Search Results for: comptia
220-1001 Dumps Latest | Correct CompTIA A+ 220-1001 Exam Study Documents
All candidates seeking CompTIA A+ certification should pass the CompTIA A+ Certification Exam: Core 1 (220-1001). We’ve updated 220-1001 dumps, the most powerful CompTIA A+ 220-1001 exam study documents to help you pass easily.
Use the latest 220-1001 dumps >> https://www.pass4itsure.com/220-1001.html >> to pass the CompTIA A+ Certification Exam: Core 1 exam.
Need to figure out the basics of the CompTIA A+ 220-1001 exam?

Yes, the first step in passing the 220-1001 exam is to understand the basics of the exam.
Exam 220-1001 is one of the exams required to pass for CompTIA A+ certification, as well as exam 220-1002. Candidates must complete 220-1001 and 220-1002 to be certified.
A new version (220-1101 & 220-1102) now appears, gradually replacing the 220-1001 & 220-1002 exam.
The CompTIA 220-1001 exam has 90 questions. Question types are multiple-choice questions (single and multiple answers), drag-and-drop, and performance-based. The time limit is 90 minutes, and the score needs to reach 675 (in the range of 100-900) to pass. The exam costs $246.
How do I master and pass the CompTIA 220-1001 exam certification?
You’ll need the latest 220-1001 dumps, such as Pass4itSure 220-1001 dumps, to provide you with the correct CompTIA A+ 220-1001 exam study documents (220-1001 PDF + 220-1001 VCE) to help you prepare for the exam and practice hard to successfully pass the CompTIA 220-1001 exam certification.
Where can I get free dumps to study for the CompTIA A+ 220-1001 exam?
Here you can get the free 220-1001 dumps online download address below: https://drive.google.com/file/d/1AKTy5eSUmAQd5DpVZlTwmiYx-LsW0jzl/view?usp=sharing
Or, read it directly online.
Downloadzpdf.com provides you with a full range of CompTIA certification questions, and if needed, you can search for the free exam questions you want.
CompTIA A+ Core 1 (220-1001) Free Dumps Sample Questions [2022.9]
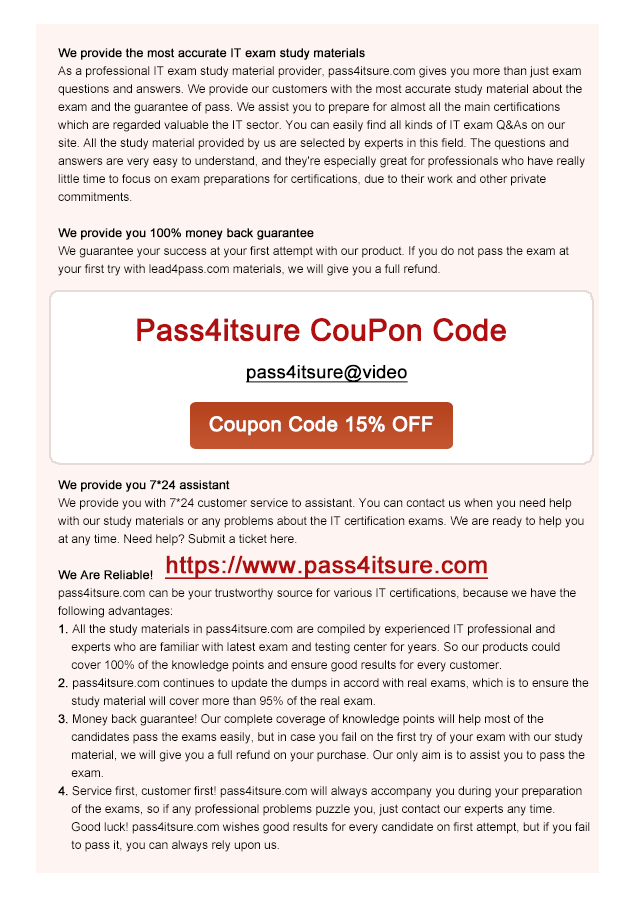
Q1
DRAG DROP
Drag and drop each mobile technology to the description of its use. Some answers will not be used.
Q2.
A few users have been noticing ongoing degradation of performance in a VDI environment A technician checks the
environment and discovers the shared VM is experiencing maximum CPU utilization Which of the following will the
Does the technician MOST likely configure to resolve the issue?
A. Network capacity
B. Resource pooling
C. Memory allocation
D. Replication scripts
Correct Answer: B
Q3.
A Windows 10 Pro user wants to initialize BitLocker to protect the system\\’s data while it is at rest. The computer does
not have a TPM. Which of the following is required to satisfy this need?
A. A BD-RE disc
B. An internal hard drive
C. A USB flash drive
D. A network share
Correct Answer: B
Q4.
A technician is installing a pair of 7.2K rpm hard drives into a NAS unit. Which of the following will provide the HIGHEST levels of performance for the setup?
A. RAID 0
B. RAID 1
C. RAID 5
D. RAID 10
Correct Answer: C
Q5.
A technician deployed a new computer and patched the unit to the data jack. However, no Ethernet connection is
detected. The technician suspects the patch panel is incorrectly numbered. Which of the following tools will the
technician MOST likely use to locate the jack on the patch panel?
A. A multimeter
B. A tone generator and a probe
C. A loopback plug
D. A cable tester
Correct Answer: B
Q6.
A technician was asked to virtualize four existing PCs before decommissioning them. The resulting VMs are imported
into a new VM workstation running a hypervisor on top of an OS Three of the VMs are running property, but the entire
system locks up when trying to start the fourth VM. Which of the following should the technician have reviewed prior to creating the VMs to prevent this from occurring? (Select TWO)
A. Hypervisor requirements
B. Storage requirements
C. Resource requirements
D. Network requirements
E. Backup requirements
F. Security requirements
Correct Answer: AF
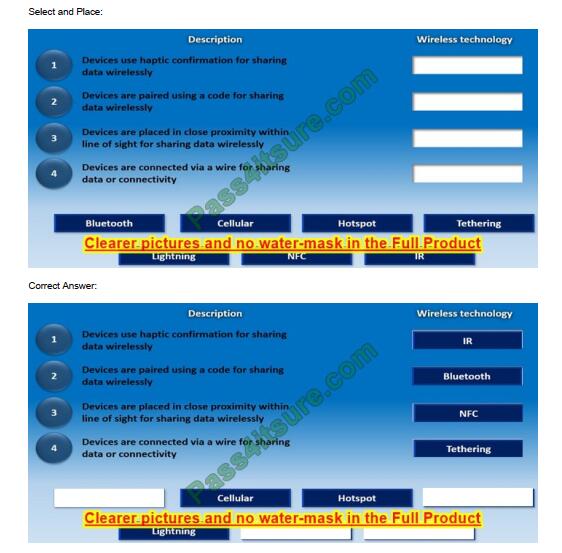
Q7.
SIMULATION
You need to configure your mobile device to send and receive electronic messages from your company. You must use the company\’s WLAN as all e-mail services are on default non-secure ports. The company\’s WLAN is broadcasting across the company for easier access. Users must authenticate to the server with the same credentials in order to send and receive emails. Authentication should be enforced in the settings of the mobile device using the following parameters:
- Username: [email protected]
- Password: P@$$w0rd
- Outgoing server: mail.techies.com
- Incoming server: pop3.techies.com
- Company SSID: Techies
- Security Key: CA:FE:33:71:00
INSTRUCTIONS:
Update the mobile device\’s parameters to fit the criteria and support the strongest encryption available.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
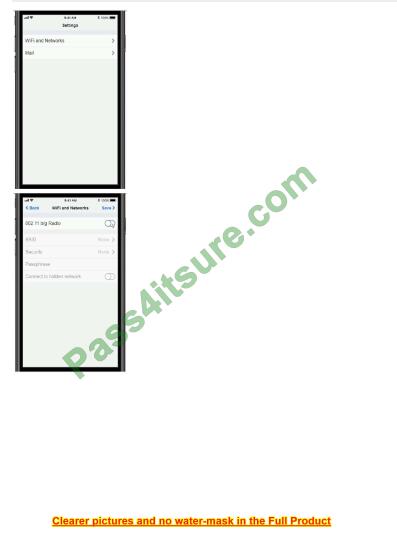
A. Check the answer in the explanation.
Correct Answer: A
For the WiFi setup, do the following:
1. Enable 802.11 b/g Radio
2. Choose the Techies SSID, and enter the CA: FE:33:71:00 Security Key.
3. Choose the “Same as Incoming Server” option below.
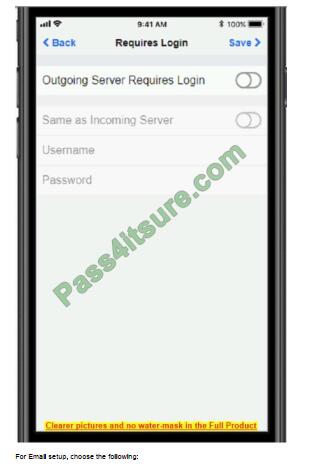
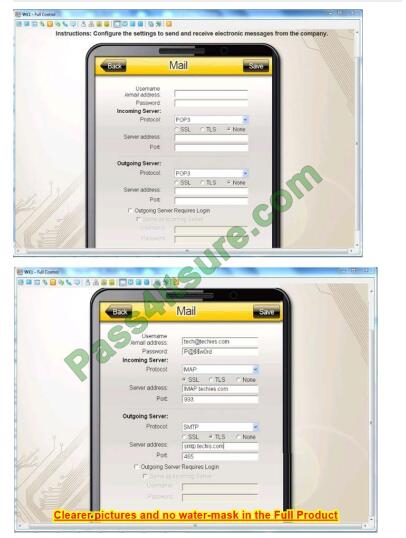
Q8.
A technician needs to install an IP-based camera in a remote location. The technician runs a Cat 6 cable to the location
and connects it to the camera. Which of the following is needed for the camera to operate?
A. USB to Ethernet adapter
B. DVI cable
C. PoE switch
D. H.261 codec
Correct Answer: C
Q9.
A customer recently moved a high-end graphics card from a known-working computer to a different computer. The
computer works without issue when viewing email and web pages or when using certain applications. However, when a
game with high-end graphics requirements is opened, the program will run for a few minutes before the computer shuts down. Which of the following is MOST likely causing the problem?
A. Power supply wattage
B. Video RAM
C. CPU frequency
D. Monitor resolution
Correct Answer: A
Q10.
Which of the following peripheral types is MOST likely to be used to input actions into a PC?
A. Webcam
B. Mouse
C. Monitor
D. Optical drive
Correct Answer: B
Q11.
A shipping department is having problems with its thermal label printer. Two columns on the left are not appearing on all labels. Which of the following should a technician do FIRST?
A. Verify the ribbon is correctly aligned to the label
B. Run a label calibration
C. Remove stuck labels from the print path
D. Replace the print head
Correct Answer: A
Q12.
A user is having trouble printing and has asked a technician for help. The technician is able to print remotely from the
print server. Which of the following will the technician MOST likely need to perform NEXT? (Choose two.)
A. Modify the environment variables on the computer
B. Check the AD account settings for the user
C. Replace the printer\’s network cable
D. Clear the print queue on the server
E. Check the network settings on the computer
F. Delete all the files from the server print spooler
Correct Answer: DE
Q13.
A customer wants to purchase a new home computer. The machine will mainly be used for internal browsing and
streaming video, except on weekends when the customer \’ son will use it to play games with friends. Which of the
following should the technician focus on to meet these requirements?
A. 80mm case fans
B. Four-core processor
C. RAID 5 array
D. 16GB DDR2 memory
E. Dual monitors
F. Encrypted hard drive
Correct Answer: BE
For more questions, please get the full Pass4itSure 220-1001 dumps: https://www.pass4itsure.com/220-1001.html
Easily Pass CompTIA Project+ PK0-003 exam, the latest effective PK0-003 exam dumps | 100% Free
Certificationmonitor is a free high quality blog that offers all exam dumps from pass4itsure experts. The latest effective 50
CompTIA Project+ PK0-003 exam dumps Practice test and free sharing of PK0-003 pdf, we keep an eye on the latest content to ensure that
all questions and answers are up to date. Free content allows you to progress and enhance your abilities, and if you want to easily
pass the exam to get a PK0-003 exam certificate, please select the full https://www.pass4itsure.com/pk0-003.html PDF + VCE
[PDF] Free CompTIA Project+ PK0-003 dumps download from Google Drive:
https://drive.google.com/open?id=1hbymsTa9IIcwUfeHZAxe8qTu_uuLobNC
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
Project+ (Plus) Certification | CompTIA IT Certifications:https://certification.comptia.org/certifications/project
About the exam:
The CompTIA Project+ examination is designed for business professionals who coordinate or manage small-to-medium-sized projects.
The successful candidate will have the knowledge and skills required to:
Manage the project life cycle
Ensure appropriate communication
Manage resources and stakeholders
Maintain project documentation
Pass4itsure offers the latest CompTIA Project+ PK0-003 practice test free of charge (50Q&As)
QUESTION 1
Which of the following MUST be clearly defined in a project charter?
A. Quality
B. Scope
C. Action items
D. WBS
Correct Answer: B
QUESTION 2
Which of the following is the MAIN difference between an open-ended and a close-ended problem
statement?
A. An open-ended problem statement leads to multiple solutions, while a close-ended one has limited
solutions.
B. An open-ended problem statement has a low success rate, while a close-ended problem statement has
a high success rate.
C. In open-ended problem statements, well defined resources cannot be allocated to the project, while a
close-ended one allows for defined resources.
D. An open-ended problem statement expands the scope of the project, while a close-ended one keeps
the project in scope.
Correct Answer: A
QUESTION 3
A project team member, Joe, has completed his project work. Although the project is not completed yet,
Joe has been assigned by the PMO director to a new project. Which of the following describes the
organization structure Joe works in?
A. Functional
B. Matrix
C. Project based
D. Strong Matrix
Correct Answer: C
QUESTION 4
Which of the following is used to provide a functional description of the efforts which are required in order
to accomplish a task?
A. Gantt chart
B. PERT
C. GERT
D. WBS dictionary
Correct Answer: D
QUESTION 5
A project manager is entering the list of a project’s activities with their estimated begin and end time to
visualize which activities overlap and when the project is scheduled to end. Which of the following is the
project manager building?
A. Gantt chart
B. Work Breakdown Structure
C. Critical PathD. PERT chart
Correct Answer: A
QUESTION 6
The project manager is sequencing a set of activities. They discover that some of the activities may or may
not occur based on the outcome of other activities. Which of the following is BEST suited in this situation to
show the activities’ logical relationship?
A. Gantt
B. ADM
C. CCB
D. CCM
Correct Answer: B
QUESTION 7
Which of the following is the MAIN difference between bottom up and top down cost estimation?
A. Bottom up leads to a more accurate cost estimate than top down because it is performed by subject
matter experts
B. Top down leads to a more accurate cost estimate because it is performed by upper management with
direct access to budget information
C. Bottom up leads to a less accurate cost estimate because it is breaks down the task into smaller
subtasks where some tasks may not have a cost
D. Both top down and bottom up are equally accurate estimation of a project’s total cost because they
both refer to resources assigned by the project sponsor
Correct Answer: A
QUESTION 8
Which of the following purchasing processes should a project team use to ensure that the work will be
done per company specifications, while selecting the overall cheapest provider?
A. RFI
B. RFP
C. RFC
D. RFQ
Correct Answer: B
QUESTION 9
One of the MAIN purposes of a kick-off meeting is to:
A. Assign and review roles and responsibilities to the project team.
B. Allow the project sponsor to introduce the project manager to the team.
C. Review the project definition document and make the appropriate changes.
D. Ensure project team members communicate amongst each others.
Correct Answer: A
QUESTION 10
After the ground breaking at a new construction site, the pile driving operation comes to a full stop due to
the nature of the terrain. Which of the following is MOST likely to occur?
A. The project communication plan must be updated and a stakeholder meeting must be scheduled.
B. The project manager must manage the new issue as the project schedule could be delayed.
C. The project manager must implement conflict resolution and review the resource requirement.D. The project scope statement must be reviewed and the project manager must prepare a performance
report.
Correct Answer: B
QUESTION 11
A new software solution is being deployed. The customer realizes that an important piece of the software
must be purchased in order for the project to be successful. Which of the following is TRUE about this
scenario?
A. The new piece of software will most likely expand the scope of the project therefore a new scope
statement must be written.
B. The current project must be completed and a new project can be started to implement the additional
software.
C. Quality management metrics are affected therefore the project manager should review the quality of the
project.
D. Project schedule may be affected and the project manager must follow the change control process.
Correct Answer: D
QUESTION 12
While performing a scheduled walkthrough at a construction site, the customer points out a discrepancy.
Which of the following is the FIRST step that should be taken before submitting a change control form?
A. Consult the project sponsor
B. Identify the change
C. Perform a feasibility study
D. Perform impact analysis
Correct Answer: B
QUESTION 13
A project team member has identified a required change to one of their assigned tasks. The change would
alter the order in which other tasks must be completed. Which of the following should be done NEXT?
A. Implement the change
B. Update the change registry
C. Document the change
D. Perform an impact analysis
Correct Answer: D
QUESTION 14
Additional company employees have been assigned to the project. Which of the following will be affected?
A. The timeline may be positively affected at the expense of the project cost.
B. This change does not affect the triple constraint because the additional employees are already on the
company payroll.
C. The quality of the product will improve but it will add more time to the project to train the new
employees.
D. Total project cost will be reduced because the project can now be completed sooner.
Correct Answer: A
QUESTION 15
Which of the following is the project manager implementing when they allocate additional resources to a
set of tasks that are in the critical path and are slowing down the project completion?
A. CrashingB. Optimizing
C. Controlling
D. Fast tracking
Correct Answer: A
QUESTION 16
The project manager is reviewing the Pareto chart to identify if the life cycle of a deliverable is producing
software bugs. Which of the following are represented in the chart? (Select TWO).
A. Number of work units affected by the bug
B. Percentage of bug types occurring
C. Software bug counts
D. Root cause of bug occurrence
E. Affect of the bug occurrence
Correct Answer: BC
QUESTION 17
The project manager wants to report to the stakeholders to date project’s cost performance. If the total of
completed work to date is $200,000 and the actual cost is $210,000, which of the following is the cost
variance?
A. -5%
B. 5%
C. -$10,000
D. $10,000
Correct Answer: C
QUESTION 18
Some of the stakeholders are losing interest in the project because of its length. Which of the following
should the project manager implement in this situation?
A. Remove the stakeholders who are losing interest to ensure successful completion of the project.
B. Limit communication with the stakeholders to the bare minimum and only report on the progress and
not the issues.
C. Implement a concise and reoccurring communication plan which focuses on the project goal and
accomplishments.
D. Review the project goal with the stakeholder and allow them to make the appropriate changes to keep
them interested.
Correct Answer: C
QUESTION 19
A project’s deliverable has been assigned to a team located in a different country. Although it is understood
that daily reports are due by close of business every weekday, the external team’s reports are consistently
being delivered after business hours. Which of the following is MOST likely occurring?
A. The external project team did not understand the report requirements due to the language barrier.
B. External project team members are always allowed to deliver reports late.
C. The project manager has not taken into consideration the time zone difference.
D. Cultural differences between the project manager and the external team were not considered.
Correct Answer: C
QUESTION 20
Which of the following should be used when determining the details of a project component or scopeentry?
A. WBS Dictionary
B. Project Management Plan
C. Work Breakdown Structure
D. Project Charter
Correct Answer: A
QUESTION 21
During the course of a project, key stakeholders have requested new requirements after the business
requirements document has already been signed off. Which of the following should have been performed
earlier in the project in order to deal with this situation?
A. Ensure that stakeholders understand that once requirements are approved the scope cannot be
changed.
B. Develop a clear communications flow between the project and business stakeholders.
C. Perform multiple rounds of requirements solicitation before permanently locking down the scope.
D. Agree on a process to deal with project change requests.
Correct Answer: D
QUESTION 22
Which of the following scheduling algorithms establishes floats, durations, and paths between work
schedule activities?
A. AON
B. PERT
C. CPM
D. GERT
Correct Answer: C
QUESTION 23
A draft structure for a risk tracking sheet has been provided below:
1. Risk identifier
2. Risk status
3. Risk description
4. Mitigation steps
5. Mitigation status
Which of the following should be ADDED to the risk tracking sheet?
A. Risk rating
B. Stakeholder risk tolerance
C. Revised project schedule
D. Risk matrix
Correct Answer: A
QUESTION 24
Which of the following is BEST suited for assigning resources to WBS tasks?
A. WBS defines functional teams which should then be mapped to project scope items
B. WBS contains the project schedule which should be used to determine timing of when to engage
functional teams
C. WBS defines the description of the end result delivered by the projectD. WBS defines activities and deliverables that can be mapped to functional teams
Correct Answer: D
QUESTION 25
Which of the following can be used as a quality metric when performing quality planning?
A. Quality control
B. Cost benefit analysis
C. Perform preventative actions
D. Quality assurance
Correct Answer: B
QUESTION 26
A project manager confronts a team member about the use of personal instant messaging during working
hours. This is an example of which of the following conflict resolution techniques?
A. Forcing
B. Smoothing
C. Compromise
D. Avoiding
Correct Answer: A
QUESTION 27
Which of the following are components in the communications management planning process?
A. Communications planning, information distribution, performance reporting, project implementation
B. Communications planning, information distribution, performance reporting, closing
C. Communications planning, information distribution, performance reporting, initiating
D. Communications planning, information distribution, performance reporting, manage stakeholders
Correct Answer: D
QUESTION 28
An analysis of the cost-benefit trade-offs for a project should be included as part of the:
A. Work plan
B. Risk register
C. Project charter
D. Quality plan
Correct Answer: D
QUESTION 29
A project manager of a particular project receives formal notification that a vendor has gone out of
business. New vendors with similar products at similar costs have been identified. Which of the following
should the project manager do FIRST?
A. Initiate RFQs to qualified vendors, update the project management plan and communicate the issue
with the project sponsor following the project communications plan.
B. Undertake a make-or-buy decision analysis; communicate the issue with the project sponsor following
the project communications plan.
C. Call a stakeholder meeting following the project communications plan to urgently review the project
schedule; update the project management plan.
D. Communicate the issue with the project sponsor following the project communications plan, call a
project team meeting to discuss alternatives and update the project management plan.
Correct Answer: A
QUESTION 30
In a Gantt chart, how are milestones displayed?
A. An activity with zero day duration
B. An activity with one day duration
C. Activity-on-node with a finish-to-finish precedence
D. End-to-end bar graph showing the time to complete a task
Correct Answer: A
QUESTION 31
When would a project manager have a closure meeting? (Select THREE).
A. Stage completion
B. Task completion
C. Document completion
D. Project cancellation
E. Project completion
F. Vendor cancellation
Correct Answer: ADE
QUESTION 32
Before a change request is presented to the change control board, which of the following should the
project manager do?
A. Suggest the board study the cost of the change.
B. Evaluate the affect on all other parts of the project.
C. Review the change request with the project sponsor.
D. Request team member input on the value of the change.
Correct Answer: B
QUESTION 33
Which of the following should a project manager do for a team member who does not speak the same
language?
A. Hire a translator to assist the team member in communicating.
B. Communicate with the team member using translation software.
C. Send the team member to training on the desired language.
D. Ask for a replacement team member that speaks the same language.
Correct Answer: A
QUESTION 34
A project manager is completing a project schedule network diagram using boxes to represent the project
activities that are connected by lines to show their dependencies. Which of the following tools is the project
manager using?
A. AOA
B. WBS
C. ADM
D. PDM
Correct Answer: D
QUESTION 35
A conflict has developed among two project team members. The project manager reiterates the areas of
agreement and avoids the areas of disagreement. Which of the following BEST describes this conflict
resolution technique?
A. Smoothing
B. Compromising
C. Avoiding
D. Negotiating
Correct Answer: A
QUESTION 36
Which of the following directly utilize the WBS? (Select TWO).
A. Communication plan
B. Monte Carlo technique
C. Activity estimation
D. Variance analysis
E. Resource assignment
Correct Answer: CE
QUESTION 37
— Exhibit
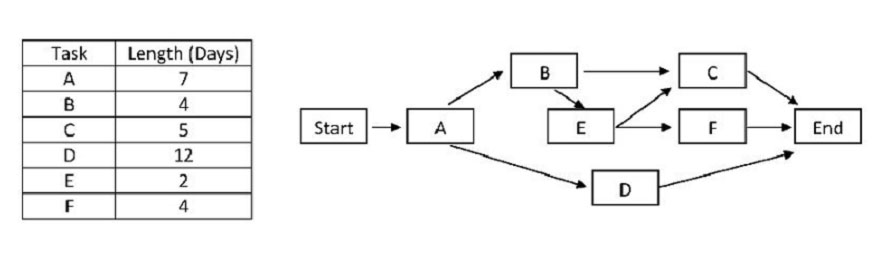
— Exhibit —
Click on the exhibit button. Which of the following is the critical path?
A. Start-A-B-E-F-end
B. Start-A-B-C-end
C. Start-A-B-E-C-end
D. Start-A-D-end
Correct Answer: D
QUESTION 38
— Exhibit
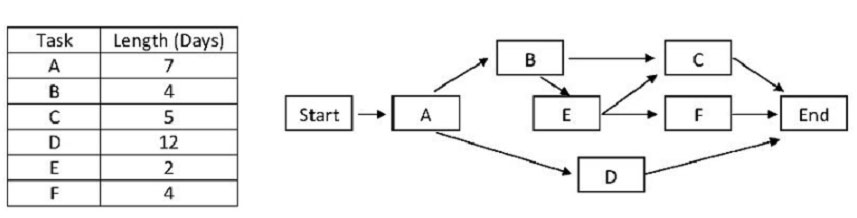
— Exhibit —
Click on the Exhibit button. Which of the following is the float of the path: start-A-D-end?
A. Zero
B. One
C. Five
D. Nineteen
Correct Answer: A
QUESTION 39
Which of the following is the BEST method to avoid staffing conflict between resource managers and
project managers?
A. Allow team members to enter the project as best fits their schedule.
B. Ask the project sponsor for team member assignments.
C. Claim the best department resources before the project starts.
D. Formally request team members early.
Correct Answer: D
QUESTION 40
After a change control board meeting, which of the following actions should the project manager do NEXT?
A. Notify the requester of the verdict.
B. Review the impact of proposed change.
C. Update the project scope statement.
D. Document the specific change request.
Correct Answer: A
QUESTION 41
A statement of work (SOW) has been heavily revised by the stakeholders. Which of the following should beimplemented to make it easier to determine how many times the document has been revised?
A. Version control
B. A document revision date
C. Approval signatures from each stakeholder
D. A change request
Correct Answer: A
QUESTION 42
Which of the following human resource outputs would a project manager use to determine a team
member’s skills?
A. Role
B. Accountability
C. Competency
D. Responsibility
Correct Answer: C
QUESTION 43
All of the following are characteristics of a project EXCEPT that it:
A. is managed by consensus.
B. is a temporary endeavor to create a unique product or service.
C. is limited by human and financial resources.
D. adheres to the triple constraint.
Correct Answer: A
QUESTION 44
Which of the following techniques can a project manager use to assist with quality planning? (Select
THREE).
A. Peer review
B. Critical Chain Method (CCM)
C. Inspection
D. Performance Evaluation and Review Technique (PERT)
E. Work Breakdown Structure (WBS)
F. Benchmarking
Correct Answer: ACF
QUESTION 45
Reviewing the results of a control chart, the project manager finds the production samples had results
inside both the upper control limit and the lower control limit. Which of the following is the BEST course of
action for the project manager based on this information?
A. The project manager should identify potential new production teams to obtain different results.
B. The project manager should create a report to outline the results for client review and request a more
generous range between limits.
C. The project manager should stop production until the processes are reviewed in full for identification of
flaws.
D. The project manager should continue following the existing process, including the measuring of
samples for tracking.
Correct Answer: D
QUESTION 46
A project manager has a project with staff in four different countries. When generating the resource
management plan, which of the following should be considered FIRST?
A. Reviewing holiday and vacation schedule with all team members.
B. Getting the email address of all the employees.
C. Locating each employee on the map in the office.
D. Understanding the international country code of all the team members.
Correct Answer: A
QUESTION 47
An approved change request has delayed the project start date without modifying the completion date. The
project sponsor has requested the project manager to pursue an option with the LOWEST initial cost.
Which of the following methods should the project manager consider?
A. Parametric estimating
B. Rolling wave planning
C. Crashing
D. Fast tracking
Correct Answer: D
QUESTION 48
The project manager has constructed a graphical chart categorically representing the frequency of each
data occurrence. This is an example of which of the following tools?
A. Histogram
B. Gantt chart
C. Ishikawa diagram
D. Control chart
Correct Answer: A
QUESTION 49
The project office has created change request templates that must be used on any corporate project.
Which of the following BEST describes this action?
A. Regulation
B. Best practice
C. Guideline
D. Standard
Correct Answer: D
QUESTION 50
The project manager has received an approved change request. Which of the following actions should the
project manager take NEXT?
A. Schedule a meeting with the change advisory board to discuss the impact of the change
B. Perform a probability and impact assessment on the approved change
C. Hold a team meeting to ensure the change is immediately implemented
D. Develop a plan to incorporate the change into the project
Correct Answer: D
Conclusion:
We shared 50 free CompTIA Project+ PK0-003 exam dumps and PK0-003 PDF to help you get started with the first step
of certification, and to easily pass the exam requires a complete selection of https://www.pass4itsure.com/pk0-003.html PDF + VCE
(100% guaranteed actual validity, 100% latest, 100% guaranteed invalid refund)
[PDF] Free CompTIA Project+ PK0-003 dumps download from Google Drive:
https://drive.google.com/open?id=1hbymsTa9IIcwUfeHZAxe8qTu_uuLobNC
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
Pass4itsure Promo Code 15% Off
related: https://www.certificationmonitor.com/latest-upload-cisco-400-101-dumps-pdf/
Easily Pass CompTIA Server+ SK0-003 exam, the latest effective SK0-003 exam dumps | 100% Free
Certificationmonitor is a free high quality blog that offers all exam dumps from pass4itsure experts. The latest effective 69
CompTIA Server+ SK0-003 exam dumps Practice test and free sharing of SK0-003 pdf, we keep an eye on the latest content to ensure that
all questions and answers are up to date. Free content allows you to progress and enhance your abilities, and if you want to easily
pass the exam to get a SK0-003 exam certificate, please select the full https://www.pass4itsure.com/sk0-003.html PDF + VCE
[PDF] Free CompTIA Server+ SK0-003 dumps download from Google Drive:
https://drive.google.com/open?id=1cfJpDphyWzitG3kE2tDheirRkitNykOS
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
Server+ (Plus) Certification | CompTIA IT Certifications:https://certification.comptia.org/certifications/server
About the exam:
CompTIA Server+ certified candidates can work in any environment because it is the only vendor-neutral certification covering the major
server platforms. It is the only industry certification that covers the latest server technologies including virtualization,
security and network-attached storage.
CompTIA Server+ certification validates the skills necessary to be a server administrator. Successful candidates will have mastered the
following concepts:
Virtualization
Storage
Security
Troubleshooting
Pass4itsure offers the latest CompTIA Server+ SK0-003 practice test free of charge (69Q&As)
Exam B
QUESTION 1
A technician has fixed a reported issue with a heavily used software program and users have verified that the program is working correctly. Which of the following
should the technician do NEXT?
A. Document the process and update the baseline.
B. Test the theory of probable cause and verify with the software vendor.
C. Establish a plan of action to be included in the business impact analysis.
D. Implement the software manufacturer workaround.
Correct Answer: A
QUESTION 2
After installing a new hard drive into a server for the purpose of mirroring the data from the first drive to the second one, the server displays an “operating system
not found” error. Which of the following should the technician do to boot the server from the original drive?
A. Replace the second drive with a hot swappable one.
B. Swap the drive boot order in the BIOS.
C. Make the second disk active under the disk management tool.
D. Rebuild the array using the hardware RAID tool at boot.
Correct Answer: B
QUESTION 3
Which of the following MUST be done when imaging a Windows Server that will be used as a template?
A. Remove software
B. Run Windows Updates
C. Update drivers
D. Sysprep
Correct Answer: D
QUESTION 4
A technician works for a company that has recently been affected by a virus. The virus entered the network by using port 6000. Port 6000 is used by an application
located on a server. The technician has been asked to block this port on all servers and computers except for the one server which uses this port.
Which of the following should the technician do?
A. Update the antivirus application
B. Install critical update security patches
C. Adjust the software firewall settings
D. Replace the current antivirus program
Correct Answer: C
QUESTION 5
A technician manages a server that contains sensitive data. The server currently has two hard drives, one hosting the operating system and other generic files and
the second hosting sensitive data. The technician needs to implement a technology that would guard against data loss for only the sensitive data, while adding
only one additional hard drive. Which of the following should the technician implement to avoid reformatting any drives?
A. RAID 0
B. RAID 1
C. RAID 3
D. RAID 5
Correct Answer: B
QUESTION 6
When planning for redundant power sources in a server deployment, which of the following should be purchased? (Select TWO).
A. RAID controllers
B. Multiple UPSs
C. Redundant cooling
D. Dual NICs
E. Redundant power supplies
Correct Answer: BE
QUESTION 7
Which of the following is an advantage of RAID 0?
A. Mirrors data
B. Redundancy
C. Speed
D. Automatic hot spare
Correct Answer: C
QUESTION 8
A technician is installing a server with sixteen 1 TB drives. They want the benefit of both speed and redundancy. Which of the following RAID configurations
should be used?
A. RAID 0
B. RAID 1
C. RAID 3D. RAID 50
Correct Answer: D
QUESTION 9
Which of the following types of UPS would be used with equipment that is very sensitive to power fluctuations?
A. Offline / Standby
B. Line interactive
C. Rackmount
D. Online / Double Conversion
Correct Answer: D
QUESTION 10
When a technician left the server room Monday evening everything was operational. When the technician returned Tuesday morning, the front bezel was off of the
mail server, and it had been powered off. Which of the following should be checked FIRST?
A. TCP/IP settings
B. RAID configuration
C. Whether the power cord is attached
D. Server room access log
Correct Answer: D
QUESTION 11
Which of the following server roles allows a server to translate fully qualified domain names into IP addresses?
A. Directory services server
B. NTP server
C. DHCP server
D. DNS server
Correct Answer: D
QUESTION 12
A technician has just finished installing a new server into a server rack. Which of the following should the technician do NEXT to complete the installation
documentation?
A. Update drivers, update operating system (e.g. Windows Update), create server baseline, create a new network diagram, update change management
procedures
B. Create server baseline, label server, store vendor-specific documentation, update network diagrams, update asset tracking information
C. Create server baseline, assign server roles, install tape drive, delete network diagram, label server, update operating system (e.g. Windows Update)
D. Install applications on server, install external drives, toss vendor-specific documentation, update network diagrams
Correct Answer: B
QUESTION 13
A small business has had unauthorized people enter their server room and damage their servers. Which of the following locks for the door would BEST prevent
unauthorized people from accessing the server room?
A. Biometric
B. Keypad
C. Barcode
D. Key lock
Correct Answer: A
QUESTION 14
A technician is troubleshooting a lack of Internet connectivity affecting their entire office. The technician suspects the issue is with their Internet Service Provider
failing to provide service. Which of the following command line tools should the technician use to BEST test this theory?
A. tracert
B. ipconfig
C. netstat
D. nslookup
Correct Answer: A
QUESTION 15
An administrator needs to install a 2U server into a rack. Which of the following shows how much space, in height, needs to be available for the server to fit in the
rack?
A. 1.75 inches (4.45 cm)
B. 2.5 inches (6.35 cm)
C. 3.5 inches (8.89 cm)
D. 4.25 inches (10.8 cm)
Correct Answer: C
QUESTION 16
A customer has purchased a triple channel memory kit containing three DDR3 RAM modules. The server the RAM is intended for only has a dual channel capable
motherboard. Which of the following is the BEST action to perform?
A. Install only two modules as the RAM has to be installed in pairs
B. Purchase one additional RAM module to make it even. Three modules will function as triple channel and the additional module will be for parityC. Purchase dual channel memory. The triple channel memory may be incompatible with the server motherboard
D. Install the RAM. Two modules will perform as dual channel and one as single channel
Correct Answer: C
QUESTION 17
Which of the following processor technologies is typically supported on current enterprise class UNIX servers but not enterprise class Windows Servers?
A. RISC
B. CISC
C. Multi-threading
D. 64-bit
Correct Answer: A
QUESTION 18
An administrator needs to connect servers to the Fiber Channel SAN. Which of the following should the administrator install in the servers to allow this
connection?
A. Riser
B. HBA
C. SCSI card
D. SAS card
Correct Answer: B
QUESTION 19
An administrator creates a new directory then shares it on the Windows server. The administrator sets the permissions for everyone to “Modify” but users report
they are unable to create or delete documents.
Which of the following is the cause?
A. The administrator forgot to change the share permissions
B. The users were not part of the “Everyone” built in group
C. The administrator shared the files but not the folder
D. “Modify” only allows users to change existing documents
Correct Answer: A
QUESTION 20
An administrator has just finished physically replacing the system board in a Windows domain controller. Which of the following must be done before booting the
server back into Windows?
A. Update the time and date in the BIOS.
B. Update the firmware on the SCSI controller.
C. Update the firmware to the latest version.
D. Configure IPMI on the new board.
Correct Answer: A
QUESTION 21
A server was recently updated with the latest antivirus definitions. Immediately after the update, the server begins to report `file not found’ errors for a mission
critical application. Which of the following is the MOST likely reason for this?
A. The update was done incorrectly and now the server needs to be restarted.
B. The update has discovered viruses on the server and removed those virus files.
C. The update requires a reboot for the files to process correctly.
D. The update has quarantined files that are false positives.
Correct Answer: D
QUESTION 22
Which of the following are the BEST tools to test connectivity between two hosts? (Select TWO).
A. netstat
B. nslookup
C. ipconfig
D. traceroute
E. pathping
Correct Answer: DE
QUESTION 23
An administrator is overseeing the backup process and tapes utilized by a former employee. Which of the following is the BEST way for the administrator to
proceed?
A. Utilize differential backups.
B. Verify the tape drives are functional.
C. Verify that the backups are functional.
D. Utilize incremental backups.
Correct Answer: C
QUESTION 24
A staff member reports that they cannot access the shared folder on the network; however, other staff members are reporting that they can access the shared
folder. Which of the following is the BEST way to identify the problem?A. The administrator should monitor all traffic between the staff member and the server.
B. The administrator should reconfigure the RAID configuration to allow more space.
C. The administrator should map a drive using the net use command.
D. The administrator should allow the staff member to use a USB drive.
Correct Answer: C
QUESTION 25
An administrator needs to maintain 1TB of storage for mission critical application data. Fault tolerance and performance are the most important considerations.
Cost is not a factor at all. Which of the following RAID configurations would be the BEST choice to meet the criteria for the storage array?
A. RAID 6 with six 250GB hard drives
B. RAID 10 with eight 250GB hard drives
C. RAID 5 with five 250GB hard drives
D. RAID 0 with eight 250GB hard drives
Correct Answer: B
QUESTION 26
Which of the following storage interface protocols has the FASTEST speeds?
A. Ultra2 SCSI
B. SATA
C. Ultra320 SCSI
D. SAS
Correct Answer: D
QUESTION 27
Which of the following is a benefit of application virtualization?
A. The need for multiple licenses of any software is unnecessary.
B. Interoperability of disparate programs is easily attained.
C. Server loads are greatly reduced from lowered traffic.
D. Applications are easily accessible from anywhere on the LAN.
Correct Answer: D
QUESTION 28
Which of the following is the MOST likely to cause a server power supply fan to fail but allows the power supply to still be functional?
A. Dust
B. Power Surge
C. Excessive humidity
D. High temperatures
Correct Answer: A
QUESTION 29
A server has lost communication to its drives located on a fiber channel SAN. An administrator notices that the indicator lights on both the HBA and the SAN
switch are not lit. Which of the following are the MOST likely causes of the problem? (Select THREE).
A. Failed HBA
B. Failed switch port
C. Faulty fiber cable
D. Faulty driver
E. Failed hard drives
F. Faulty configuration
Correct Answer: ABC
QUESTION 30
A Windows server has rebooted by itself several times. There are several functioning non- Windows servers in the same rack that are connected to the same
uninterruptible power supply (UPS). Which of the following is the MOST likely cause of the reboots?
A. The UPS is malfunctioning.
B. The user traffic to the server is too high.
C. A BSOD is occurring.
D. The non-Windows servers cannot be located on the same UPS as the Windows server.
Correct Answer: C
QUESTION 31
A server has had a drive fail in its storage RAID set. The administrator swaps the drive with a replacement and the RAID set does not automatically start to rebuild
the replaced drive. Which of the following utilities would MOST likely be used to initialize the rebuilding of the replacement drive?
A. Net use
B. Array management
C. Fdisk
D. Disk Management Plug-in
Correct Answer: B
QUESTION 32
An administrator installs a new network card in a properly functioning DC. During the Windows boot up process the DC bluescreens. Which of the following is theNEXT step?
A. Press F8 and boot to Directory Services Restore Mode.
B. Press F8 and boot to Last Known Good Configuration.
C. Reboot the server again.
D. Press F8 and boot to Safe Mode.
Correct Answer: B
QUESTION 33
The staff is not able to access a database server. The server has an ‘Operating System not found’ error and is set to boot from a fiber channel SAN. All other
database servers are set to boot from the SAN and access the same switch and data as this database server. Which of the following is the MOST likely cause of
the problem?
A. The SAN is offline
B. Fiber channel switch
C. Multiple failed drives in the SAN
D. HBA
Correct Answer: D
QUESTION 34
After a critical service failure occurs the server keeps rebooting every fifteen minutes not giving an administrator enough time to troubleshoot the failure. Which of
the following does the administrator need to do to allow enough time to work on the system to troubleshoot the problem?
A. Modify boot.ini file
B. Disable automatic reboot on service
C. Press F6 at boot up
D. Clear cache
Correct Answer: B
QUESTION 35
Which of the following is an example of a private IP address?
A. 191.168.5.4
B. 111.12.53.2
C. 5.2.4.4
D. 169.254.15.28
Correct Answer: D
QUESTION 36
Which of the following ports should be allowed through a firewall for Telnet to function?
A. 23
B. 25
C. 50
D. 110
Correct Answer: A
QUESTION 37
Given four drives, which of the following RAID levels will allow for the GREATEST performance?
A. RAID 0
B. RAID 5
C. RAID 6
D. RAID 10
Correct Answer: A
QUESTION 38
Which of the following RAID levels would be appropriate given two drives and a need for fault tolerance?
A. RAID 0
B. RAID 1
C. RAID 5
D. RAID 10
Correct Answer: B
QUESTION 39
Which of the following MOST correctly describes a hot spare?
A. A drive assigned to an array that will only hold parity information used for rebuilding a failed array drive.
B. An external hard drive to which all data is replicated to for recovery in the event of a failure.
C. A drive assigned to an array that will automatically be used to rebuild a failed array drive.
D. An extra drive purchased and stored in the parts cabinet to replace failed drives.
Correct Answer: C
QUESTION 40
Which of the following ports MUST be open on the firewall to allow remote desktop connection and remote assistance traffic through?A.21
B. 443
C. 3389
D. 8080
Correct Answer: C
QUESTION 41
As a best practice, when should the server be rebooted to apply the reboot required patches?
A. During scheduled downtime
B. Once a year
C. As soon as the patches are finished installing
D. At the same time every day
Correct Answer: A
QUESTION 42
When installing a server in a rack, which of the following locations describes where in the rack a server should be installed?
A. On the very bottom U of the rack, with the UPS above the server
B. In the middle of the rack to help balance the rack
C. Closest to the bottom of the rack, above heavier equipment
D. On the very top U of the rack, with the UPS directly below it
Correct Answer: C
QUESTION 43
Which of the following is the BEST way to make sure the network printer is automatically installed when the user logs on?
A. Log onto the user’s computer as a local administrator and install the printer.
B. Make sure the user has permission to print to the printer.
C. Create and implement a logon script.
D. After the user has logged on, install the printer.
Correct Answer: C
QUESTION 44
Which of the following server types stores users’ home directory folders?
A. Application
B. File
C. Directory services
D. Print
Correct Answer: B
QUESTION 45
Which of the following cable types should be used to achieve Gigabit Ethernet speed?
A. CAT5
B. CAT3
C. CAT6
D. Thicknet
Correct Answer: C
QUESTION 46
After performing the initial steps in installing the server OS from a DVD-ROM, the server reboots and goes back into the setup wizard. Which of the following is the
MOST likely cause for this problem?
A. The DVD-ROM drive has failed.
B. An installation file copied from the DVD to the hard drive is corrupt.
C. Faulty OS installation DVD.
D. Incorrect boot sequence in the BIOS.
Correct Answer: D
QUESTION 47
When disposing of data, which of the following should be considered FIRST?
A. Company policy requirements
B. Local legal requirements
C. Storage requirements
D. Disposal requirements
Correct Answer: B
QUESTION 48
Which of the following ports does RDP use by default?
A. 23
B. 902
C. 1677
D. 3389
Correct Answer: D
QUESTION 49
Which of the following can be used when installing the OS without a boot disk?
A. ZFS
B. VMFS
C. PXE
D. PBX
Correct Answer: C
QUESTION 50
The administrator has just installed a new memory module into the server. Now, the server is not showing the new memory. Which of the following should the
administrator perform FIRST?
A. System reboot
B. Reseat the memory
C. Install the latest firmware
D. Install the latest driver
Correct Answer: B
QUESTION 51
Management has asked the server technician to deploy fourteen new servers with newly-released operating systems in the virtual environment for testing
purposes. Which of the following is the FASTEST way to do this?
A. Create a template of an existing server and deploy the fourteen images from that server.
B. Create a server template, and deploy all fourteen servers from this template.
C. Create one server, create a backup image, and restore thirteen servers from the image.
D. Create each server individually.
Correct Answer: B
QUESTION 52
Which of the following should be done FIRST when troubleshooting a problem?
A. Test the theory to determine the cause
B. Perform a root cause analysis
C. Establish a plan of action
D. Document outcomes
Correct Answer: A
QUESTION 53
A datacenter director implements a new security measure in response to multiple equipment thefts from the datacenter. The new security measure requires
people entering or leaving the datacenter to go through an extra secure area. Once entering the area people must present two forms of authentication to leave.
Which of the following security measures does this describe?
A. Mantrap
B. RFID cards
C. Defense in depth
D. Biometrics
Correct Answer: A
QUESTION 54
A system administrator needs to provision storage for a 200GB database. The database must have extremely low seek time. Which of the following is the BEST
solution?
A. A JBOD
B. A RAID 50 array
C. A NAS
D. A single SSD
Correct Answer: D
QUESTION 55
Which of the following defines memory interleaving?
A. The distribution of data written across all the memory DIMMs and the L1 cache
B. The distribution of data written across all the memory DIMMs in one bank
C. The distribution of data written across all the memory DIMMs and the processor
D. The distribution of data written across all the memory DIMMs and the L2 cache
Correct Answer: B
QUESTION 56
When troubleshooting a problem on a server, which of the following is the industry best practice?
A. Reseat all components
B. Replace the memory and CPU
C. Test each component one at a time
D. Reinstall TCP/IP
Correct Answer: C
QUESTION 57
Security patches that were issued to address a security flaw in the database server software have failed to install. All other OS security patches applied
successfully. Which of the following is the MOST likely cause of the failure?
A. Database patches typically require a reinstall of the database server software.
B. The server was unavailable during the patch window.
C. The OS patches and database patches cannot be deployed together.
D. The account used does not have permission to patch the database software.
Correct Answer: D
QUESTION 58
Which of the following protocols define the rules and processes used to transmit and receive block storage applications over TCP/IP?
A. iSCSI
B. VoIP
C. Distributed Applications over IP
D. HTTPS
Correct Answer: A
QUESTION 59
Which of the following is the BEST to use when securing fiber cables and preventing damage?
A. Zip ties
B. Twist ties
C. Black electrical tape
D. Velcro cable straps
Correct Answer: D
QUESTION 60
An administrator has been instructed to add four additional drives to a server configured with RAID 5. The server is using 146GB drives for the data. Without
changing the configuration, how much additional data space would be available if the administrator purchased 300GB drives and added them to the existing
array?
A. 438GB
B. 584GB
C. 900GB
D. 1200GB
Correct Answer: B
QUESTION 61
Which of the following describes the difference between SATA and PATA?
A. SATA operates on a single channel.
B. PATA devices have three channels.
C. PATA devices have their own channel whereas SATA does not.
D. SATA devices have their own channel whereas PATA does not.
Correct Answer: D
QUESTION 62
When troubleshooting a problem on a server, which of the following is the industry best practice?
A. Reseat all components
B. Replace the memory and CPU
C. Test each component one at a time
D. Reinstall TCP/IP
Correct Answer: C
QUESTION 63
An administrator is required to maintain space for 750GB of user data. Which of the following is the BEST option available to the administrator?
A. Create a RAID 5 array using five 200GB disks.
B. Create a JBOD using four 200GB disks.
C. Create a RAID 1 array using six 200GB disks.
D. Create a RAID 5 array using three 200GB disks.
Correct Answer: A
QUESTION 64
Users can only access external websites. Which of the following is the MOST likely cause of this problem?
A. The incorrect gateway address is being provided to the workstation.
B. DHCP is not providing workstations with the proper subnet mask.
C. The DNS cache was cleared.
D. The internal zone was deleted.
Correct Answer: D
QUESTION 65
An administrator needs to configure a server to restrict mail traffic to an application server for security reasons. Which of the following techniques can be used to
manage this?
A. PAT
B. ACLs
C. Subnet masking
D. Port blocking
Correct Answer: B
QUESTION 66
Which of the following is the MOST critical environmental consideration when determining the location of a server?
A. Ease of physical access
B. Cable management
C. Height from the floor
D. Temperature of the room
Correct Answer: D
QUESTION 67
A company has 100GB of data that needs to be automatically backed up daily, and needs to be stored for 20 years. Which of the following backup media is the
BEST solution for archiving the server data?
A. Tape
B. SAN
C. Flash
D. Optical
Correct Answer: A
QUESTION 68
Which of the following storage technologies connects by TCP/IP and is separate from the company’s LAN?
A. Tape library
B. NAS
C. Optical jukebox
D. SAN
Correct Answer: D
QUESTION 69
Users report slow performance when saving files on a server with a RAID 5 array, but not when reading files from that server. Which of the following is the MOST
likely cause?
A. Mismatched drives
B. Bad sectors
C. Cache battery failure
D. Disk drive failure
Correct Answer: C
Conclusion:
We shared 69 free CompTIA Server+ SK0-003 exam dumps and SK0-003 PDF to help you get started with the first step
of certification, and to easily pass the exam requires a complete selection of https://www.pass4itsure.com/sk0-003.html PDF + VCE
(100% guaranteed actual validity, 100% latest, 100% guaranteed invalid refund)
[PDF] Free CompTIA Server+ SK0-003 dumps download from Google Drive:
https://drive.google.com/open?id=1cfJpDphyWzitG3kE2tDheirRkitNykOS
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
Pass4itsure Promo Code 15% Off
related: https://www.certificationmonitor.com/high-quality-cisco-300-170-dumps-dcvai-exam/
Easily Pass CompTIA security+ sy0-401 exam, the latest effective sy0-401 exam dumps | 100% Free
Certificationmonitor is a free high quality blog that offers all exam dumps from pass4itsure experts. The latest effective 131 CompTIA
security+ sy0-401 exam dumps Practice test and free sharing of sy0-401 pdf, we keep an eye on the latest content to ensure that
all questions and answers are up to date. Free content allows you to progress and enhance your abilities, and if you want to easily
pass the exam to get a sy0-401 exam certificate, please select the full https://www.pass4itsure.com/sy0-401.html PDF + VCE
[PDF] Free CompTIA Security+ SY0-401 dumps download from Google Drive:
https://drive.google.com/open?id=1fNUvuARTsqEpjU2G_fxVaZCoDDWhG1sd
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
CompTIA Security+ Certification:https://certification.comptia.org/certifications/security
Pass4itsure offers the latest CompTIA Security+ SY0-401 practice test free of charge (141Q&As)
QUESTION 1
Ann is the data owner of financial records for a company. She has requested that she have the ability to assign read and write privileges to her folders. The network administrator is tasked with setting up the initial access control system and
handing Ann’s administrative capabilities. Which of the following systems should be deployed?
A. Role-based
B. Mandatory
C. Discretionary
D. Rule-based
Correct Answer: C
QUESTION 2
A password history value of three means which of the following?
A. Three different passwords are used before one can be reused.
B. A password cannot be reused once changed for three years.
C. After three hours a password must be re-entered to continue.
D. The server stores passwords in the database for three days.
Correct Answer: A
QUESTION 3
A security administrator has installed a new KDC for the corporate environment. Which of the following authentication protocols is the security administrator planning to implement across the organization?
A. LDAP
B. RADIUS
C. Kerberos
D. XTACACS
Correct Answer: C
QUESTION 4
A system administrator is using a packet sniffer to troubleshoot remote authentication. The administrator detects a device trying to communicate to TCP port 49. Which of the following authentication methods is MOST likely being attempted?
A. RADIUS
B. TACACS+
C. Kerberos
D. LDAP
Correct Answer: B
QUESTION 5
Which of the following authentication services requires the use of a ticket-granting ticket (TGT) server in order to complete the authentication process?
A. TACACS+
B. Secure LDAP
C. RADIUS
D. Kerberos
Correct Answer: D
QUESTION 6
An organization has introduced token-based authentication to system administrators due to risk of password compromise. The tokens have a set of numbers that automatically change every 30 seconds. Which of the following type of
authentication mechanism is this?
A. TOTP
B. Smart card
C. CHAP
D. HOTP
Correct Answer: A
QUESTION 7
The security department has implemented a new laptop encryption product in the environment. The product requires one user name and password at the time of boot up and also another password after the operating system has finished
loading. This setup is using which of the following authentication types?
A. Two-factor authentication
B. Single sign-on
C. Multifactor authentication
D. Single factor authentication
Correct Answer: D
QUESTION 8
A company hired Joe, an accountant. The IT administrator will need to create a new account for
Joe. The company uses groups for ease of management and administration of user accounts.
Joe will need network access to all directories, folders and files within the accounting department.
Which of the following configurations will meet the requirements?
A. Create a user account and assign the user account to the accounting group.
B. Create an account with role-based access control for accounting.
C. Create a user account with password reset and notify Joe of the account creation.
D. Create two accounts: a user account and an account with full network administration rights.
Correct Answer: B
QUESTION 9
Which of the following access controls enforces permissions based on data labeling at specific levels?
A. Mandatory access control
B. Separation of duties access control
C. Discretionary access control
D. Role based access control
Correct Answer: A
QUESTION 10
A system administrator needs to ensure that certain departments have more restrictive controls to their shared folders than other departments. Which of the following security controls would be implemented to restrict those departments?
A. User assigned privileges
B. Password disablement
C. Multiple account creation
D. Group based privileges
Correct Answer: D
QUESTION 11
Ann was reviewing her company’s event logs and observed several instances of GUEST accessing the company print server, file server, and archive database. As she continued to investigate, Ann noticed that it seemed to happen at random
intervals throughout the day, but mostly after the weekly automated patching and often logging in at the same time. Which of the following would BEST mitigate this issue?
A. Enabling time of day restrictions
B. Disabling unnecessary services
C. Disabling unnecessary accounts
D. Rogue machine detection
Correct Answer: C
QUESTION 12
An administrator implements SELinux on a production web server. After implementing this, the web server no longer serves up files from users’ home directories. To rectify this, the administrator creates a new policy as the root user. This is
an example of which of the following? (Select TWO).A. Enforcing SELinux in the OS kernel is role-based access control
B. Enforcing SELinux in the OS kernel is rule-based access control
C. The policy added by the root user is mandatory access control
D. Enforcing SELinux in the OS kernel is mandatory access control
E. The policy added by the root user is role-based access control
F. The policy added by the root user is rule-based access control
Correct Answer: DF
QUESTION 13
Jane, a security administrator, has been tasked with explaining authentication services to the company’s management team. The company runs an active directory infrastructure. Which of the following solutions BEST relates to the host
authentication protocol within the company’s environment?
A. Kerberos
B. Least privilege
C. TACACS+
D. LDAP
Correct Answer: A
QUESTION 14
Which of the following is an example of multifactor authentication?
A. Credit card and PIN
B. Username and password
C. Password and PIN
D. Fingerprint and retina scan
Correct Answer: A
QUESTION 15
Which of the following should be used to authenticate and log connections from wireless users connecting with EAP-TLS?
A. Kerberos
B. LDAP
C. SAML
D. RADIUS
Correct Answer: D
QUESTION 16
Which of the following authentication services uses a ticket granting system to provide access?
A. RADIUS
B. LDAP
C. TACACS+
D. Kerberos
Correct Answer: D
QUESTION 17
Which of the following was based on a previous X.500 specification and allows either unencrypted authentication or encrypted authentication through the use of TLS?
A. Kerberos
B. TACACS+
C. RADIUS
D. LDAP
Correct Answer: D
QUESTION 18
Which of the following types of security services are used to support authentication for remote users and devices?
A. Biometrics
B. HSM
C. RADIUS
D. TACACS
Correct Answer: C
QUESTION 19
A hacker has discovered a simple way to disrupt business for the day in a small company which relies on staff working remotely. In a matter of minutes the hacker was able to deny remotely working staff access to company systems with a
script. Which of the following security controls is the hacker exploiting?
A. DoS
B. Account lockout
C. Password recovery
D. Password complexity
Correct Answer: B
QUESTION 20
A technician is reviewing the logical access control method an organization uses. One of the senior managers requests that the technician prevent staff members from logging on during nonworking days. Which of the following should the
technician implement to meet managements request?
A. Enforce Kerberos
B. Deploy smart cards
C. Time of day restrictions
D. Access control lists
Correct Answer: C
QUESTION 21
Which of the following is the BEST reason for placing a password lock on a mobile device?
A. Prevents an unauthorized user from accessing owner’s data
B. Enables remote wipe capabilities
C. Stops an unauthorized user from using the device again
D. Prevents an unauthorized user from making phone calls
Correct Answer: A
QUESTION 22
Which of the following is mainly used for remote access into the network?
A. XTACACS
B. TACACS+
C. Kerberos
D. RADIUS
Correct Answer: D
QUESTION 23
Which of the following protocols uses TCP instead of UDP and is incompatible with all previous versions?
A. TACACS
B. XTACACS
C. RADIUS
D. TACACS+
Correct Answer: D
QUESTION 24
The system administrator is tasked with changing the administrator password across all 2000 computers in the organization. Which of the following should the system administrator implement to accomplish this task?A. A security group
B. A group policy
C. Key escrow
D. Certificate revocation
Correct Answer: B
QUESTION 25
The IT department has setup a website with a series of questions to allow end users to reset their own accounts. Which of the following account management practices does this help?
A. Account Disablements
B. Password Expiration
C. Password Complexity
D. Password Recovery
Correct Answer: D
QUESTION 26
Use of group accounts should be minimized to ensure which of the following?
A. Password security
B. Regular auditing
C. Baseline management
D. Individual accountability
Correct Answer: D
QUESTION 27
One of the most basic ways to protect the confidentiality of data on a laptop in the event the device is physically stolen is to implement which of the following?
A. File level encryption with alphanumeric passwords
B. Biometric authentication and cloud storage
C. Whole disk encryption with two-factor authentication
D. BIOS passwords and two-factor authentication
Correct Answer: C
QUESTION 28
A security analyst implemented group-based privileges within the company active directory. Which of the following account management techniques should be undertaken regularly to ensure least privilege principles?
A. Leverage role-based access controls.
B. Perform user group clean-up.
C. Verify smart card access controls.
D. Verify SHA-256 for password hashes.
Correct Answer: B
QUESTION 29
An internal auditing team would like to strengthen the password policy to support special characters. Which of the following types of password controls would achieve this goal?
A. Add reverse encryption
B. Password complexity
C. Increase password length
D. Allow single sign on
Correct Answer: B
QUESTION 30
Which of the following is best practice to put at the end of an ACL?
A. Implicit deny
B. Time of day restrictions
C. Implicit allow
D. SNMP string
Correct Answer: A
QUESTION 31
Ann, a security administrator, wishes to replace their RADIUS authentication with a more secure protocol, which can utilize EAP. Which of the following would BEST fit her objective?
A. CHAP
B. SAML
C. Kerberos
D. Diameter
Correct Answer: D
QUESTION 32
Jane, a security administrator, needs to implement a secure wireless authentication method that uses a remote RADIUS server for authentication.
Which of the following is an authentication method Jane should use?
A. WPA2-PSK
B. WEP-PSK
C. CCMP
D. LEAP
Correct Answer: D
QUESTION 33
A network administrator is configuring access control for the sales department which has high employee turnover. Which of the following is BEST suited when assigning user rights to individuals in the sales department?
A. Time of day restrictions
B. Group based privileges
C. User assigned privileges
D. Domain admin restrictions
Correct Answer: B
QUESTION 34
A security technician is working with the network firewall team to implement access controls at the company’s demarc as part of the initiation of configuration management processes. One of the network technicians asks the security
technician to explain the access control type found in a firewall. With which of the following should the security technician respond?
A. Rule based access control
B. Role based access control
C. Discretionary access control
D. Mandatory access control
Correct Answer: A
QUESTION 35
A security administrator has been tasked to ensure access to all network equipment is controlled by a central server such as TACACS+. This type of implementation supports which of the following risk mitigation strategies?
A. User rights and permissions review
B. Change management
C. Data loss prevention
D. Implement procedures to prevent data theft
Correct Answer: A
QUESTION 36
Which of the following is an XML based open standard used in the exchange of authentication and authorization information between different parties?
A. LDAP
B. SAMLC. TACACS+
D. Kerberos
Correct Answer: B
QUESTION 37
The security manager wants to unify the storage of credential, phone numbers, office numbers, and address information into one system. Which of the following is a system that will support the requirement on its own?
A. LDAP
B. SAML
C. TACACS
D. RADIUS
Correct Answer: A
QUESTION 38
LDAP and Kerberos are commonly used for which of the following?
A. To perform queries on a directory service
B. To store usernames and passwords for Federated Identity
C. To sign SSL wildcard certificates for subdomains
D. To utilize single sign-on capabilities
Correct Answer: D
QUESTION 39
A user reports being unable to access a file on a network share. The security administrator determines that the file is marked as confidential and that the user does not have the appropriate access level for that file. Which of the following is
being implemented?
A. Mandatory access control
B. Discretionary access control
C. Rule based access control
D. Role based access control
Correct Answer: A
QUESTION 40
Users report that they are unable to access network printing services. The security technician checks the router access list and sees that web, email, and secure shell are allowed. Which of the following is blocking network printing?
A. Port security
B. Flood guards
C. Loop protection
D. Implicit deny
Correct Answer: D
QUESTION 41
Ann has recently transferred from the payroll department to engineering. While browsing file shares, Ann notices she can access the payroll status and pay rates of her new coworkers. Which of the following could prevent this scenario from
occurring?
A. Credential management
B. Continuous monitoring
C. Separation of duties
D. User access reviews
Correct Answer: D
QUESTION 42
A security administrator is tackling issues related to authenticating users at a remote site. There have been a large number of security incidents that resulted from either tailgating or impersonation of authorized users with valid credentials. The
security administrator has been told to implement multifactor authentication in order to control facility access. To secure access to the remote facility, which of the following could be implemented without increasing the amount of space
required at the entrance?
A. MOTD challenge and PIN pad
B. Retina scanner and fingerprint reader
C. Voice recognition and one-time PIN token
D. One-time PIN token and proximity reader
Correct Answer: C
QUESTION 43
A security administrator wants to check user password complexity. Which of the following is the
BEST tool to use?
A. Password history
B. Password logging
C. Password cracker
D. Password hashing
Correct Answer: C
QUESTION 44
Which of the following controls mitigates the risk of Matt, an attacker, gaining access to a company network by using a former employee’s credential?
A. Account expiration
B. Password complexity
C. Account lockout
D. Dual factor authentication
Correct Answer: A
QUESTION 45
An organizations’ security policy requires that users change passwords every 30 days. After a security audit, it was determined that users were recycling previously used passwords. Which of the following password enforcement policies
would have mitigated this issue?
A. Password history
B. Password complexity
C. Password length
D. Password expiration
Correct Answer: A
QUESTION 46
The systems administrator notices that many employees are using passwords that can be easily guessed or are susceptible to brute force attacks. Which of the following would BEST mitigate this risk?
A. Enforce password rules requiring complexity.
B. Shorten the maximum life of account passwords.
C. Increase the minimum password length.
D. Enforce account lockout policies.
Correct Answer: A
QUESTION 47
When Ann an employee returns to work and logs into her workstation she notices that, several desktop configuration settings have changed. Upon a review of the CCTV logs, it is determined that someone logged into Ann’s workstation.
Which of the following could have prevented this from happening?
A. Password complexity policy
B. User access reviews
C. Shared account prohibition policy
D. User assigned permissions policy
Correct Answer: A
QUESTION 48
Which of the following allows a network administrator to implement an access control policy based on individual user characteristics and NOT on job function?A. Attributes based
B. Implicit deny
C. Role based
D. Rule based
Correct Answer: A
QUESTION 49
Which of the following presents the STRONGEST access control?
A. MAC
B. TACACS
C. DAC
D. RBAC
Correct Answer: A
QUESTION 50
Ann is a member of the Sales group. She needs to collaborate with Joe, a member of the IT group, to edit a file. Currently, the file has the following permissions:
Ann:read/write
Sales Group:read
IT Group:no access
If a discretionary access control list is in place for the files owned by Ann, which of the following would be the BEST way to share the file with Joe?
A. Add Joe to the Sales group.
B. Have the system administrator give Joe full access to the file.
C. Give Joe the appropriate access to the file directly.
D. Remove Joe from the IT group and add him to the Sales group.
Correct Answer: C
QUESTION 51
A security administrator implements access controls based on the security classification of the data and need-to-know information. Which of the following BEST describes this level of access control?
A. Implicit deny
B. Role-based Access Control
C. Mandatory Access Controls
D. Least privilege
Correct Answer: C
QUESTION 52
A group policy requires users in an organization to use strong passwords that must be changed every 15 days. Joe and Ann were hired 16 days ago. When Joe logs into the network, he is prompted to change his password; when Ann logs
into the network, she is not prompted to change her password. Which of the following BEST explains why Ann is not required to change her password?
A. Ann’s user account has administrator privileges.
B. Joe’s user account was not added to the group policy.
C. Ann’s user account was not added to the group policy.
D. Joe’s user account was inadvertently disabled and must be re-created.
Correct Answer: C
QUESTION 53
Which of the following authentication services should be replaced with a more secure alternative?
A. RADIUS
B. TACACS
C. TACACS+
D. XTACACS
Correct Answer: B
QUESTION 54
Which of the following security concepts can prevent a user from logging on from home during the weekends?
A. Time of day restrictions
B. Multifactor authentication
C. Implicit deny
D. Common access card
Correct Answer: A
QUESTION 55
Several employee accounts appear to have been cracked by an attacker. Which of the following should the security administrator implement to mitigate password cracking attacks? (Select TWO).
A. Increase password complexity
B. Deploy an IDS to capture suspicious logins
C. Implement password history
D. Implement monitoring of logins
E. Implement password expiration
F. Increase password length
Correct Answer: AF
QUESTION 56
A security technician has been asked to recommend an authentication mechanism that will allow users to authenticate using a password that will only be valid for a predefined time interval. Which of the following should the security technician
recommend?
A. CHAP
B. TOTP
C. HOTP
D. PAP
Correct Answer: B
QUESTION 57
Privilege creep among long-term employees can be mitigated by which of the following procedures?
A. User permission reviews
B. Mandatory vacations
C. Separation of duties
D. Job function rotation
Correct Answer: A
QUESTION 58
Human Resources suspect an employee is accessing the employee salary database. The administrator is asked to find out who it is. In order to complete this task, which of the following is a security control that should be in place?
A. Shared accounts should be prohibited.
B. Account lockout should be enabled
C. Privileges should be assigned to groups rather than individuals
D. Time of day restrictions should be in use
Correct Answer: A
QUESTION 59
Which of the following is a BEST practice when dealing with user accounts that will only need to be active for a limited time period?
A. When creating the account, set the account to not remember password history.
B. When creating the account, set an expiration date on the account.
C. When creating the account, set a password expiration date on the account.D. When creating the account, set the account to have time of day restrictions.
Correct Answer: B
QUESTION 60
A company requires that a user’s credentials include providing something they know and something they are in order to gain access to the network. Which of the following types of authentication is being described?
A. Biometrics
B. Kerberos
C. Token
D. Two-factor
Correct Answer: D
QUESTION 61
An administrator discovers that many users have used their same passwords for years even though the network requires that the passwords be changed every six weeks. Which of the following, when used together, would BEST prevent
users from reusing their existing password? (Select TWO).
A. Length of password
B. Password history
C. Minimum password age
D. Password expiration
E. Password complexity
F. Non-dictionary words
Correct Answer: BC
QUESTION 62
RADIUS provides which of the following?
A. Authentication, Authorization, Availability
B. Authentication, Authorization, Auditing
C. Authentication, Accounting, Auditing
D. Authentication, Authorization, Accounting
Correct Answer: D
QUESTION 63
In order for network monitoring to work properly, you need a PC and a network card running in what mode?
A. Launch
B. Exposed
C. Promiscuous
D. Sweep
Correct Answer: C
QUESTION 64
Users require access to a certain server depending on their job function. Which of the following would be the MOST appropriate strategy for securing the server?
A. Common access card
B. Role based access control
C. Discretionary access control
D. Mandatory access control
Correct Answer: B
QUESTION 65
A recent audit of a company’s identity management system shows that 30% of active accounts belong to people no longer with the firm. Which of the following should be performed to help avoid this scenario? (Select TWO).
A. Automatically disable accounts that have not been utilized for at least 10 days.
B. Utilize automated provisioning and de-provisioning processes where possible.
C. Request that employees provide a list of systems that they have access to prior to leaving the firm.
D. Perform regular user account review / revalidation process.
E. Implement a process where new account creations require management approval.
Correct Answer: BD
QUESTION 66
A company with a US-based sales force has requested that the VPN system be configured to authenticate the sales team based on their username, password and a client side certificate.
Additionally, the security administrator has restricted the VPN to only allow authentication from the US territory. How many authentication factors are in use by the VPN system?
A. 1
B. 2
C. 3
D. 4
Correct Answer: C
QUESTION 67
A network administrator has a separate user account with rights to the domain administrator group. However, they cannot remember the password to this account and are not able to login to the server when needed. Which of the following is
MOST accurate in describing the type of issue the administrator is experiencing?
A. Single sign-on
B. Authorization
C. Access control
D. Authentication
Correct Answer: D
QUESTION 68
A user attempting to log on to a workstation for the first time is prompted for the following information before being granted access: username, password, and a four-digit security pin that was mailed to him during account registration. This is
an example of which of the following?
A. Dual-factor authentication
B. Multifactor authentication
C. Single factor authentication
D. Biometric authentication
Correct Answer: C
QUESTION 69
After a recent internal audit, the security administrator was tasked to ensure that all credentials must be changed within 90 days, cannot be repeated, and cannot contain any dictionary words or patterns. All credentials will remain enabled
regardless of the number of attempts made. Which of the following types of user account options were enforced? (Select TWO).
A. Recovery
B. User assigned privileges
C. Lockout
D. Disablement
E. Group based privileges
F. Password expiration
G. Password complexity
Correct Answer: FG
QUESTION 70
Which of the following is the difference between identification and authentication of a user?
A. Identification tells who the user is and authentication tells whether the user is allowed to logon to a system.
B. Identification tells who the user is and authentication proves it.
C. Identification proves who the user is and authentication is used to keep the users data secure.
D. Identification proves who the user is and authentication tells the user what they are allowed to do.
Correct Answer: B
QUESTION 71
Sara, a security manager, has decided to force expiration of all company passwords by the close of business day. Which of the following BEST supports this reasoning?
A. A recent security breach in which passwords were cracked.
B. Implementation of configuration management processes.
C. Enforcement of password complexity requirements.
D. Implementation of account lockout procedures.
Correct Answer: A
QUESTION 72
Which of the following security benefits would be gained by disabling a terminated user account rather than deleting it?
A. Retention of user keys
B. Increased logging on access attempts
C. Retention of user directories and files
D. Access to quarantined files
Correct Answer: A
QUESTION 73
Ann, a security administrator at a call center, has been experiencing problems with users intentionally installing unapproved and occasionally malicious software on their computers. Due to the nature of their jobs, Ann cannot change their
permissions. Which of the following would BEST alleviate her concerns?
A. Deploy a HIDS suite on the users’ computers to prevent application installation.
B. Maintain the baseline posture at the highest OS patch level.
C. Enable the pop-up blockers on the users’ browsers to prevent malware.
D. Create an approved application list and block anything not on it.
Correct Answer: D
QUESTION 74
A security administrator has deployed all laptops with Self Encrypting Drives (SED) and enforces key encryption. Which of the following represents the greatest threat to maintaining data confidentiality with these devices?
A. Full data access can be obtained by connecting the drive to a SATA or USB adapter bypassing the SED hardware.
B. A malicious employee can gain the SED encryption keys through software extraction allowing access to other laptops.
C. If the laptop does not use a Secure Boot BIOS, the SED hardware is not enabled allowing full data access.
D. Laptops that are placed in a sleep mode allow full data access when powered back on.
Correct Answer: D
QUESTION 75
A company plans to expand by hiring new engineers who work in highly specialized areas. Each engineer will have very different job requirements and use unique tools and applications in their job. Which of the following is MOST appropriate
to use?
A. Role-based privileges
B. Credential management
C. User assigned privileges
D. User access
Correct Answer: A
QUESTION 76
Account lockout is a mitigation strategy used by Jane, the administrator, to combat which of the following attacks? (Select TWO).
A. Spoofing
B. Man-in-the-middle
C. Dictionary
D. Brute force
E. Privilege escalation
Correct Answer: CD
QUESTION 77
Which of the following is an authentication and accounting service that uses TCP for connecting to routers and switches?
A. DIAMETER
B. RADIUS
C. TACACS+
D. Kerberos
Correct Answer: C
QUESTION 78
A recent audit has discovered that at the time of password expiration clients are able to recycle the previous credentials for authentication. Which of the following controls should be used together to prevent this from occurring? (Select TWO).
A. Password age
B. Password hashing
C. Password complexity
D. Password history
E. Password length
Correct Answer: AD
QUESTION 79
An auditing team has found that passwords do not meet best business practices. Which of the following will MOST increase the security of the passwords? (Select TWO).
A. Password Complexity
B. Password Expiration
C. Password Age
D. Password Length
E. Password History
Correct Answer: AD
QUESTION 80
Which of the following protocols provides for mutual authentication of the client and server?
A. Two-factor authentication
B. Radius
C. Secure LDAP
D. Biometrics
Correct Answer: C
QUESTION 81
Ann, the security administrator, wishes to implement multifactor security. Which of the following should be implemented in order to compliment password usage and smart cards?
A. Hard tokens
B. Fingerprint readers
C. Swipe badge readers
D. Passphrases
Correct Answer: B
QUESTION 82
Which of the following services are used to support authentication services for several local devices from a central location without the use of tokens?
A. TACACS+
B. Smartcards
C. Biometrics
D. Kerberos
Correct Answer: A
QUESTION 83
After Ann, a user, logs into her banking websites she has access to her financial institution mortgage, credit card, and brokerage websites as well. Which of the following is being described?
A. Trusted OS
B. Mandatory access control
C. Separation of duties
D. Single sign-on
Correct Answer: D
QUESTION 84
Which of the following is an authentication method that can be secured by using SSL?
A. RADIUS
B. LDAP
C. TACACS+
D. Kerberos
Correct Answer: B
QUESTION 85
A small company has a website that provides online customer support. The company requires an account recovery process so that customers who forget their passwords can regain access.
Which of the following is the BEST approach to implement this process?
A. Replace passwords with hardware tokens which provide two-factor authentication to the online customer support site.
B. Require the customer to physically come into the company’s main office so that the customer can be authenticated prior to their password being reset.
C. Web-based form that identifies customer by another mechanism and then emails the customer their forgotten password.
D. Web-based form that identifies customer by another mechanism, sets a temporary password and forces a password change upon first login.
Correct Answer: D
QUESTION 86
Which of the following common access control models is commonly used on systems to ensure a “need to know” based on classification levels?
A. Role Based Access Controls
B. Mandatory Access Controls
C. Discretionary Access Controls
D. Access Control List
Correct Answer: B
QUESTION 87
A customer has provided an email address and password to a website as part of the login process. Which of the following BEST describes the email address?
A. Identification
B. Authorization
C. Access control
D. Authentication
Correct Answer: A
QUESTION 88
Speaking a passphrase into a voice print analyzer is an example of which of the following security concepts?
A. Two factor authentication
B. Identification and authorization
C. Single sign-on
D. Single factor authentication
Correct Answer: A
QUESTION 89
A Chief Information Security Officer (CISO) wants to implement two-factor authentication within the company. Which of the following would fulfill the CISO’s requirements?
A. Username and password
B. Retina scan and fingerprint scan
C. USB token and PIN
D. Proximity badge and token
Correct Answer: C
QUESTION 90
A security administrator is concerned about the strength of user’s passwords. The company does not want to implement a password complexity policy. Which of the following can the security Administrator implement to mitigate the risk of an
online password attack against users with weak passwords?
A. Increase the password length requirements
B. Increase the password history
C. Shorten the password expiration period
D. Decrease the account lockout time
Correct Answer: C
QUESTION 91
Which of the following protocols is MOST likely to be leveraged by users who need additional information about another user?
A. LDAP
B. RADIUS
C. Kerberos
D. TACACS+
Correct Answer: A
QUESTION 92
A security administrator is reviewing the below output from a password auditing tool:
P@ss.
@pW1.
S3cU4
Which of the following additional policies should be implemented based on the tool’s output?
A. Password age
B. Password history
C. Password length
D. Password complexity
Correct Answer: C
QUESTION 93
In order for Sara, a client, to logon to her desktop computer, she must provide her username, password, and a four digit PIN. Which of the following authentication methods is Sara using?
A. Three factor
B. Single factor
C. Two factor
D. Four factor
Correct Answer: B
QUESTION 94
A new intern was assigned to the system engineering department, which consists of the system architect and system software developer’s teams. These two teams have separate privileges. The intern requires privileges to view the system
architectural drawings and comment on some software development projects. Which of the following methods should the system administrator implement?A. Group based privileges
B. Generic account prohibition
C. User access review
D. Credential management
Correct Answer: A
QUESTION 95
Joe Has read and write access to his own home directory. Joe and Ann are collaborating on a project, and Joe would like to give Ann write access to one particular file in this home directory. Which of the following types of access control
would this reflect?
A. Role-based access control
B. Rule-based access control
C. Mandatory access control
D. Discretionary access control
Correct Answer: D
QUESTION 96
A security administrator must implement a system that will support and enforce the following file system access control model:
FILE NAMESECURITY LABEL
Employees.docConfidential
Salary.xlsConfidential
OfficePhones.xlsUnclassified
PersonalPhones.xlsRestricted
Which of the following should the security administrator implement?
A. White and black listing
B. SCADA system
C. Trusted OS
D. Version control
Correct Answer: C
QUESTION 97
In Kerberos, the Ticket Granting Ticket (TGT) is used for which of the following?
A. Identification
B. Authorization
C. Authentication
D. Multifactor authentication
Correct Answer: C
QUESTION 98
Employee badges are encoded with a private encryption key and specific personal information.
The encoding is then used to provide access to the network. Which of the following describes this access control type?
A. Smartcard
B. Token
C. Discretionary access control
D. Mandatory access control
Correct Answer: A
QUESTION 99
Which of the following relies on the use of shared secrets to protect communication?
A. RADIUS
B. Kerberos
C. PKI
D. LDAP
Correct Answer: A
QUESTION 100
A system administrator is configuring UNIX accounts to authenticate against an external server. The configuration file asks for the following information DC=ServerName and DC=COM. Which of the following authentication services is being
used?
A. RADIUS
B. SAML
C. TACACS+
D. LDAP
Correct Answer: D
QUESTION 101
Which of the following is a measure of biometrics performance which rates the ability of a system to correctly authenticate an authorized user?
A. Failure to capture
B. Type II
C. Mean time to register
D. Template capacity
Correct Answer: B
QUESTION 102
During an audit, the security administrator discovers that there are several users that are no longer employed with the company but still have active user accounts. Which of the following should be performed?
A. Account recovery
B. Account disablement
C. Account lockouts
D. Account expiration
Correct Answer: B
QUESTION 103
ABC company has a lot of contractors working for them. The provisioning team does not always get notified that a contractor has left the company. Which of the following policies would prevent contractors from having access to systems in
the event a contractor has left?
A. Annual account review
B. Account expiration policy
C. Account lockout policy
D. Account disablement
Correct Answer: B
QUESTION 104
A company wants to ensure that all credentials for various systems are saved within a central database so that users only have to login once for access to all systems. Which of the following would accomplish this?
A. Multi-factor authentication
B. Smart card access
C. Same Sign-On
D. Single Sign-On
Correct Answer: D
QUESTION 105
Which of the following techniques enables a highly secured organization to assess security weaknesses in real time?
A. Access control lists
B. Continuous monitoring
C. Video surveillance
D. Baseline reporting
Correct Answer: B
QUESTION 106
A network administrator, Joe, arrives at his new job to find that none of the users have changed their network passwords since they were initially hired. Joe wants to have everyone change their passwords immediately. Which of the following
policies should be enforced to initiate a password change?
A. Password expiration
B. Password reuse
C. Password recovery
D. Password disablement
Correct Answer: A
QUESTION 107
Joe, a network administrator, is able to manage the backup software console by using his network login credentials. Which of the following authentication services is the MOST likely using?
A. SAML
B. LDAP
C. iSCSI
D. Two-factor authentication
Correct Answer: B
QUESTION 108
Pete, a security auditor, has detected clear text passwords between the RADIUS server and the authenticator. Which of the following is configured in the RADIUS server and what technologies should the authentication protocol be changed
to?
A. PAP, MSCHAPv2
B. CHAP, PAP
C. MSCHAPv2, NTLMv2
D. NTLM, NTLMv2
Correct Answer: A
QUESTION 109
A technician wants to implement a dual factor authentication system that will enable the organization to authorize access to sensitive systems on a need-to-know basis. Which of the following should be implemented during the authorization
stage?
A. Biometrics
B. Mandatory access control
C. Single sign-on
D. Role-based access control
Correct Answer: A
QUESTION 110
Which of the following practices reduces the management burden of access management?
A. Password complexity policies
B. User account audit
C. Log analysis and review
D. Group based privileges
Correct Answer: D
QUESTION 111
An organization’s security policy states that users must authenticate using something you do. Which of the following would meet the objectives of the security policy?
A. Fingerprint analysis
B. Signature analysis
C. Swipe a badge
D. Password
Correct Answer: B
QUESTION 112
The company’s sales team plans to work late to provide the Chief Executive Officer (CEO) with a special report of sales before the quarter ends. After working for several hours, the team finds they cannot save or print the reports.
Which of the following controls is preventing them from completing their work?
A. Discretionary access control
B. Role-based access control
C. Time of Day access control
D. Mandatory access control
Correct Answer: C
QUESTION 113
A network administrator uses an RFID card to enter the datacenter, a key to open the server rack, and a username and password to logon to a server. These are examples of which of the following?
A. Multifactor authentication
B. Single factor authentication
C. Separation of duties
D. Identification
Correct Answer: B
QUESTION 114
A system administrator has noticed that users change their password many times to cycle back to the original password when their passwords expire. Which of the following would BEST prevent this behavior?
A. Assign users passwords based upon job role.
B. Enforce a minimum password age policy.
C. Prevent users from choosing their own passwords.
D. Increase the password expiration time frame.
Correct Answer: B
QUESTION 115
Which of the following BEST describes using a smart card and typing in a PIN to gain access to a system?
A. Biometrics
B. PKI
C. Single factor authentication
D. Multifactor authentication
Correct Answer: D
QUESTION 116
During the information gathering stage of a deploying role-based access control model, which of the following information is MOST likely required?
A. Conditional rules under which certain systems may be accessed
B. Matrix of job titles with required access privileges
C. Clearance levels of all company personnel
D. Normal hours of business operation
Correct Answer: B
QUESTION 117
Which of the following passwords is the LEAST complex?
A. MyTrain!45
B. Mytr@in!!
C. MyTr@in12
D. MyTr@in#8
Correct Answer: B
QUESTION 118
Which of the following should be done before resetting a user’s password due to expiration?
A. Verify the user’s domain membership.
B. Verify the user’s identity.
C. Advise the user of new policies.
D. Verify the proper group membership.
Correct Answer: B
QUESTION 119
Which of the following is an authentication service that uses UDP as a transport medium?
A. TACACS+
B. LDAP
C. Kerberos
D. RADIUS
Correct Answer: D
QUESTION 120
Ann works at a small company and she is concerned that there is no oversight in the finance department; specifically, that Joe writes, signs and distributes paycheques, as well as other expenditures. Which of the following controls can she
implement to address this concern?
A. Mandatory vacations
B. Time of day restrictions
C. Least privilege
D. Separation of duties
Correct Answer: D
QUESTION 121
A recent review of accounts on various systems has found that after employees’ passwords are required to change they are recycling the same password as before. Which of the following policies should be enforced to prevent this from
happening? (Select TWO).
A. Reverse encryption
B. Minimum password age
C. Password complexity
D. Account lockouts
E. Password history
F. Password expiration
Correct Answer: BE
QUESTION 122
Which of the following types of authentication solutions use tickets to provide access to various resources from a central location?
A. Biometrics
B. PKI
C. ACLs
D. Kerberos
Correct Answer: D
QUESTION 123
Use of a smart card to authenticate remote servers remains MOST susceptible to which of the following attacks?
A. Malicious code on the local system
B. Shoulder surfing
C. Brute force certificate cracking
D. Distributed dictionary attacks
Correct Answer: A
QUESTION 124
The security administrator notices a user logging into a corporate Unix server remotely as root. Which of the following actions should the administrator take?
A. Create a firewall rule to block SSH
B. Delete the root account
C. Disable remote root logins
D. Ensure the root account has a strong password
Correct Answer: C
QUESTION 125
Which of the following types of authentication packages user credentials in a ticket?
A. Kerberos
B. LDAP
C. TACACS+
D. RADIUS
Correct Answer: A
QUESTION 126
An organization is implementing a password management application which requires that all local administrator passwords be stored and automatically managed. Auditors will be responsible for monitoring activities in the application by
reviewing the logs. Which of the following security controls is the BEST option to prevent auditors from accessing or modifying passwords in the application?
A. Time of day restrictions
B. Create user accounts for the auditors and assign read-only access
C. Mandatory access control
D. Role-based access with read-only
Correct Answer: D
QUESTION 127
A new network administrator is setting up a new file server for the company. Which of the following would be the BEST way to manage folder security?
A. Assign users manually and perform regular user access reviews
B. Allow read only access to all folders and require users to request permission
C. Assign data owners to each folder and allow them to add individual users to each folder
D. Create security groups for each folder and assign appropriate users to each group
Correct Answer: D
QUESTION 128
A user ID and password together provide which of the following?
A. Authorization
B. Auditing
C. Authentication
D. Identification
Correct Answer: C
QUESTION 129
A file on a Linux server has default permissions of rw-rw-r–. The system administrator has verified that Ann, a user, is not a member of the group owner of the file. Which of the following should be modified to assure that Ann has read access
to the file?
A. User ownership information for the file in question
B. Directory permissions on the parent directory of the file in question
C. Group memberships for the group owner of the file in question
D. The file system access control list (FACL) for the file in question
Correct Answer: C
QUESTION 130
An insurance company requires an account recovery process so that information created by an employee can be accessed after that employee is no longer with the firm. Which of the following is the BEST approach to implement this
process?
A. Employee is required to share their password with authorized staff prior to leaving the firm
B. Passwords are stored in a reversible form so that they can be recovered when needed
C. Authorized employees have the ability to reset passwords so that the data is accessible
D. All employee data is exported and imported by the employee prior to them leaving the firm
Correct Answer: C
QUESTION 131
A network inventory discovery application requires non-privileged access to all hosts on a network for inventory of installed applications. A service account is created by the network inventory discovery application for accessing all hosts.
Which of the following is the MOST efficient method for granting the account non-privileged access to the hosts?
A. Implement Group Policy to add the account to the users group on the hosts
B. Add the account to the Domain Administrator group
C. Add the account to the Users group on the hosts
D. Implement Group Policy to add the account to the Power Users group on the hosts.
Correct Answer: A
QUESTION 132
A supervisor in the human resources department has been given additional job duties in the accounting department. Part of their new duties will be to check the daily balance sheet calculations on spreadsheets that are restricted to the
accounting group. In which of the following ways should the account be handled?
A. The supervisor should be allowed to have access to the spreadsheet files, and their membership in the human resources group should be terminated.
B. The supervisor should be removed from the human resources group and added to the accounting group.
C. The supervisor should be added to the accounting group while maintaining their membership in the human resources group.
D. The supervisor should only maintain membership in the human resources group.
Correct Answer: C
QUESTION 133
An information bank has been established to store contacts, phone numbers and other records.
An application running on UNIX would like to connect to this index server using port 88. Which of the following authentication services would this use this port by default?
A. Kerberos
B. TACACS+
C. Radius
D. LDAP
Correct Answer: A
QUESTION 134
A user has forgotten their account password. Which of the following is the BEST recovery strategy?
A. Upgrade the authentication system to use biometrics instead.
B. Temporarily disable password complexity requirements.
C. Set a temporary password that expires upon first use.
D. Retrieve the user password from the credentials database.
Correct Answer: C
QUESTION 135
Ann has taken over as the new head of the IT department. One of her first assignments was to implement AAA in preparation for the company’s new telecommuting policy. When she takes inventory of the organizations existing network
infrastructure, she makes note that it is a mix of several different vendors. Ann knows she needs a method of secure centralized access to the company’s network resources. Which of the following is the BEST service for Ann to implement?
A. RADIUS
B. LDAP
C. SAML
D. TACACS+
Correct Answer: A
QUESTION 136
The fundamental information security principals include confidentiality, availability and which of the following?
A. The ability to secure data against unauthorized disclosure to external sources
B. The capacity of a system to resist unauthorized changes to stored information
C. The confidence with which a system can attest to the identity of a user
D. The characteristic of a system to provide uninterrupted service to authorized users
Correct Answer: B
QUESTION 137
The IT department has setup a share point site to be used on the intranet. Security has established the groups and permissions on the site. No one may modify the permissions and all requests for access are centrally managed by the
security team. This is an example of which of the following control types?
A. Rule based access control
B. Mandatory access control
C. User assigned privilege
D. Discretionary access control
Correct Answer: D
QUESTION 138
A company has 5 users. Users 1, 2 and 3 need access to payroll and users 3, 4 and 5 need access to sales. Which of the following should be implemented to give the appropriate access while enforcing least privilege?
A. Assign individual permissions to users 1 and 2 for payroll. Assign individual permissions to users 4 and 5 for sales. Make user 3 an administrator.
B. Make all users administrators and then restrict users 1 and 2 from sales. Then restrict users 4 and 5 from payroll.
C. Create two additional generic accounts, one for payroll and one for sales that users utilize.
D. Create a sales group with users 3, 4 and 5. Create a payroll group with users 1, 2 and 3.
Correct Answer: D
QUESTION 139
Which of the following is an important implementation consideration when deploying a wireless network that uses a shared password?
A. Authentication server
B. Server certificate
C. Key length
D. EAP method
Correct Answer: C
QUESTION 140
For each of the given items, select the appropriate authentication category from the dropdown choices.
Instructions: When you have completed the simulation, please select the Done button to submit.

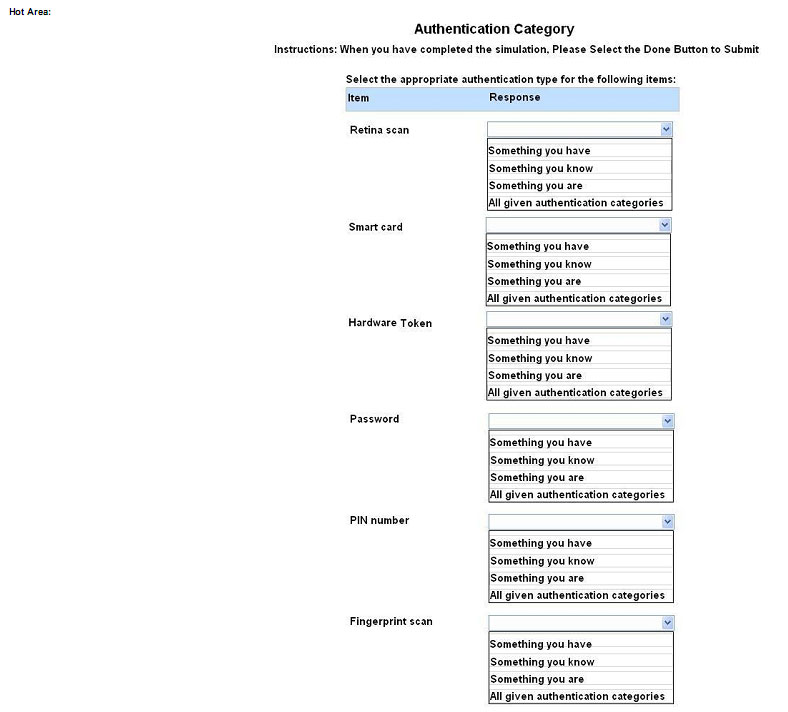
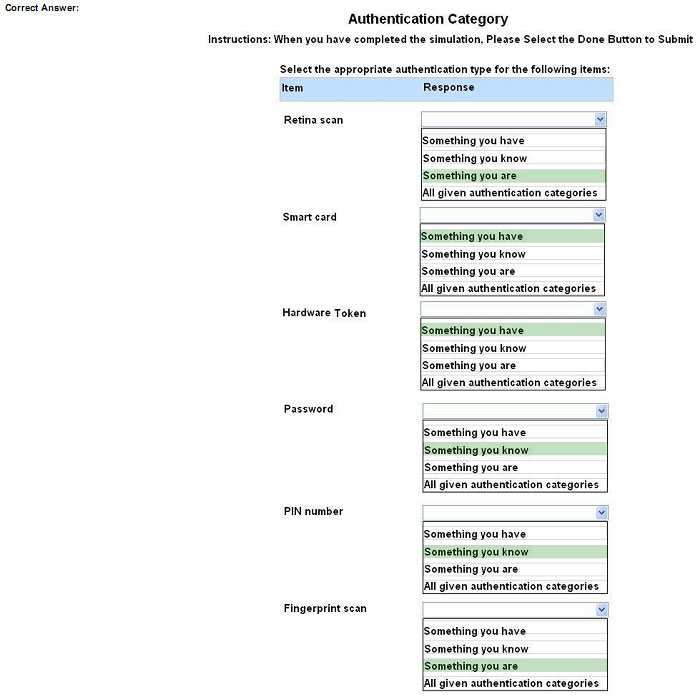
QUESTION 141
For each of the given items, select the appropriate authentication category from the drop down choices.
Select the appropriate authentication type for the following items:

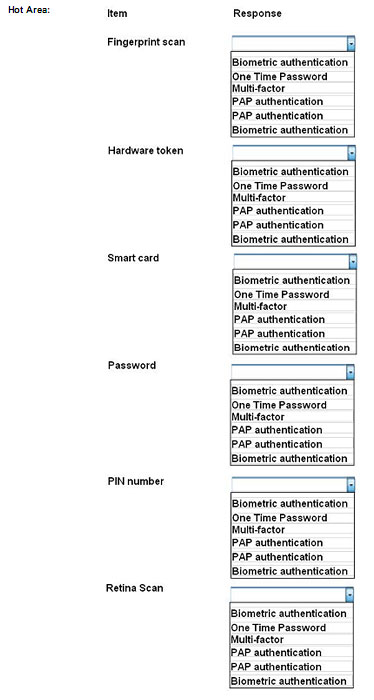
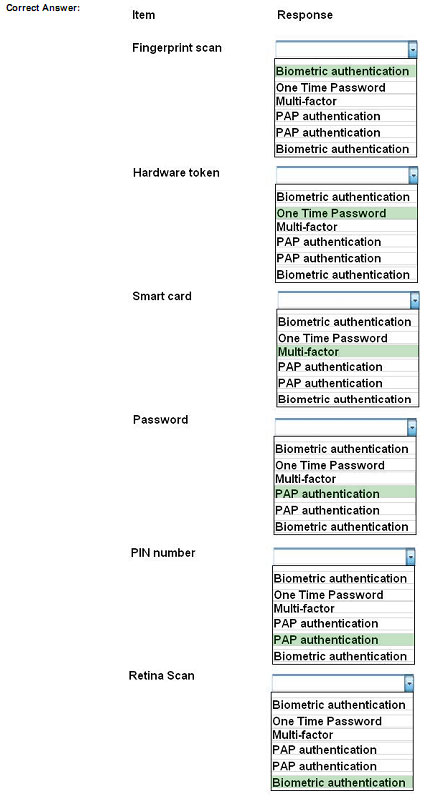
About the exam:
CompTIA Security+ is the first security certification IT professionals should earn. It establishes the core knowledge
required of any cybersecurity role and provides a springboard to intermediate-level cybersecurity jobs. Security+
incorporates best practices in hands-on trouble-shooting to ensure security professionals have practical security
problem-solving skills. Cybersecurity professionals with Security+ know how to address security incidents –
not just identify them.
The new CompTIA Security+ SY0-501 exam is available as of October 4, 2017. More information on both versions of the exam is
available in the Exam Details below.
Conclusion:
We shared 141 free CompTIA security+ sy0-401 exam dumps and sy0-401 PDF to help you get started with the first step
of certification, and to easily pass the exam requires a complete selection of https://www.pass4itsure.com/sy0-401.html PDF + VCE
(100% guaranteed actual validity, 100% latest, 100% guaranteed invalid refund)
[PDF] Free CompTIA Security+ SY0-401 dumps download from Google Drive:
https://drive.google.com/open?id=1fNUvuARTsqEpjU2G_fxVaZCoDDWhG1sd
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
Pass4itsure Promo Code 15% Off
related: https://www.certificationmonitor.com/the-best-cisco-300-360-dumps-practice-test/
About US

Why Certificationmonitor was built?
At present, there are many free IT material providing platforms on the entire Internet, including blog sites, sales sites, forums, etc. In fact, it is unrealistic to be completely free. Some publish more and some publish less. In fact, most of what they share is Expired content. No real meaning. It is very good to share the latest free materials to really let candidates know the latest exam situation, but some people promote it as completely free.
After actual calculation, it was found that the cost was more, and it was very shameful that they used different charging models to realize the cash.
The purpose of establishing the Certificationmonitor platform
Because of this, I created this IT exam material platform, which is a comprehensive platform that shares the most popular IT exam materials: Cisco, Microsoft, CompTIA, Fortinet, Amazon, ISC, HP, IBM, etc. Certificationmonitor has It has been established for a long time, but we have yet to share the original intention of our founding. Today we solemnly publish “About Us” to tell all candidates what the platform is doing.
What will Certificationmonitor do for you?
Certificationmonitor is a self-managed blog platform that prohibits entry of any irrelevant content, so comments are blocked and registered users are prohibited.
I would like to ask everyone, what is your purpose in choosing an IT material supplier? There is no doubt that you must successfully pass the target exam through one exam practice. This is the real savings.
Some sales websites are free on the surface, but actually charge higher prices. Most of the content is expired, and the content is not updated in a timely manner. The money spent in the last few times may not be able to pass.
On this platform, the latest IT exam materials will be shared from time to time. None are completely free, only part of them can be shared, and we will recommend you truly useful material channels, because the truly effective exam materials are all private.
My materials came from Pass4itsure, and their team provided me with some practical exam questions and answers. I will organize and edit, collect key information for the actual exam and publish it online.