Get the Oracle PL/SQL Developer Certified Associate 1z0-071 Certification Exam.
“Oracle Database 12c SQL”: https://www.pass4itsure.com/1z0-071.html (Q&As: 272).
Free Oracle PL/SQL Developer Certified Associate 1z0-071 exam practice test. Improve your skills and exam experience!
Get the latest Oracle PL/SQL Developer Certified Associate 1z0-071 pdf
[PDF] Free Oracle 1z0-071 pdf dumps download from Google Drive: https://drive.google.com/open?id=1JxGiD_ejPIkZwon2FXtX9nLtXRK-gJvQ
Valid information provided by Oracle officials
Oracle Database SQL Certification Exam | 1Z0-071: https://education.oracle.com/oracle-database-sql/pexam_1Z0-071
Associated Certification Paths
- Oracle Database 11g Administrator Certified Associate
- Oracle PL/SQL Developer Certified Associate
- Oracle Database 12c Administrator Certified Associate
- Oracle Database SQL Certified Associate
The latest Oracle PL/SQL Developer Certified Associate 1z0-071 exam practice questions test your strength
QUESTION 1
Which are iSQL*Plus commands? (Choose all that apply.)
A. INSERT
B. UPDATE
C. SELECT
D. DESCRIBE
E. DELETE
F. RENAME
Correct Answer: D
The only SQL*Plus command in this list : DESCRIBE. It cannot be used as SQL command. This command returns a
description of tablename, including all columns in that table, the datatype for each column and an indication of whether
the column permits storage of NULL values.
Incorrect answer:
A. INSERT is not a SQL*PLUS command
B. UPDATE is not a SQL*PLUS command
C. SELECT is not a SQL*PLUS command
E. DELETE is not a SQL*PLUS command
F. RENAME is not a SQL*PLUS command
Refer: Introduction to Oracle9i: SQL, Oracle University Study Guide, 7
QUESTION 2
Which two statements are true regarding working with dates? (Choose two.)
A. The RR date format automatically calculates the century from the SYSDATE function but allows the session user to
enter the century.
B. The RR date format automatically calculates the century from the SYSDATE function and does not allow a session
user to enter the century.
C. The default internal storage of dates is in character format.
D. The default internal storage of dates is in numeric format.
Correct Answer: AD
QUESTION 3
Examine the description of the EMP_DETAILS table given below:
Which two statements are true regarding SQL statements that can be executed on the EMP_DETAIL TABLE?
A. An EMP_IMAGE column cannot be included in the ORDER BY clause.
B. You can alter the table to include the NOT NULL constraint on the EMP_IMAGE column.
C. You cannot add a new column to the table with LONG as the data type.
D. An EMP_IMAGE column can be included in the GROUP BY clause.
Correct Answer: AC
QUESTION 4
View the Exhibit and examine the structure of the CUSTOMERS table.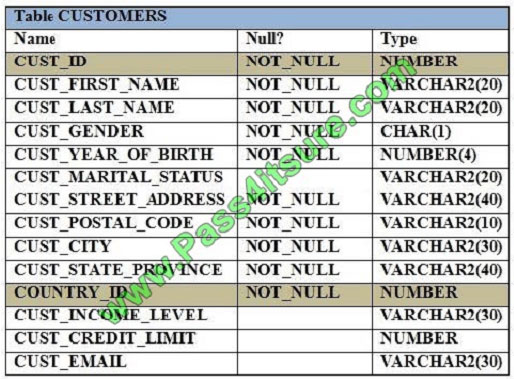
Evaluate the following SQL statement: Which statement is true regarding the outcome of the above query?
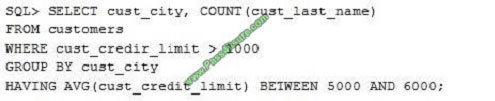
A. It returns an error because the BETWEEN operator cannot be used in the HAVING clause.
B. It returns an error because WHERE and HAVING clauses cannot be used in the same SELECT statement.
C. It returns an error because WHERE and HAVING clauses cannot be used to apply conditions on the same column.
D. It executes successfully.
Correct Answer: D
QUESTION 5
Examine the commands used to create DEPARTMENT_DETAILS and COURSE_DETAILS tables: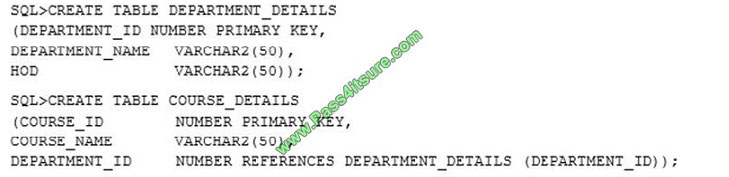
You want to generate a list of all department IDs that do not exist in the COURSE_DETAILS table.
You execute the SQL statement:

What is the outcome?
A. It fails because the join type used is incorrect.
B. It executes successfully and displays the required list.
C. It executes successfully but displays an incorrect list.
D. It fails because the ON clause condition is not valid.
Correct Answer: B
QUESTION 6
Which two statements are true about sequences crated in a single instance Oracle database?
A. The numbers generated by an explicitly defined sequence can only be used to insert data in one table.
B. DELETE would remove a sequence from the database.
C. CURRVAL is used to refer to the most recent sequence number that has been generated for a particular sequence.
D. When the MAXVALUE limit for a sequence is reached, it can be increased by using the ALTER SEQUENCE
statement.
E. When the database instance shuts down abnormally, sequence numbers that have been cached but not used are
available again when the instance is restarted.
Correct Answer: CD
QUESTION 7
Which two statements are true regarding single row functions? (Choose two.)
A. MOD : returns the quotient of a division.
B. TRUNC : can be used with NUMBER and DATE values.
C. CONCAT : can be used to combine any number of values.
D. SYSDATE : returns the database server current date and time.
E. INSTR : can be used to find only the first occurrence of a character in a string.
F. TRIM : can be used to remove all the occurrences of a character from a string.
Correct Answer: BD
QUESTION 8
Which three SQL statements would display the value 1890.55 as $1,890.55? (Choose three.)
A. SELECT TO_CHAR (1890.55, \\’$99G999D00\\’) FROM DUAL
B. SELECT TO_CHAR (1890.55, \\’$9,999V99\\’) FROM DUAL;
C. SELECT TO_CHAR (1890.55, \\’$0G000D00\\’) FROM DUAL;
D. SELECT TO_CHAR (1890.55, \\’$99,999D99\\’) FROM DUAL;
E. SELECT TO_CHAR (1890.55, \\’$99G999D99\\’) FROM DUAL
Correct Answer: ACE
QUESTION 9
View the exhibit and examine the description of the EMPLOYEES table. (Choose two.)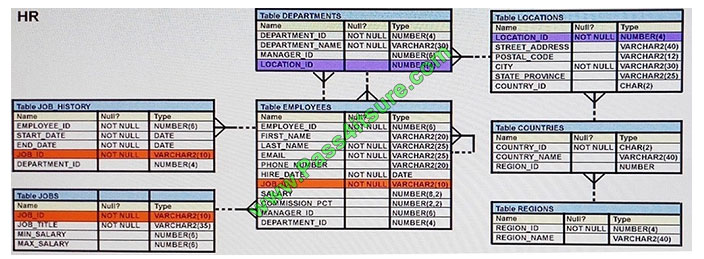
You executed this SQL statement:
SELECT first_name, department_id, salary FROM employees ORDER BY department_id, first_name, salary desc;
Which two statements are true regarding the result? (Choose two.)
A. The values in the SALARY column would be returned in descending order for all employees having the same value in
the DEPARTMENT_ID and FIRST_NAME column.
B. The values in the FIRST_NAME column would be returned in ascending order for all employees having the same
value in the DEPARTMENT_ID column.
C. The values in the SALARY column would be returned in descending order for all employees having the same value in
the DEPARTMENT_ID column.
D. The values in all columns would be returned in descending order.
E. The values in the FIRST_NAME column would be returned in descending order for all employees having the same
value in the DEPARTMENT_ID column.
Correct Answer: AB
QUESTION 10
View the Exhibits and examine PRODUCTS and SALES tables.
Exhibit 1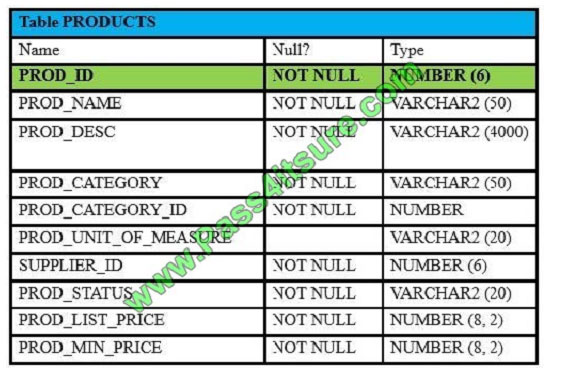
Exhibit 2
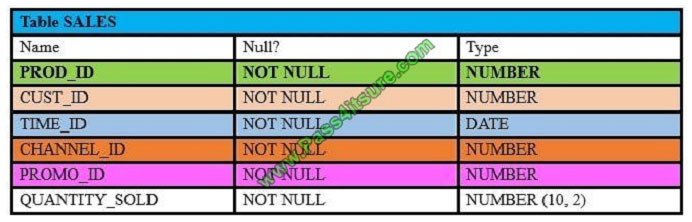
You issue the following query to display product name the number of times the product has been sold:
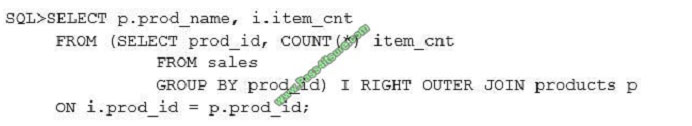
What happens when the above statement is executed?
A. The statement executes successfully and produces the required output.
B. The statement produces an error because a subquery in the FROM clause and outer-joins cannot be used together.
C. The statement produces an error because the GROUP BY clause cannot be used in a subquery in the FROM
clause.
D. The statement produces an error because ITEM_CNT cannot be displayed in the outer query.
Correct Answer: A
QUESTION 11
View the Exhibit and examine the structure of the EMP table which is not partitioned and not an index-organized table.
(Choose two.)
Evaluate this SQL statement:
ALTER TABLE emp
DROP COLUMN first_name;
Which two statements are true?
A. The FIRST_NAME column can be dropped even if it is part of a composite PRIMARY KEY provided the CASCADE
option is added to the SQL statement.
B. The FIRST_NAME column would be dropped provided at least one column remains in the table.
C. The FIRST_NAME column would be dropped provided it does not contain any data.
D. The drop of the FIRST_NAME column can be rolled back provided the SET UNUSED option is added to the SQL
statement.
Correct Answer: B
QUESTION 12
View the Exhibit and examine the structure of the ORDERS table.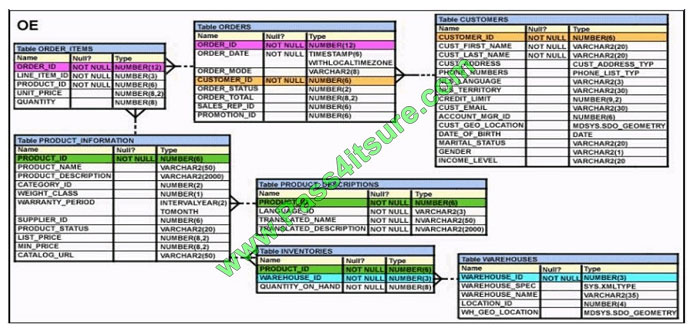
Which UPDATE statement is valid?
A. UPDATE orders SET order_date = \\’12-mar-2007\\’, order_total IS NULL WHERE order_id = 2455;
B. UPDATE orders SET order_date = \\’12-mar-2007\\’, AND order_total = TO_NUMBER(NULL) WHERE order_id =
2455;
C. UPDATE orders SET order_date = \\’12-mar-2007\\’, order_total = NULL WHERE order_id = 2455;
D. UPDATE orders SET order_date = TO_DATE(\\’12-mar-2007\\’,\\’dd-mon-yyyy\\’), SET order_total = TO_NUMBER
(NULL) WHERE order_id = 2455;
Correct Answer: C
QUESTION 13
View the Exhibit and examine the structure of the PROMOTIONS table.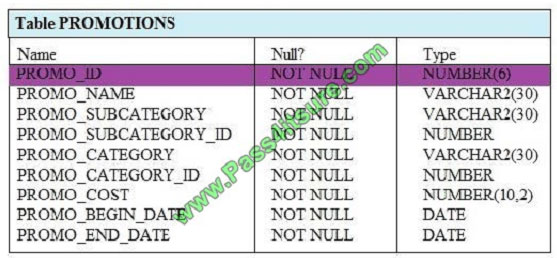
Evaluate the following SQL statement:

Which statement is true regarding the outcome of the above query?
A. It produces an error because subqueries cannot be used with the CASE expression.
B. It shows COST_REMARK for all the promos in the promo category `TV\\’.
C. It shows COST_REMARK for all the promos in the table.
D. It produces an error because the subquery gives an error.
Correct Answer: C
Follow Pass4itsure free sharing of YouTube channels
We offer more ways to make it easier for everyone to learn, and YouTube is the best tool in the video. Follow channels: https://www.youtube.com/channel/UCTP5RClZrtMxtRkSvIag0DQ/videos get more useful exam content.
Watch the Oracle PL/SQL Developer Certified Associate 1z0-071 video tutorial online
Share Pass4itsure coupons for free
Reasons to choose Pass4itsure
Pass4itsure offers the latest exam practice questions and answers free of charge! Update all exam questions throughout the year, with a number of professional exam experts! To make sure it works! Maximum pass rate, best value for money! Helps you pass the exam easily on your first attempt.
This maybe you’re interested
Summarize:
The latest Oracle PL/SQL Developer Certified Associate 1z0-071 dumps, online 1z0-071 practice test questions, pass the 1z0-071 exam: https://www.pass4itsure.com/1z0-071.html (Q&As: 272). Boost exam skills Share 1z0-071 pdf and 1z0-071 Youtube videos for free


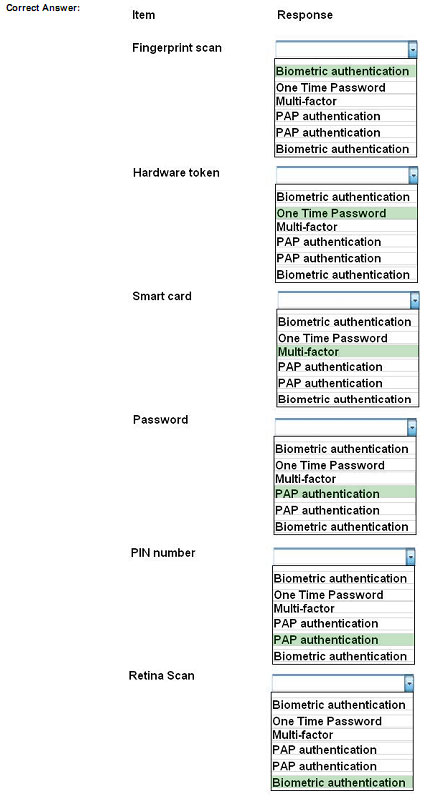
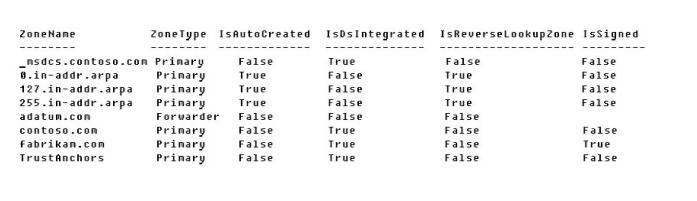
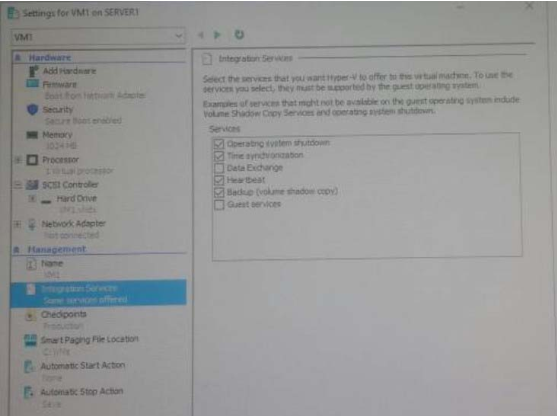
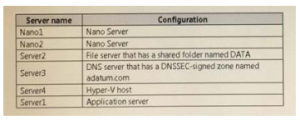
 After earning a prerequisite certification, learners must take one additional exam to earn the MCSE: Cloud Platform and Infrastructure certification which, like all expert-level certifications under Microsoft’s new certification structure, allows learners to choose from a pool of exams to customize a certification to their needs. Learners must pass one of the following exams to earn the MCSE 70-744 dumps certification:
After earning a prerequisite certification, learners must take one additional exam to earn the MCSE: Cloud Platform and Infrastructure certification which, like all expert-level certifications under Microsoft’s new certification structure, allows learners to choose from a pool of exams to customize a certification to their needs. Learners must pass one of the following exams to earn the MCSE 70-744 dumps certification: