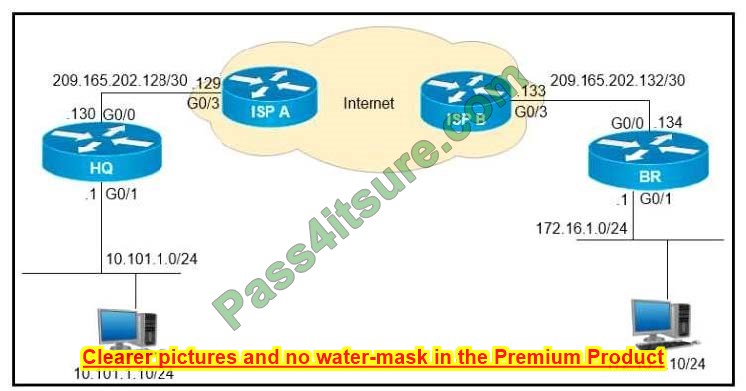
Question 10:
Refer to the exhibit.
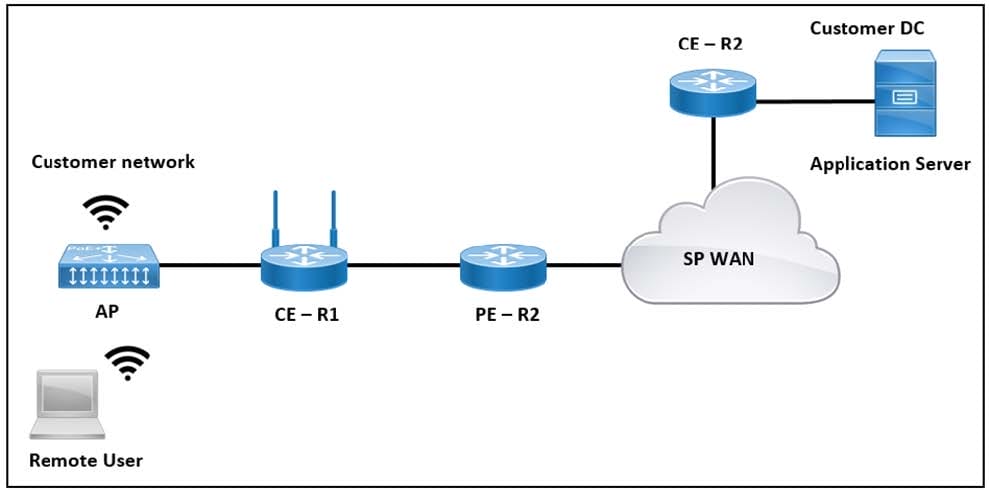
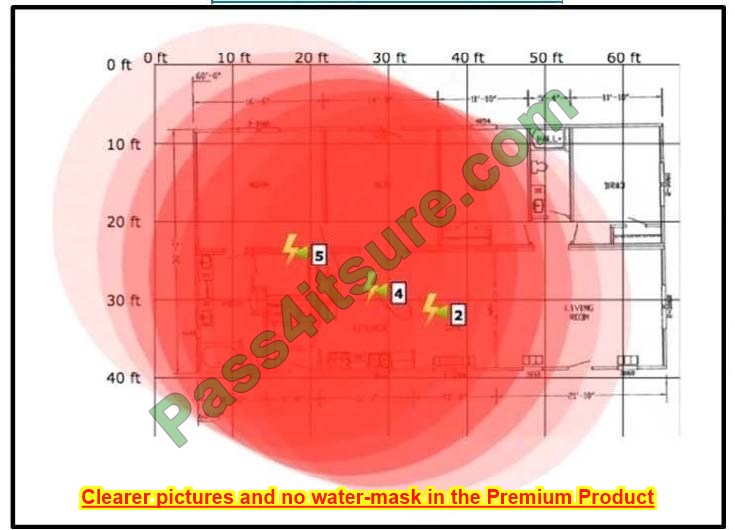
The application server in the data center hosts voice, video, and data applications over the internet. The data applications run more slowly than the voice and video applications. To ensure that all applications run smoothly, the service provider decided to implement a QoS policy on router PER 2 to apply traffic shaping. Which two actions must an engineer take to implement the task? (Choose two.)
A. Configure the scheduling function to handle delayed packets.
B. Enable packet remarking for priority traffic.
C. Configure a queue to buffer excess traffic.
D. Set the token value for secondary traffic.
E. Set a threshold to discard excess traffic.
Correct Answer: A
Question 11:
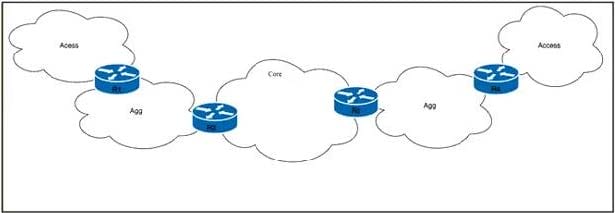
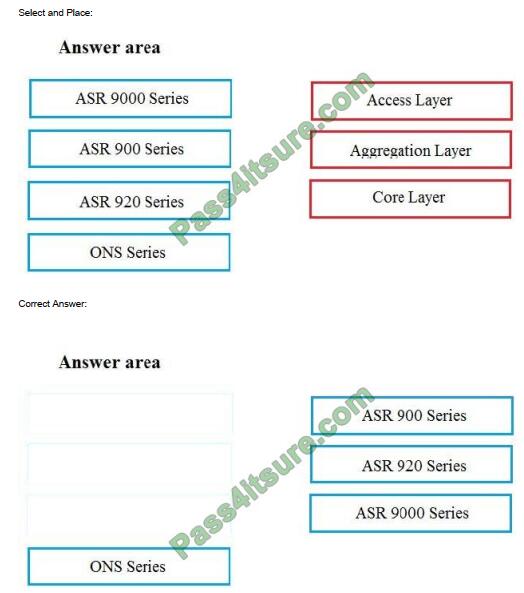
Refer to the exhibit. Tier 1 ISP A purchased several Tier 2 ISPs to increase their customer base and provide more regional coverage. ISP A plans to implement MPLS services in the access layer, with scalability up to 100,000 devices in one packet network and service recovery up to 50 ms. The network architect decided to use different independent IGP and LDP domains and interconnect LSPs that are based on RFC 3107. Which two actions must the network engineer perform to meet the requirements? (Choose two.)
A. Implement BGP inline RR functionality with next-hop-self capabilities on routers R2 and R3.
B. Implement the IS-IS routing protocol on the access domain.
C. Implement BGP connectivity between routers R1 and R4 with VPNv4 address family enabled.
D. Configure three OSPF areas, with Area 0 in the core domain, and Areas 2 and 3 in the aggregation domain.
E. Implement BGP PIC core functionality on routers R2 and R3.
Correct Answer: AE
Question 12:
Refer to the exhibit.

A network engineer is implementing QoS services. Which two statements about the QoS-group keyword on Cisco IOS XR are true? (Choose two.)
A. It marks packets for end-to-end QoS policy enforcement across the network.
B. QoS group marking occurs on the ingress.
C. The QoS group numbering corresponds to the priority level.
D. QoS group can be used in fabric QoS policy as match criteria.
E. It cannot be used with a priority traffic class.
Correct Answer: BD
Question 13:
DRAG DROP
Drag and drop the technologies from the left onto the correct definitions on the right.
Select and Place:
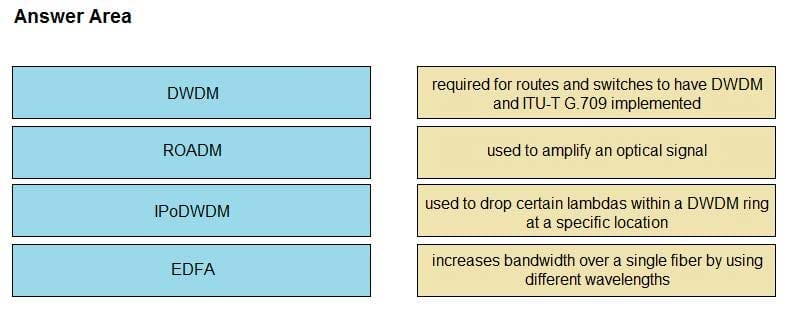
Correct Answer:
Question 14:
When configuring traffic engineering tunnels in the Cisco MPLS core network, you see the traffic is not tacking the expected path in the core. Which command do you use to quickly check the path of a TE tunnel?
A. traceroute
B. show mpls traffic-engineering tunnels
C. Ping
D. traceroute mpls ipv4
Correct Answer: D
Explanation
The D. traceroute mpls ipv4 command is specifically tailored for tracing the path of MPLS packets through the network. This command allows network engineers to see how MPLS-labeled packets are being routed, including the labels used at each hop. This is crucial for troubleshooting MPLS TE tunnels because it provides visibility into the actual path MPLS-TE labeled packets are taking through the network, which can be different from the expected path due to various reasons such as misconfiguration, link failures, or incorrect routing policies.
This command is more specific and direct for troubleshooting MPLS paths than the previously discussed B. show mpls traffic-engineering tunnels, which provides a broad overview of the TE tunnel configurations but doesn’t trace the packet flow through the network. In the context of checking the actual path taken by the traffic within TE tunnels, D. traceroute mpls ipv4 offers a more granular and practical insight into the packet-level routing decisions within the MPLS network.
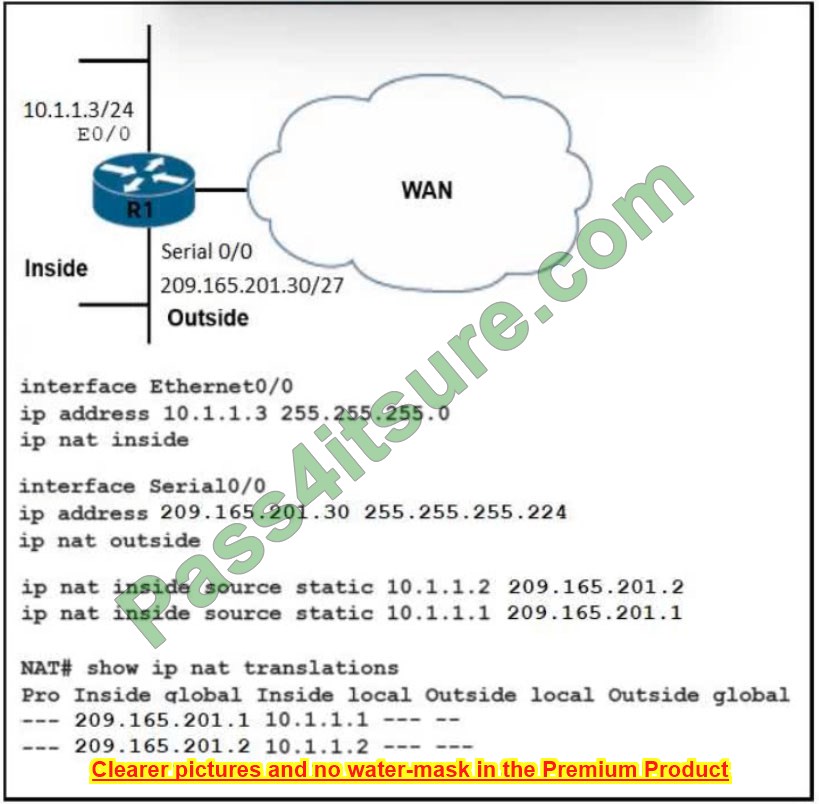
Question 15:
Refer to the exhibit

Which effect of this configuration is true?
A. R1 can support a peer that is configured for LDP SSO/NSF as the peer recovers from an outage.
B. can support a graceful restart operation on the peer, even if a graceful restart is disabled on the peer.
C. R1 can failover to any peer.
D. R1 can failover only to a peer that is configured for LDF SSO/NSF.
Correct Answer: A
Reference: https://www.cisco.com/en/US/docs/general/Test/kwoodwar/fsgr29s.html
With practice questions, is that enough? You need more study resources to pass the Cisco 350-501 SPCOR exam.
Keep learning.
A collection of the latest Cisco SPCOR exam study resources:
PDF format:
350-501 SPCOR Exam: Implementing and Operating Cisco Service Provider Network Core Technologies
Document format:
- Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)
- CCIE Service Provider Certification and Training
- CCNP Service Provider
- SPCOR study materials
Video format:
Still, have doubts? Look here
When you start looking at the Cisco 350 501 exam, you start to realize that there are almost no books used for the exam, so is there no SPCOR 350-501 study guidebook?
Yes, SPCOR has not released a book yet.
Where are the free exam questions for the 350-501 SPCOR exam available?
Here, you can also get it on the Pass4itSure website.
Is the Cisco 350 501 exam market very small, why are there so few resources on the Internet, and is the exam still worth passing?
There are few resources, you can find the latest 350 501 resources here (the latest in 2024), and the exam is well worth it for those who need to develop in this area.
Write at the end:
All that needs to be said has been said, in short, make good use of the 350-501 dumps (update) as a weapon to pass the exam, prepare well for your exam, and come on. Victory lies ahead.
Again, download Update 350-501 dumps https://www.pass4itsure.com/350-501.html (PDF, VCE, or try Pass4itSure’s new Premium Program) to get effective practice questions, and be sure to combine other resources with 350-501 dumps to learn better.
I wish you all a smooth exam and a happy day.