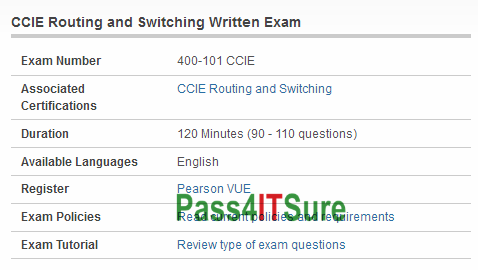
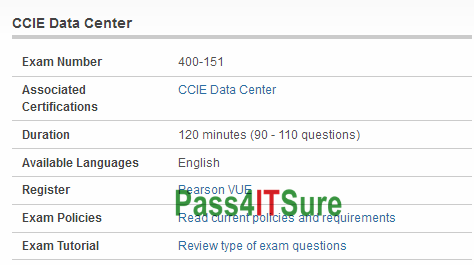
Cisco exam 400-151 dumps which study guides are better? The CCIE Data Center Written Exam (400-151 CCIE Data Center) exam is a 120 minutes (90 – 110 questions) assessment in pass4itsure that is associated with the CCIE Data Center certification. Easily to pass 2018 latest Cisco 400-151 dumps pdf CCIE Data Center test questions and answers with high quality Youtube study. “CCIE Data Center Written Exam” is the exam name of Pass4itsure Cisco 400-151 dumps test which designed to help candidates prepare for and pass the Cisco 400-151 exam. If you buy Pass4itsure’s Cisco certification 400-151 valid test questions and answers exam practice questions and answers, you can not only pass Cisco certification https://www.pass4itsure.com/400-151.html dumps valid test questions and answers exam, but also enjoy a year of free update service.
[100% Valid Cisco 400-151 Dumps Questions From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWbTFibUcwbXBkZms
[100% Valid Cisco 400-201 Dumps Questions From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWV2ZxQlJ2OGxkaXc
Pass4itsure Free Cisco 400-151 Dumps Exam Questions and Answers:
2.Which IPv4 address classes are reserved for specific uses and may not be assigned to hosts? (Choose two.)
A.A
B.B
C.C
D.D
E.E
400-151 exam Correct:D E
3.What IPX routing protocol is best suited for an internetwork that contains 138 routers, multiple redundant routes that require load balancing, and three WAN links? Answer:
A.NLSP,(NETWARELINKSERVICESPROTOCOL)
Correct:A
4.Which two components of the TCP/IP protocol suite map to the Host-to-Host layer of the DOD model? (Choose two.)
A.IP B.TCP
C.FTP
D.NFS
E.UDP
F.ARP
400-151 dumps Correct:B E
5.Click on the Exhibit button. A Class B network uses the subnet mask 255.255.224.0. The network will reserve subnets of all “0’s” and all “1’s”. What is the maximum number of available subnets?
Answer:
A.6
Correct:A
6.Select the link state routing protocols. (Choose two.)
A.RIP B.LAT
C.SNA
D.NLSP
E.RTMP
F.OSPF
400-151 pdf Correct:D F
7.What protocol is normally considered to be both a LAN and WAN protocol?
A.PPP
B.ATM
C.X.25
D.SLIP E.ISDN
F.Frame Relay
Correct:B
8.Identify the network devices associated with the Data Link layer of the OSI model. (Choose two.)
A.NICs
B.routers
C.switches
D.gateways
E.repeaters
F.active hubs
400-151 vce Correct:A C
9.What is the maximum number of bytes that can be dedicated to the station address portion of an IPv4 address? Answer:
A.THREE
Correct:A
10.What IPX routing protocol generally uses the least bandwidth, provides the fastest routing updates, and offers scalability for large internetworks? Answer:
A.NLSP,(NETWARELINKSERVICESPROTOCOL)
400-151 exam Correct:A
11.What are two disadvantages to RIP? (Choose two.)
A.static routing B.count
to-infinity C.resource
intensive D.slow
convergence time E.lack
of industry support
Correct:B D
12.A network uses a subnet mask of 255.255.248.0. It reserves host addresses containing all “1’s”. How many host addresses are available for each subnet?
A.255
B.512
C.1023
D.2047
400-151 dumps Correct:D
13.What protocol provides access to the X.500 and is specifically targeted at simple management
and browser applications? Answer:
A.LDAP,(LIGHTWEIGHTDIRECTORYACCESSPROTOCOL)
Correct:A
14.How many characters may be in a single domain name label?
A.16
B.63
C.120
D.255
400-151 pdf Correct:B
15.Which IPX network addresses are reserved for special purposes? (Choose three.)
A.00000000
B.11111111
C.FFFFFFFF
D.FFFFFFFE
E.AAAAAAAA
F.AAAA0000
Correct:A C D
16.How many bits are in an IPv4 address? Answer:
A.32
400-151 vce Correct:A
17.What IPX routing protocol offers load balancing capabilities without reducing the physical size of the internetwork? Answer:
A.NLSP,(NETWARELINKSERVICESPROTOCOL)
Correct:A
18.What information is exchanged in an initial “hello” packet between OSPF routers? (Choose three.)
A.hello interval
B.router priority number
C.full link state database
D.IP address and subnet mask
E.summary of the link state database
F.summary of the link state advertising database
400-151 exam Correct:A B D
19.A network administrator has been assigned a Class B network address of 150.225.0.0. The administrator then subnetted the network with a subnet mask of 255.255.240.0. If the administrator is reserving node addresses of all “0’s” and all “1’s,” what is the range of available node addresses for the subnet 150.225.32.0?
A.150.225.32.1 to 150.225.44.254
B.150.225.32.1 to 150.225.47.254
C.150.225.32.1 to 150.225.48.254
D.150.225.32.1 to 150.225.50.254
E.150.225.32.1 to 150.225.52.254
F.150.225.33.1 to 150.225.44.254
G.150.225.33.1 to 150.225.46.254
H.150.225.33.1 to 150.225.48.254
I.150.225.33.1 to 150.225.52.254
J.150.225.33.1 to 150.225.54.254
Correct:A
20.How many IP addresses must be combined to create the IP supernet address 215.100.16.0/21?
A.2
B.3
C.4
D.5
E.6
F.7
G.8
H.9
I.10
400-151 dumps Correct:G
21. An example of a module exhibiting temporal cohesion is a combination of .
A. the control and management of two onboard hardware clocks
B. a 40 millisecond periodic navigation function and a 40 millisecond periodic display update function
C. several mathematical functions such as the sine, cosine, and arctangent functions
D. the vehicle speed and acceleration management functions
Answer: B
22. What two actions must occur in systems that use overlaying with a disk drive backing store? (Choose two.)
A. Only data is stored on the disk and code is stored in RAM.
B. A task executing in RAM can also execute code that is stored on the disk.
C. The operating system must prevent each task in RAM from accessing RAM outside the area reserved for it.
D. The code for the currently executing tasks is stored in RAM and that for the currently inactive tasks is stored on the disk, as managed by the operating system.
400-151 pdf Answer: CD
23. Which two statements about static memory allocation are true? (Choose two.)
A. Garbage collection is not required.
B. Memory fragmentation does not occur.
C. Memory allocation units are always the same fixed size.
D. Tasks must inform the run-time (e.g., operating system) the total amount of memory they will need before they begin requesting memory.
Answer: AB
24. POSIX .
A. is the same as UNIX
B. is not designed for real-time systems
C. does not support asynchronous I/O
D. is an operating system interface standard
400-151 vce Answer: D
25. A scheduler runs tasks to completion instead of pre-empting tasks by time slicing or according to priority. What two actions will occur? (Choose two.)
A. Maximize the number of completed tasks per unit of time
B. Minimize the task scheduling and context switching overheads
C. Honor the commitment made to complete the task once it has begun executing
D. Share the processor time fairly among ready tasks
Answer: BC
26. Which two statements are true of a monitor for synchronization? (Choose two.)
A. No concurrent access by tasks is allowed to any resource(s) within a monitor.
B. One monitor may encapsulate any number of resources and their synchronization functions.
C. If a requesting task enters a monitor but finds the resource isn’t available, the task exits the monitor and is placed at the end of the monitor’s external queue.
D. If two tasks are waiting in a monitor’s queues for separate resources, when the task that has been accessing a resource finishes doing so, all the queues with waiting tasks are served round-robin.
400-151 exam Answer: AB
27. Which two are POSIX real-time extensions? (Choose two.)
A. suspend / resume API’s
B. direct cyclic executive support
C. task synchronization
D. priority-based preemptive task scheduling
Answer: CD
28. Which two of these techniques would successfully avoid mutual exclusion deadlocks? (Choose two.)
A. Set up a circular dependency of tasks and resources
B. Allow a task’s use of a resource to be pre-empted
C. Require tasks to acquire and use only one resource at a time
D. Require tasks to acquire resources in order of the tasks’ priorities
400-151 dumps Answer: BC
29. The priority of a runnable task blocked on a resource request is temporarily changed to be the same as the priority of another task. Which two phrases could describe the new priority? (Choose two.)
A. The priority of the highest priority task
B. The priority of the lowest priority task which uses the resource
C. The priority of the higher priority task being blocked by the lower priority one
D. The ceiling priority of the resource on which the lower priority task is blocked
Answer: CD
30. What two results occur by changing priorities dynamically? (Choose two.)
A. Reduces overhead
B. Increases overhead
C. May starve lower priority tasks
D. Avoids the need for priority queues
400-151 pdf Answer: BC
31. A representative benchmark differs from a synthetic benchmark in that a .
A. representative benchmark models a representative ideal application
B. synthetic benchmark precisely predicts specific application performance
C. representative benchmark models a real application’s execution characteristics
D. synthetic benchmark must be developed by the same team that will build the application
Answer: C
32. Network protocol models are described as layers that .
A. permit separation of concerns of lower layers (e.g., hardware) from higher layers (e.g., application)
B. add increasing efficiency to higher layers (e.g., application) than lower layers (e.g., hardware)
C. are highly consistent in number and function among different protocols
D. provide efficient application access to network hardware addresses
400-151 vce Answer: A
33. The primary requirement for an RTOS is to .
A. maximize application speed and minimize memory utilization
B. enable fast control and data transfer to critical system devices
C. enable the application to meet both its functional and temporal requrements
D. permit the application to efficiently access all resources (e.g., I/O and memory)
Answer: C
34. A strictly conforming POSIX application .
A. uses all POSIX functions and standard options
B. uses only IEEE tested conforming operating systems
C. uses only POSIX required API’s for its OS functionality
D. runs on all operating systems whose vendors claim POSIX conformance
400-151 exam Answer: C
35. Which statement accurately describes where a “mark” exists in the MDA model hierarchy?
A. as part of the PSM
B. as part of the PIM
C. as part of a transparent layer placed over a PIM
D. as part of a transparent layer placed over a PSM
Answer: C
36. In MDA practice, transformations from PIM to PSM . (Choose TWO.)
A. may be automated
B. are required for all systems
C. may be hand generated
D. always produce executable code
E. are always implemented in the QVT action language
400-151 dumps Answer: AC
37. What does the term “Platform independence” mean?
A. The application model can be moved to every other platform that is available.
B. The application model is independent of the features of any particular platform from some class of platforms.
C. The application is written in a high-level programming language such as Java or C++.
D. The application model is independent of the hardware platform where the application may be deployed.
Answer: B
38. What is an “implementation model”?
A. A PIM that provides all of the information needed to construct a system and put it into operation.
B. A model that includes C++ source code for all classes in the model.
C. A PSM that provides all of the information needed to construct a system and put it into operation.
D. A file that is executable on some computer system.
400-151 pdf Answer: C
39. What two functions does the Model transformation specification provide? (Choose TWO.)
A. Always prescribes a one-to-one mapping from input model elements to output model elements.
B. Prescribes the transformations that merge a set of models to produce another set of models.
C. Are implemented using the OMG standard Model Transformation language.
D. Prescribes the transformation of one model to another model.
Answer: BD
40. A metamodel is a .
A. set of UML templates for drawing system models
B. special kind of model that specifies a modeling language
C. collection of stereotypes and classes that define a set of architectural patterns
D. conceptual pattern for a class of application systems
400-151 vce Answer: B
You can free download part of practice questions and answers about Cisco certification 400-151 dumps valid test questions and answers exam as a try to test the reliability of Pass4itsure’s products.”CCIE Data Center Written Exam”, also known as 400-151 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Pass4itsure Cisco 400-151 dumps exam questions answers are updated (408 Q&As) are verified by experts. The associated certifications of 400-151 dumps is CCIE Data Center. If you fail your https://www.pass4itsure.com/400-151.html dumps exam, Pass4itsure will full refund to you.